Advanced Settings
Comodo Firewall features advanced detection settings to help protect your computer against common types of denial of service (DoS) attack. When launching a denial of service or 'flood' attack, an attacker bombards a target machine with so many connection requests that your computer is unable to accept legitimate connections, effectively shutting down your web, email, FTP or VPN server.
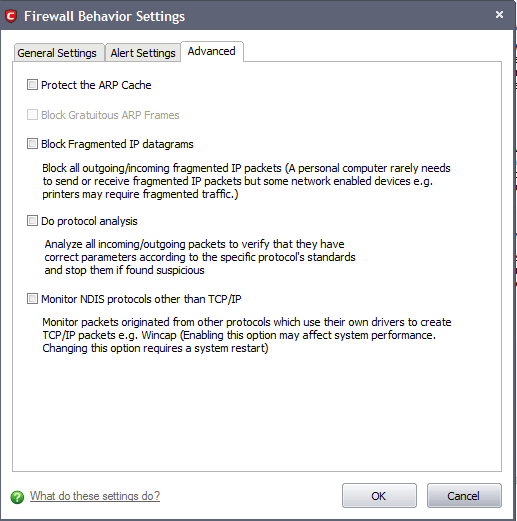
-
Protect the ARP Cache - Checking this option makes Comodo Firewall to start performing stateful inspection of ARP (Address Resolution Protocol) connections. This blocks spoof ARP requests and protects your computer from ARP cache poisoning attacks (Default = Disabled).
The ARP Cache (or ARP Table) is a record of IP addresses stored on your computer that is used to map IP addresses to MAC addresses. Stateful inspection involves the analysis of data within the lowest levels of the protocol stack and comparing the current session to previous ones in order to detect suspicious activity.
Background - Every device on a network has two addresses: a MAC (Media Access Control) address and an IP (Internet Protocol) address. The MAC address is the address of the physical network interface card inside the device, and never changes for the life of the device (in other words, the network card inside your PC has a hard coded MAC address that it keeps even if you install it in a different machine.) On the other hand, the IP address can change if the machine moves to another part of the network or the network uses DHCP to assign dynamic IP addresses. In order to correctly route a packet of data from a host to the destination network card it is essential to maintain a record of the correlation between a device's IP address and it's MAC address. The Address Resolution Protocol performs this function by matching an IP address to its appropriate MAC address (and vice versa). The ARP cache is a record of all the IP and MAC addresses that your computer has matched together.
Hackers can potentially alter a computer's ARP cache of matching IP/MAC address pairs to launch a variety of attacks including, Denial of Service attacks, Man in the Middle attacks and MAC address flooding and ARP request spoofing. It should be noted, that a successful ARP attack is almost always dependent on the hacker having physical access to your network or direct control of a machine on your network - therefore this setting is of more relevance to network administrators than home users.
-
Block Gratuitous ARP Frames - A gratuitous ARP frame is an ARP Reply that is broadcast to all machines in a network and is not in response to any ARP Request. When an ARP Reply is broadcast, all hosts are required to update their local ARP caches, whether or not the ARP Reply was in response to an ARP Request they had issued. Gratuitous ARP frames are important as they update your machine's ARP cache whenever there is a change to another machine on the network (for example, if a network card is replaced in a machine on the network, then a gratuitous ARP frame informs your machine of this change and requests to update your ARP cache so that data can be correctly routed). Enabling this setting helps to block such requests - protecting the ARP cache from potentially malicious updates (Default = Disabled).
-
Block Fragmented IP datagrams - When a connection is opened between two computers, they must agree on a Maximum Transmission Unit (MTU). IP Datagram fragmentation occurs when data passes through a router with an MTU less than the MTU you are using i.e when a datagram is larger than the MTU of the network over which it must be sent, it is divided into smaller 'fragments' which are each sent separately. Fragmented IP packets can create threats similar to a DOS attack. Moreover, these fragmentations can double the amount of time it takes to send a single packet and slow down your download time.
Comodo Firewall is set by default to block fragmented IP datagrams i.e the option Block Fragmented IP datagrams is checked by default.
-
Do protocol analysis - Protocol Analysis is key to the detection of fake packets used in denial of service attacks. Checking this option means Comodo Firewall checks every packet conforms to that protocols standards. If not, then the packets are blocked (Default = Disabled).
-
Monitor NDIS protocols other than TCP/IP - This forces Comodo Firewall to capture the packets belonging to any other protocol driver than TCP/IP. Trojans can potentially use their own protocol driver to send/receive packets. This option is useful to catch such attempts. This option is disabled by default: because it can reduce system performance and may be incompatible with some protocol drivers (Default = Disabled).
Comodo Internet Security User Guide | © 2012 Comodo Security Solutions Inc. | All rights reserved



