Execution Control Settings
Image Execution Control is an integral part of the Defense+ engine. If your Defense+ Security Level is set to 'Training Mode' or 'Clean PC Mode', then it is responsible for authenticating every executable image that is loaded into the memory.
Comodo Internet Security calculates the hash of an executable at the point it attempts to load into memory. It then compares this hash with the list of known/recognized applications that are on the Comodo safe list. If the hash matches the one on record for the executable, then the application is safe. If no matching hash is found on the safe list, then the executable is 'unrecognized' and you will receive an alert.
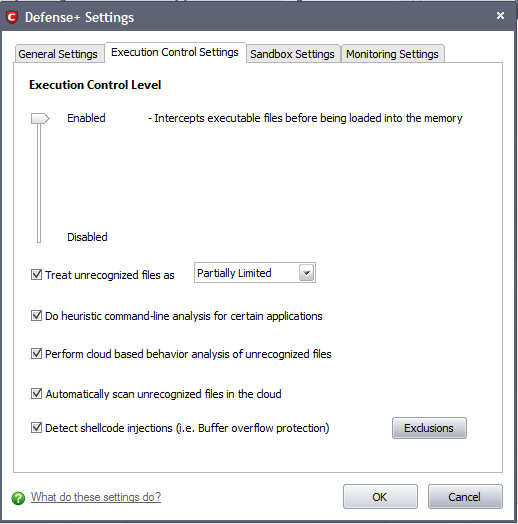
This area allows you to quickly determine how proactive the monitor should be and which types of files it should check.
|
Background note: In this context, an 'image' means an 'Executable Image'. An executable image is a variation on file compression, such as ZIP or RAR files. For example, most program installers are contained in executable images. |
Image Execution Control Level Slider
The control slider in the Settings interface allows you to switch the Image Execution settings between Enabled(Default) and Disabled states. The Image Execution Control is disabled irrespective of the settings in this slider, if Defense+ is permanently deactivated in the General Settings from the Defense+ Settings interface.
-
Enabled (Default) - This setting instructs Defense+ to intercept all the files before they are loaded into memory and also Intercepts pre-fetching/caching attempts for the executable files.
-
Disabled - No execution control is applied to the executable files.
Check Boxes
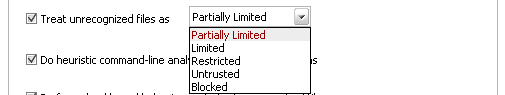
Treat unrecognized files as – This has five options and the unrecognized files will be run as per the option selected.
-
Partially Limited (Default) - The application is allowed to access all the Operating system files and resources like clipboard. Modification of protected files/registry keys is not allowed. Privileged operations like loading drivers or debugging other applications are also not allowed.
-
Limited - Only selected operating system resources can be accessed by the application. The application is not allowed to execute more than 10 processes at a time and is run with out Administrator account privileges.
-
Restricted - The application is allowed to access very few operating system resources. The application is not allowed to execute more than 10 processes at a time and is run with very limited access rights.
|
Note: Some of the applications like computer games may not work properly under this setting. |
- Untrusted - The application is not allowed to access any of the Operating system resources. The application is not allowed to execute more than 10 processes at a time and is run with very limited access rights.
|
Note: Some of the applications that require user interaction may not work properly under this setting. |
- Blocked – The application is not allowed to run at all.
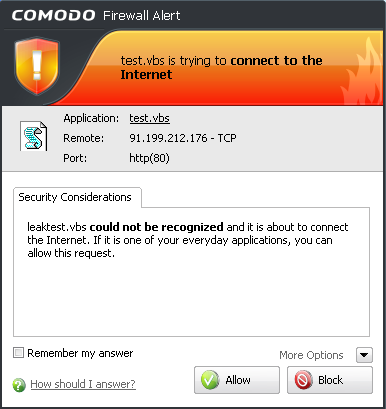
Do heuristic command-line analysis for certain applications - Selecting this option instructs Comodo Internet Security to perform heuristic analysis of programs that are capable of executing code such as visual basic scripts and java applications. Example programs that are affected by enabling this option are wscript.exe, cmd.exe, java.exe and javaw.exe. For example, the program wscipt.exe can be made to execute visual basic scripts (.vbs file extension) via a command similar to “wscipt.exe c:teststest.vbs”. If this option is selected, CIS detects c:teststest.vbs from the command line and applies all security checks based on this file. If test.vbs attempts to connect to the internet, for example, the alert will state ‘c:teststest.vbs’ is attempting to connect to the internet (Default=Enabled).
|
Background note: ‘Heuristics’ describes the method of analyzing a file to ascertain whether it contains codes typical of a virus. Heuristics is about detecting virus-like behavior or attributes rather than looking for a precise virus signature that matches a signature on the virus blacklist. This helps to identify previously unknown (new) viruses. |
Perform cloud based behavior analysis of unrecognized files – When checked, any file that is marked as unrecognized and is sent to the Comodo Instant Malware Analysis (CIMA) server for behavior analysis. Each file is executed in a virtual environment on Comodo servers and tested to determine whether it contains any malicious code. The results will be sent back to your computer in around 15 minutes. Comodo recommends users leave this setting enabled (Default=Enabled).
More details. The behavior analysis system is a cloud based service that is used to help determine whether an unknown file is safe or malicious. Once submitted to the system, the unknown executable will be automatically run in a virtual environment and all activities, host state changes and network activity will be recorded. The list of behaviors recorded during this analysis can include information about processes spawned, files and registry keys modified, network activity, and other changes. If these behaviors are found to be malicious then the signature of the executable is automatically added to the antivirus black list. If no malicious behavior is recorded then the file is placed into 'Unrecognized Files' (for execution within the sandbox) and will be submitted to our technicians for further checks. The behavior analysis system takes around 15 minutes to report its results back to CIS. If the executable is deemed a threat then it will be automatically quarantined or deleted. This threat report is also used to update the global black list databases and therefore benefit all CIS users.
Automatically scan unrecognized files in the cloud – Selecting this option will automatically submit unrecognized files to our File Lookup Server to check whether or not they are on the master Comodo white list or black-list (White list = files that are known to be safe. Black list = files that are known to be malware) and the files are rated accordingly. The important features of the cloud based scanning are:
-
Cloud based Whitelisting: Safe files and trusted vendors and trusted publishers can be easily identified;
-
Cloud based Antivirus: Malicious files can be detected even if the users do not have an up-to-date local antivirus database or a local antivirus database at all;
-
Cloud Based Behavior Analysis: Zero-day malware can be instantly detected by Comodo’s cloud based behavior analysis system, CIMA.
The cloud scanning, complemented by automatic sandboxing and application isolation technologies, is very extremely fast and powerful in preventing PC infection even without a traditional antivirus signature database while keeping the user interaction at minimal levels.
Comodo recommends users leave this setting enabled (Default = Enabled).
Detect shellcode injections (i.e. Buffer overflow protection) - Enabling this setting turns-on the Buffer over flow protection.
A buffer overflow is an anomalous condition where a process/executable attempts to store data beyond the boundaries of a fixed-length buffer. The result is that the extra data overwrites adjacent memory locations. The overwritten data may include other buffers, variables and program flow data and may cause a process to crash or produce incorrect results. They can be triggered by inputs specifically designed to execute malicious code or to make the program operate in an unintended way. As such, buffer overflows cause many software vulnerabilities and form the basis of many exploits.
Turning-on buffer overflow protection instructs the Comodo Internet Security to raise pop-up alerts in every event of a possible buffer overflow attack. You can allow or deny the requested activity raised by the process under execution depending on the reliability of the software and it's vendor. Click here for more details on the alerts.
Comodo recommends users leave this setting enabled (Default = Enabled).
To exclude some of the file types from being monitored under Detect Shellcode injections.
1. Click on the 'Exclusions' button.
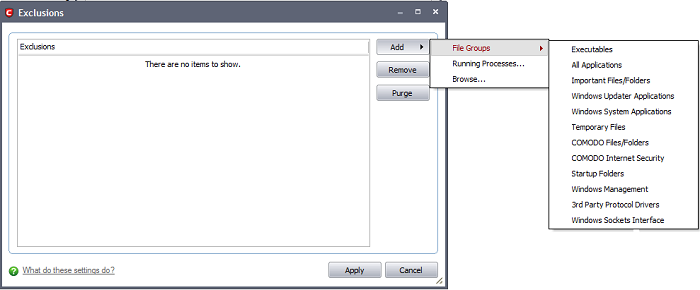
2. Click 'Add' to include file groups or processes to the Exclusions list. Click here for an outline of the options available when adding file types.
3. Click 'Remove' to remove selected entries from the exclusions list
4. Click 'Purge' to remove invalid entries (programs that are not present or uninstalled from your computer) automatically.
|
Note: These settings are recommended for advanced users only. |
5. Click 'Apply' to implement your settings.
Comodo Internet Security User Guide | © 2012 Comodo Security Solutions Inc. | All rights reserved



