Quarantined Items
The quarantine facility removes and isolates suspicious files into a safe location before analyzing them for possible infection. Any files transferred in this fashion are encrypted- meaning they cannot be run or executed. This isolation prevents infected files from affecting the rest of your PC. If a file cannot be disinfected, then it provides a reliable safe-house until the virus database is updated- neutralizing the impact of any new virus.
For adding executables to Quarantined items, refer to Antivirus Tasks > Run a Scan. You can also:
To view the list of Quarantined Items
-
Click 'Quarantined Items' from the main Antivirus Task Manager Screen.
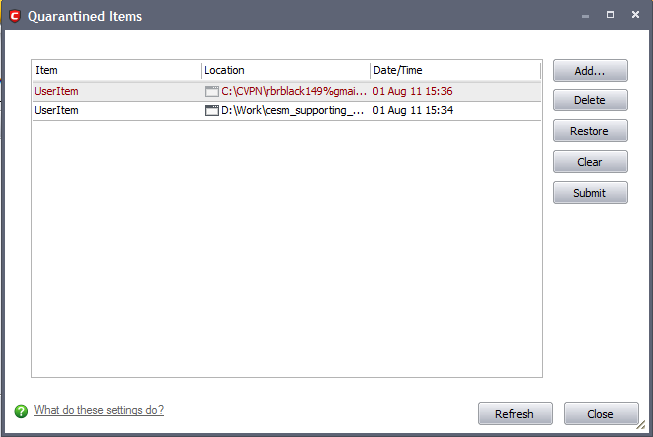
Column Descriptions
-
Item - Indicates which application or process propagated the event;
-
Location - Indicates the location where the application or the file is stored;
-
Date/Time - Indicates date and time, when the item is moved to quarantine.
Manually adding files as Quarantined Items
If you have a file, folder or drive that you suspect may contain a virus and not been detected by the scanner, then you have the option to isolate that item in quarantine.
To manually add a Quarantined Item
-
Click Add and select the file from Open dialog box.
To delete a quarantined item from the system
-
Select the item and Click 'Delete'.
This deletes the file from the system permanently.
To restore a quarantined item to its original location
-
Select the item and click 'Restore'.
If the restored item does not contain a malware, it operates as usual. But if it contains a malware, it is detected as a threat immediately, if the Real Time Scanning is enabled or during the next scan.
To remove all the quarantined items permanently
-
Click 'Clear'.
This deletes all the quarantined items from the system permanently.
To submit selected quarantined items to Comodo for analysis
-
Select the item from the list and click 'Submit'.
|
Note: Quarantined files are stored using a special format and do not constitute any danger to your computer. |
Comodo Internet Security User Guide | © 2012 Comodo Security Solutions Inc. | All rights reserved



