Sandbox Settings
The Sandbox Settings area allows you to configure the security level and the overall behavior of the sandbox. To access the Sandbox Settings interface, click ‘Defense + Settings’ then select the ‘Sandbox Settings’ tab. If you would like some background information on the sandbox before changing these settings then please see section The Sandbox -An Introduction.
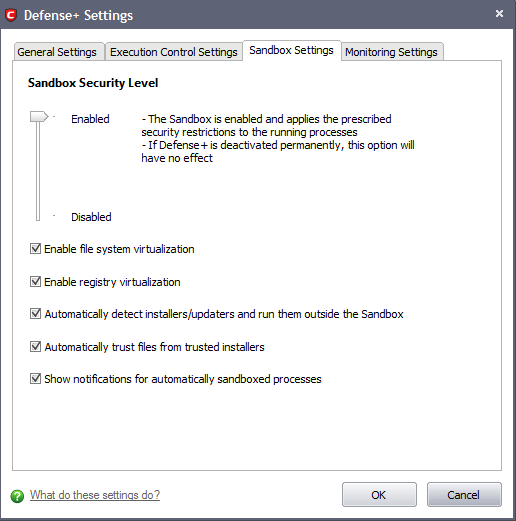
Sandbox Security Level Slider
The Security Level slider in the Settings interface allows you to switch the Sandbox between Enabled (Default) and Disabled states. The programs included in the Sandbox is executed with the set restrictions only if the Sandbox is in Enabled state. If disabled, the programs is run normally without any restrictions. The Sandbox is disabled irrespective of the settings in this slider, if Defense+ is permanently deactivated in the General Settings from the Defense+ Settings interface.
Check Boxes
Enable file system virtualization - The sandboxed applications are not permitted to modify the files in your 'real' file system. Enabling file system virtualization instructs the Sandbox to create a virtual file system in your system. The sandboxed applications write any data only into the created virtual file system, instead of affecting and potentially causing damage to your real file system. If you disable this option, the sandboxed applications may not function correctly because they are not able to create the entries that they need too (Default=Enabled).
|
Note for advanced users: The virtual file system is created inside the Sandbox working folder (e.g. c:\sandbox\) to execute the applications within this file system. If you disable this option here, the virtual file system is not created even if you have enabled file system virtualization for individual applications within the Sandbox. |
Enable registry virtualization -The sandboxed applications are not permitted to access and modify the entries in your 'real' Window's Registry hives. Enabling registry virtualization instructs the Sandbox to create a virtual registry hive in your system. The sandboxed applications write any entries pertaining to them only into the created registry hive, instead of affecting and potentially causing damage to your real registry hives. If you disable this option, the sandboxed applications may not function correctly because they are not able to create the entries that they need too (Default=Enabled).
|
Note for advanced users: The virtual file system is created inside the Sandbox working folder (e.g. c:\sandbox\) to execute the applications within this file system. If you disable this option here, the virtual file system is not created even if you have enabled file system virtualization for individual applications within the Sandbox. |
The table below explains the precedence of the file system virtualization and registry virtualization settings made through this interface and those through Computer Security Policy > Always Sandbox > Add > Always Sandbox > Advanced Settings.
|
Sandbox Settings |
Always Sandbox > Advanced Settings |
Is the setting enabled for the specific application? |
|---|---|---|
|
Yes |
Yes |
Yes |
|
Yes |
No |
No |
|
No |
Yes |
No |
|
No |
No |
No |
Automatically detect the installers / updaters and run them outside the Sandbox - On execution of an Installer or an Updater, the application is run outside the Sandbox. Select this option only if you are going to run installers / updaters from trusted vendors (Default=Enabled).
Automatically trust the files from the trusted installers - Files that are generated by trusted installers are also trusted. This means that they will not be sandboxed (Default=Enabled).
Show notifications for automatically sandboxed processes - By default, CIS will display an alert whenever it runs an unknown application in the sandbox. Use this control to enable or disable these alerts (Default = Enabled).
Click 'OK' for your settings to take effect.
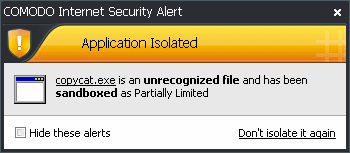
Additional information:
- See 'Sandbox Alerts' for a explanation of the options available at a Sandbox alert.
- See 'Unknown Files: The Sand-boxing and Scanning Processes' to understand the decision making process behind why CIS chooses to sandbox certain applications.
Comodo Internet Security User Guide | © 2012 Comodo Security Solutions Inc. | All rights reserved



