Manage Computers
- Click 'Administration' > 'Authentication Configuration' > 'User Management' > 'Computer Names'
- The 'Computer Names' area lets you add endpoints to Comodo SWG. You can then include the endpoints in a policy ('Configuration' > 'Policy')
- Note – 'Computer Names' is only visible if you selected 'Hosted DB' method for user authentication. Click 'Administration' > 'Authentication Configuration' > 'Authentication Settings' to view/change this setting. Click here for more information about user authentication methods.
- Policies are prioritized top-to-bottom according to the list in 'Configuration' > 'Policy'.
- In the event of a conflict between policies over a security setting, the setting in the policy nearer the top of the list will prevail.
- You can change policy priority in the 'Policy Order' drop-down when editing a policy:
- Click 'Configuration' > 'Policy'
- Locate the policy whose priority you want to change and click the 'Edit' button on the right.
- Choose the priority with the 'Priority Order' drop-down. See 'Apply Policies to Network' section for more details.
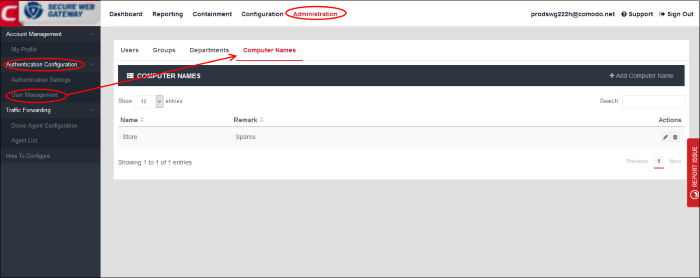
From the 'Computers Name' interface, you can:
- Click 'Computer Names' then 'Add Computer Name' at top-right
- This opens the 'Add Computer Name' dialog:
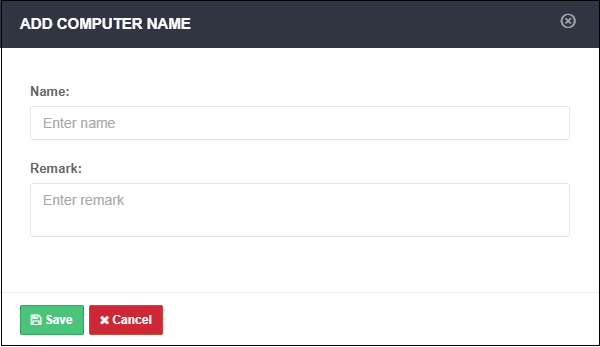
- Name - Create the label for the computer
- Remark - Provide appropriate comments for the computer
- Click 'Save'
The computer is added to the computer names area:
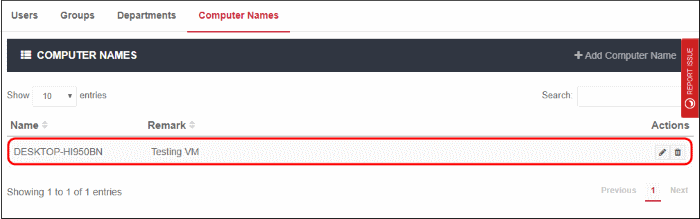
You can now deploy policies to the endpoint as required. See 'Applying Policies to Networks' to know how to deploy polices.
- Click the edit icon beside the computer name
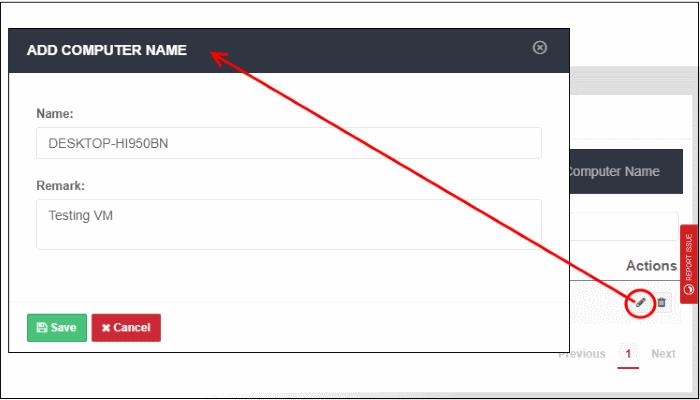
- Update the details as required. The process is similar to adding a computer explained above.
- Click 'Save' to apply your changes.
If the computer is applied any
policies, the changes done here will also be reflected in the Policy
List interface.
- Click the trash can icon beside the computer that you want to remove from the list. Note – you cannot delete a computer that has a policy assigned to it.
- Click 'OK' in the confirmation dialog.



