Setting up Defense+ for Maximum Security and Usability
This page explains on configuring the Host Intrusion Prevention System (HIPS) component of CIS to provide maximum security from the malicious programs that try to execute from within your system and to protect your system from data theft, computer crashes and system damage by preventing most types of buffer overflow attacks, prevent possible attacks from root-kits, inter-process memory injections, key-loggers and more.
To configure Defense+
-
Click 'Defense+' from the top navigation and click 'Defense+ Settings' from Defense+ Tasks interface. The Defense+ Settings interface will open.
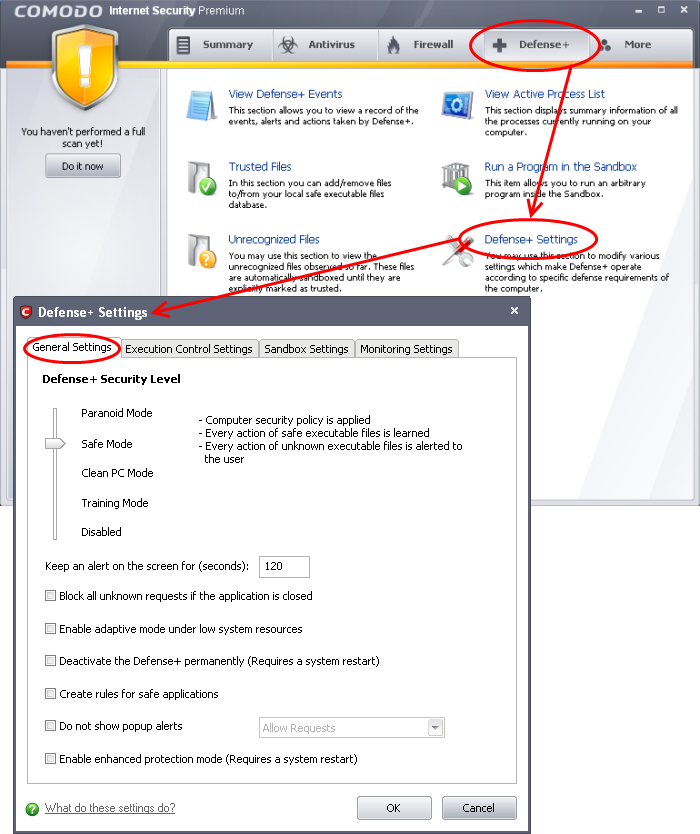
-
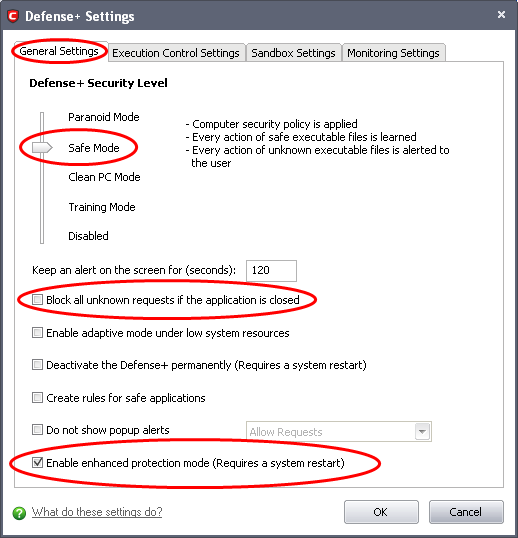
Click the 'General Settings' tab and make the following settings:
-
Move the Defense+ security Level slider to Safe Mode; Refer to Defense+ Settings > General Settings for more details on the Security Levels.
-
Optional – Enable 'Block all unknown requests if the application is closed'. Selecting this option blocks all unknown execution requests if Comodo Internet Security is not running/has been shut down. This is option is very strict indeed and in most cases should only be enabled on seriously infested or compromised machines while the user is working to resolve these issues. If you know your machine is already ‘clean’ and are looking just to enable the highest CIS security settings then it is OK to leave this box unchecked.
-
If you are using a 64-bit system, in order to maximize the security, it is important to select 'Enable enhanced protection mode (Requires a system restart)' – Enabling this mode will activate additional host intrusion prevention techniques in Defense+ to countermeasure extremely sophisticated malware that tries to bypass regular countermeasures.
Because of limitations in Windows 7 x64, some HIPS functions in previous versions of CIS could theoretically be bypassed by malware. Enhanced Protection Mode implements several patent-pending ways to improve HIPS in Defense+
-
Make sure that the check box 'Deactivate the Defense+ permanently' is not selected.
-
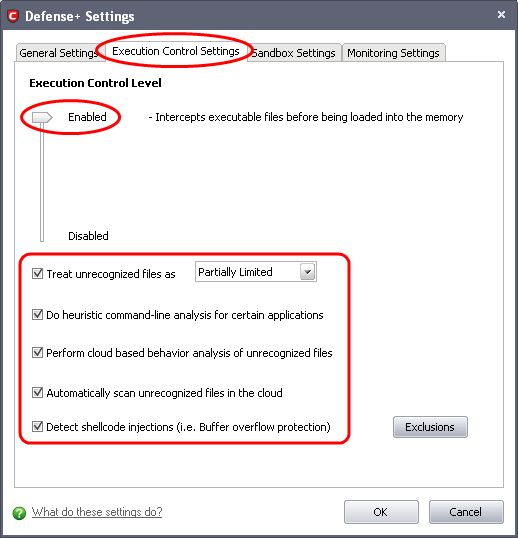
Click the Execution Control Settings tab and make the following settings:
-
Move the Execution Control Level slider to Enabled. Refer to Defense+ Settings > Execution Control Settings for more details.
-
Make sure that the check box Treat unrecognized files as is selected and choose 'Partially Limited' from the drop-down menu.
-
Make sure that all the check boxes:
-
Do heuristic command-line analysis for certain applications;
-
Perform cloud based behavior analysis of unrecognized files;
-
Automatically scan unrecognized files in the cloud; and
-
Detect shellcode injections (i.e. Buffer overflow protection).
-
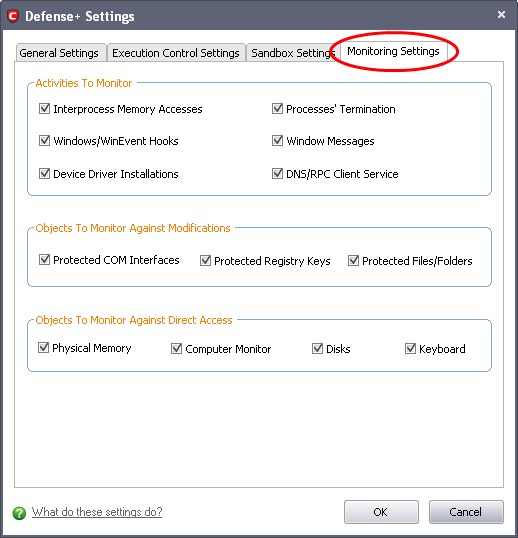
Click the 'Monitoring Settings' tab and make sure that all the check boxes are selected.
-
Click 'OK' for your settings to take effect.
… are selected.
Refer to Defense+ Settings > Execution Control Settings for more details.
Comodo Internet Security User Guide | © 2012 Comodo Security Solutions Inc. | All rights reserved



