Rules
Administrators can create rules to filter inbound mails based on sender, recipient, source and relay/MTA server, subject line, attachments and so on. There are three types of filtering rules:
- Blacklist rule - Blocks inbound mails based on one or more filter criteria. Criteria include sender, recipient, mail servers/relays and specific subject line.
- Whitelist rule - Allows mails to pass through, without security checks, based on one or more filter criteria. Criteria include sender, recipient, mail servers/relays and specific subject line.
- Forward rule - Forwards mails based on one or more filter criteria, to a set email address. Criteria include sender, recipient, mail servers/relays and specific subject line.
For example, you can create rules to block all mails from a specific mail server, allow all mails from a specific sender to a specific recipient, forward all mails containing a specific text string in the subject line and so on.
Open the 'Create Rule' interface
- In the left-hand menu, click 'Domain Rules' > 'Create Rule'
- The 'Create Rule' interface will open:
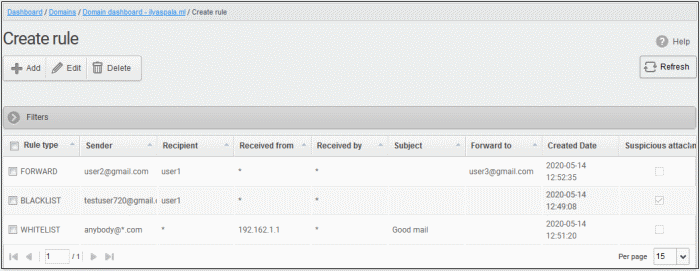
|
Column Header |
Description |
|---|---|
|
Rule Type |
Indicates whether the rule is for Blacklisting, whitelisting or forwarding. |
|
Sender |
The sender whose mails are intercepted by the rule. |
|
Recipient |
The recipient at the domain, whose mails are intercepted by the rule. |
|
Received From |
All mails sent from the external mail server indicated in this field will be intercepted by the rule. |
|
Received by |
All mails which are relayed by the servers which were indicated in this field will be intercepted by the rule. |
|
Subject |
Mails containing subject line indicated in this field will be intercepted by the rule. |
|
Forward to |
Indicates the email address to which the mails satisfying the conditions are forwarded. (Applies only to Forward Rules.) |
| Created date | The date and time the rule was added |
|
Suspicious attachment |
Indicates whether the rule should apply only to mails containing suspicious attachments. |
- Click any column header to sort rules in the ascending/descending order of the entries in that column. Does not apply to the 'Suspicious attachment' column header.
Use filters to search rules
- Click anywhere on the 'Filters' stripe to open the filters area.
- Choose the filter by which you want to search from the first drop-down, then a condition in the 2nd text box. Some filters have a third box for you to type a search string.
- Click ‘Apply Filter’.
You can filter results by the following parameters:
- Rule Type – Select the rule type (column 3) and the condition in column 2
- Sender – Type the sender's email address in the text box (column 3) and select the condition in column 2
- Recipient - Type the recipient's email address in the text box (column 3) and select the condition in column 2
- Received from - Type the hostname or IP address of external mail server in the text box (column 3) and select the condition in column 2
- Received by - Type the hostname or IP address of internal mail server in the text box (column 3) and select the condition in column 2
- Subject - Enter mail subject in the text box (column 3) and select the condition in column 2
- Forward to – Type the forward email address in the text box (column 3) and select the condition column 2
- Suspicious attachment rule - Filter suspicious attachment rules based on their enabled / disabled statuses
- Click anywhere on the 'Filters' tab to close the filters area. Click the 'Refresh' button to remove filters.
- You
can add multiple filters to the same search by clicking
 .
.
Create a new mail filter rule
- Click the 'Add' button.
- This will open the 'Add blacklist rule' dialog:
- Suspicious attachment rule
- By default, all mails containing suspicious attachments will be quarantined by CASG.
- A 'Suspicious attachment rule' lets you define specific actions if a malicious attachment is found in a mail.
- For example, you may want mails with a suspicious attachment from a specific sender, addressed to a particular recipient to be forwarded to a certain email address.
- Note. Enabling 'Suspicious attachment rule' means the rule only applies to mails which meet your conditions AND contain a suspicious attachment. It will not intercept mails which meet the conditions but do not contain a suspicious attachment.
- Rule type - Select the rule type. The available options are:
- BLACKLIST – All mails with fields satisfying the parameters entered in the options below, will be blocked.
- WHITELIST - All mails with fields satisfying the parameters entered in the options below, will be passed without security checks.
- FORWARD - All mails with fields satisfying the parameters entered in the options below, will be forwarded to the email address entered in the 'Forward email' field.
- Sender – Enter the email address of the sender, mails sent by whom are to be intercepted by the rule. You can use wildcard characters (*, ?) to enter username/domain name in part, so that all mails containing sender address with partial text entered in this field will be intercepted. For example, entering '*@hell.com' intercepts mails from all users from the domain name 'hell.com', entering 'evilspirit@*', processes all mails with sender name 'evilspirit' from any domain and entering *@* intercepts all the mails with parameters entered in the fields below.
- Recipient - Enter the username part of the email address of the recipient, mails sent to whom are to be intercepted by the rule. The domain name part will be auto-populated with the domain name from which the rule is created. You can use wildcard characters (*, ?) to enter username in part, so that all mails containing 'To' address with partial text entered in this field will be intercepted.
- Received from – Enter the hostname or IP address of the external mail server, mails sent from which, are to be intercepted by the rule. You can use wildcard characters (*, ?) to enter server name in part. For example, entering 'mailxxx*' will intercept all mails that contain “mailxxx” in part in the 'Received From' field of the mail header. To specify all sender mail servers, enter just the wildcard character.
- Received by - Enter the primary relay of the sending server or the MTA, mails sent through which, are to be intercepted by the rule. You can use wildcard characters (*, ?) to enter server name in part. For example, entering 'mailyyy*' will intercept all mails that contain “mailyyy” in part in the 'Received By' field of the mail header. To specify all mail servers, enter just the wildcard character.
- Subject - Enter keywords that you want the rule to search for in the subject lines of emails. The rule will apply if any of these words are found. Please note the search sub-string may match values in the middle of the word. Leading and trailing spaces will be trimmed.
- Forward email – This field is available only for 'FORWARD' rule. Enter the email address to which the emails containing values in the email header as configured in the fields above are to be forwarded.
- Click 'Save' to add the rule to the list of rules.
Edit a rule
- Select the rule to be edited and click the 'Edit' button from the top.
- Edit the values in the fields as required and click 'Save'.
Remove a rule
- Select the rule you want to remove and click the 'Delete' button.
A confirmation dialog will appear.
- Click
'OK' to remove the rule.



