General Settings
Slider Options
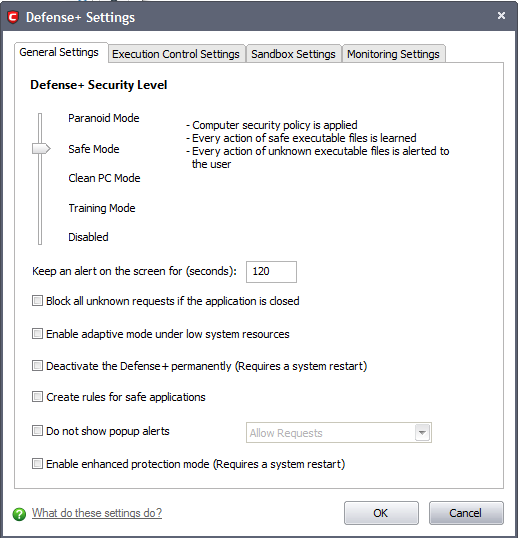
Comodo Internet Security allows you to customize the behavior of Defense+ by adjusting a Security Level slider to switch between preset security levels.
The choices available are: Paranoid Mode, Safe Mode, Clean PC Mode, Training Mode and Disabled. The setting you choose here are also to be displayed on the CIS summary screen.
-
Paranoid Mode: This is the highest security level setting and means that Defense+ monitors and controls all executable files apart from those that you have deemed safe. Comodo Internet Security does not attempt to learn the behavior of any applications - even those applications on the Comodo safe list and only uses your configuration settings to filter critical system activity. Similarly, the Comodo Internet Security does automatically create 'Allow' rules for any executables - although you still have the option to treat an application as 'Trusted' at the Defense+ alert. Choosing this option generates the most amount of Defense+ alerts and is recommended for advanced users that require complete awareness of activity on their system.
-
Safe Mode (Default): While monitoring critical system activity, Defense+ automatically learns the activity of executables and applications certified as 'Safe' by Comodo. It also automatically creates 'Allow' rules these activities, if the checkbox 'Create rules for safe applications' is selected. For non-certified, unknown, applications, you will receive an alert whenever that application attempts to run. Should you choose, you can add that new application to the safe list by choosing 'Treat this application as a Trusted Application' at the alert. This instructs the Defense+ not to generate an alert the next time it runs. If your machine is not new or known to be free of malware and other threats as in 'Clean PC Mode' then 'Safe Mode' is recommended setting for most users - combining the highest levels of security with an easy-to-manage number of Defense+ alerts.
-
Clean PC Mode: From the time you set the slider to 'Clean PC Mode', Defense+ learns the activities of the applications currently installed on the computer while all new executables introduced to the system are monitored and controlled. This patent-pending mode of operation is the recommended option on a new computer or one that the user knows to be clean of malware and other threats. From this point onwardsDefense+ alerts the user whenever a new, unrecognized application is being installed. In this mode, the files in 'My Pending Files' are excluded from being considered as clean and are monitored and controlled.
-
Training Mode: Defense+ monitors and learn the activity of any and all executables and create automatic 'Allow' rules until the security level is adjusted. You do not receive any Defense+ alerts in 'Training Mode'. If you choose the 'Training Mode' setting, we advise that you are 100% sure that all applications and executables installed on your computer are safe to run.
|
Tip: This mode can be used as the “Gaming Mode”. It is handy to use this setting temporarily when you are running an (unknown but trusted) application or Games for the first time. This suppresses all Defense+ alerts while Comodo Internet Security learns the components of the application that need to run on your machine and automatically create 'Allow' rules for them. Afterward, you can switch back to 'Safe Mode' mode). |
- Disabled: Disables Defense+ protection. All executables and applications are allowed to run irrespective of your configuration settings. Comodo strongly advise against this setting unless you are confident that you have an alternative intrusion defense system installed on your computer.
Checkbox Options
- Keep an alert on screen for maximum (n) seconds - Determines how long Comodo Internet Security shows a Defense+ alert without any user intervention. By default, the timeout is set at 120 seconds. You may adjust this setting to your own preference (Default = 120 seconds).
- Block all unknown requests if the application is closed - Selecting this option blocks all unknown execution requests if Comodo Internet Security is not running/has been shut down. This is option is very strict indeed and in most cases should only be enabled on seriously infested or compromised machines while the user is working to resolve these issues. If you know your machine is already ‘clean’ and are looking just to enable the highest CIS security settings then it is OK to leave this box unchecked. (Default = Disabled).
- Enable adaptive mode under low system resources - Very rarely (and only in a heavily loaded system), low memory conditions might cause certain CIS functions to fail. With this option enabled, CIS will attempt to locate and utilize memory using adaptive techniques so that it can complete its pending tasks. However, the cost of enabling this option may be reduced performance in even lightly loaded systems (Default = Disabled).
- Deactivate Defense+ permanently (Requires a system restart)- Shuts down the Defense+ Host Intrusion element of Comodo Internet Security PERMANENTLY. The firewall and antivirus are not affected and continues to protect your computer even if you deactivate Defense+. Comodo does not recommend users close Defense+ unless they are sure they have alternative Intrusion Prevention Systems installed (Default = Disabled).
- Create rules for safe applications - Automatically creates rules for safe applications in Computer Security Policy (Default = Disabled).
|
Note: Defense+ trusts the applications if:
|
Enabling this checkbox instructs CIS to begin learning the behavior of safe applications so that it can automatically generate the 'Allow' rules. These rules are listed in the Computer Security Policy interface. The Advanced users can edit / modify the rules as they wish.
| Background Note: Prior to version 4.x , CIS would automatically add an allow rule for ‘safe’ files to the rules interface. This allowed advanced users to have granular control over rules but could also lead to a cluttered rules interface. The constant addition of these ‘allow’ rules and the corresponding requirement to learn the behavior of applications that are already considered ‘safe’ also took a toll on system resources. In version 4.x and above, ‘allow’ rules for applications considered ‘safe’ are not automatically created – simplifying the rules interface and cutting resource overhead with no loss in security. Advanced users can re-enable this setting if they require the ability to edit rules for safe applications (or, informally, if they preferred the way rules were created in CIS version 3.x). |
- Do not show popup alerts - This option allows you to configure whether or not to show defense alerts when malware is encountered. Choosing ‘Do not show popup alerts’ will minimize disturbances but at some loss of user awareness. If you choose not to show alerts then you have a choice of default responses that CIS should automatically take – either ‘Block Requests’ or 'Allow Requests’. (Default = Disabled)
- Enable enhanced protection mode (Requires a system restart) - On 64 bit systems, enabling this mode will activate additional host intrusion prevention techniques in Defense+ to countermeasure extremely sophisticated malware that tries to bypass regular countermeasures. Because of limitations in Windows 7 x64, some HIPS functions in previous versions of CIS could theoretically be bypassed by malware. Enhanced Protection Mode implements several patent-pending ways to improve HIPS in Defense+. (Default=Disabled)
Comodo Internet Security User Guide | © 2012 Comodo Security Solutions Inc. | All rights reserved



