View Defense+ Events
Comodo Internet Security records a history of all actions taken by Defense+. These can be viewed by clicking 'View Defense+ Events' from the 'Defense+ Tasks' area. Defense+ ‘Events’ are generated and recorded for various reasons. Examples include changes in Defense+ settings, when an application or process attempts to access restricted areas or when an action occurs that contravenes your Computer Security Policy.
By default, CIS stores the log file in Support DataBase (SDB) format as cislogs.sdb file which is located in C:\Documents and Settings\All Users\Application Data\Comodo\Firewall Pro. Logs stored in this file can be extracted by using a suitable application. Logs can also be exported to html by clicking ‘More.. > File > Export’.
To view a log of Defense+ Events
- Click 'View Defense+ Events' from the Defense+ Tasks interface.
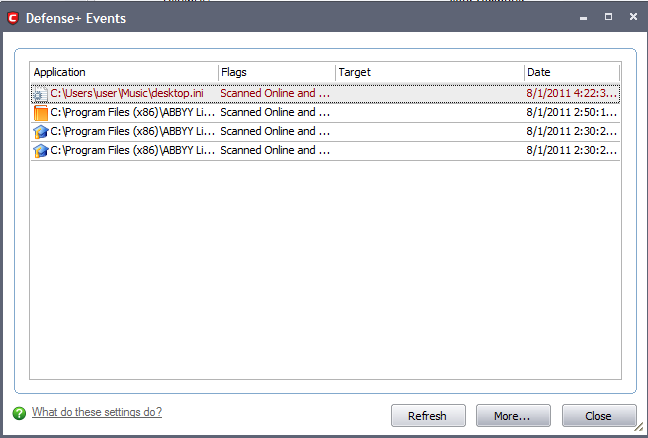
Column Descriptions
-
Application - Indicates which application or process propagated the event. If the application has no icon, the default system icon for executable files are used.
-
Flags - Indicates flags set for the kinds of actions against the event triggered by the file.
-
Target - Represents the location of the target file.
-
Date/Time - Contains precise details of the date and time of the access attempt.
-
Click Refresh to reload and update the displayed list, to include all events generated since the time you first accessed the 'Defense+ Events' area.
-
Click 'More ...' to load the full, Comodo Internet Security Log Viewer module. See below for more details on this module.
Log Viewer Module
Click 'More' to load the full, Comodo Internet Security Log Viewer module. Alternatively, this module can be opened by double-clicking the 'cfplogvw' exe file that is stored in the installation path of the CIS application. Usually the path is C:\Program Files\COMODO\COMODO Internet Security.
This window contains a full history of logged events of Firewall, Defense+ and Antivirus modules. It also allows you to build custom log files based on specific filters and to export log file for archiving or troubleshooting purposes.
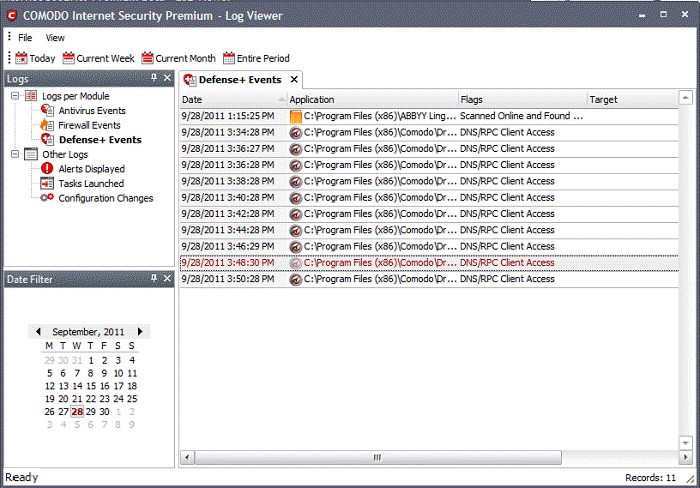
The Log Viewer Module is divided into two sections. The left hand panel displays a set of handy, pre-defined time Filters for Firewall, Defense+ and Antivirus event log files. The right hand panel displays the actual events that were logged for the time period you selected in the left hand panel (or the events that correspond to the filtering criteria you selected).
Comodo Internet Security allows you to create custom views of all logged events according to user defined criteria.
Preset Time Filters:
Clicking on any of the preset filters in the top panel alters the display in the right hand panel in the following ways:
-
Today - Displays all logged events for today.
-
Current Week - Displays all logged events during the current week. (The current week is calculated from the Sunday to Saturday that holds the current date.)
-
Current Month - Displays all logged events during the month that holds the current date.
-
Entire Period - Displays every event logged since Comodo Internet Security was installed. (If you have cleared the log history since installation, this option shows all logs created since that clearance).
The example below shows an example display when the Defense+ Logs for 'Today' are displayed.
|
Note: The type of events logged by the Antivirus, Firewall and Defense+ modules of Comodo Internet Security differ from each other. This means that the information and the columns displayed in the right hand side panel change depending on which type of log you have selected in the top and left hand side panel. For more details on the data shown in the columns, see View Anti-virus Events or View Firewall Events. |
User Defined Filters:
Having chosen a preset time filter from the top panel, you can further refine the displayed events according to specific filters. The type of filters available for Firewall logs differ to those available for Defense+ logs. The table below provides a summary of available filters and their meanings:
|
Available Filters – Logs per Module |
||
|---|---|---|
|
Antivirus Filter |
Firewall Filters |
Defense+ Filters |
|
Action - Displays events according to the response (or action taken) by the Antivirus |
Action - Displays events according to the response (or action taken) by the firewall |
Application - Displays only the events propagated by a specific application |
|
Location - Displays only the events logged from a specific location |
Application - Displays only the events propagated by a specific application |
Flags - Displays events according to the response (or action taken) by Defense+ |
|
Malware Name - Displays only the events logged corresponding to a specific malware |
Destination IP address - Displays only the events with a specific target IP address |
Action - Displays events according to the response (or action taken) by Defense+ |
|
Status - Displays the events according to the status after the action taken. It can be either 'Success' or 'Fail' |
Destination Port - Displays only the events with a specific target port number |
Target - Displays only the events that involved a specified target application |
|
|
Direction - Indicates if the event was an Inbound or Outbound connection |
|
|
|
Protocol - Displays only the events that involved a specific protocol |
|
|
|
Source IP address - Displays only the events that originated from a specific IP address |
|
|
|
Source Port - Displays only the events that originated from a specific port number |
|
Creating Custom Filters
Custom Filters can be created through the Advanced Filter Interface. You can open the Advanced Filter interface either by using the View option in the menu bar or using the context sensitive menu.
-
Click View > Advanced Filter to open the ‘Advanced Filter’ configuration area.
Or
-
Right click on any event and select 'Advanced Filter' option to open the corresponding configuration area.
The ‘Advanced Filter’ configuration area is displayed in the top half of the interface whilst the lower half displays the Events, Alerts, Tasks or Configuration Changes that the user has selected from the upper left pane. If you wish to view and filter event logs for other modules then simply click log name in the tree on the upper left hand pane.
The Advanced Log filter displays different fields and options depending on the log type chosen from the left hand pane (Antivirus, Defense+, Firewall).
This section will deal with Advanced Event Filters related to ‘Defense+ Events’ and will also cover the custom filtering that can be applied to the ‘Other Logs’ (namely ‘Alerts Displayed’, ‘Tasks’ Launched’ and ‘Configuration Changes’).
Defense+ Events - Advanced Filters
To configure Advanced Filters for Defense+ events
-
Select ‘View > Advanced Filter’
-
Select ‘Defense+ Events’ under ‘Logs Per Module’
You have 3 categories of filter that you can add. Each of these categories can be further refined by either selecting or deselecting specific filter parameters or by the user typing a filter string in the field provided.
-
Click the ‘Add’ link when you have chosen the category upon which you wish to filter.
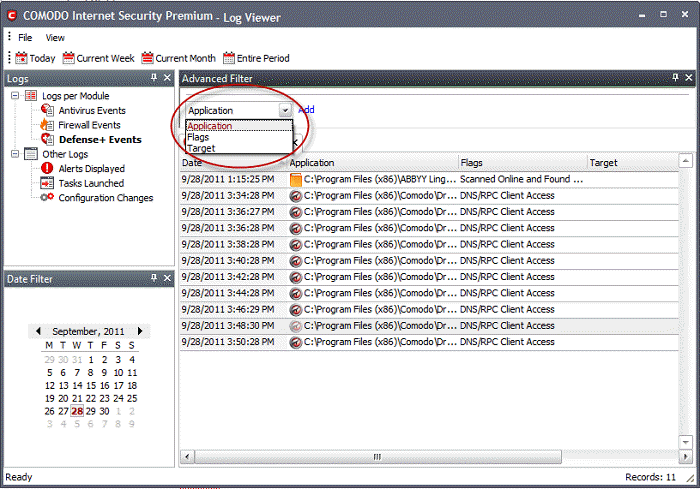
Following are the options available in the 'Add' drop down menu:
-
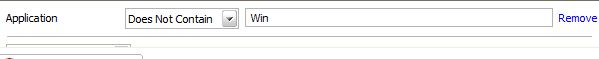
Application: Selecting the 'Application' option displays a drop-down field and text entry field.
-
Select 'Contains' or 'Does Not Contain' option from the drop-down menu.
-
Enter the text or word that needs to be filtered.
The filtered entries are shown directly underneath.
-
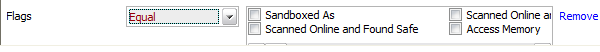
Flags: Selecting the 'Flags' option displays a drop down menu and a set of specific filter parameters that can be selected or deselected.
-
Select 'Equal' or 'Not Equal' option from the drop down menu. ‘Not Equal’ will invert your selected choice.
-
Now select the check-boxes of the specific filter parameters to refine your search. The parameter available are:
-
Sandboxed As
-
Scanned Online and Found Safe
-
Scanned Online and Found Malicious
-
Access Memory
-
Create Process
-
Terminate Process
-
Modify Key
-
Modify File
-
Direct Memory Access
-
Direct Disk Access
-
Direct Keyboard Access
-
Direct Monitor Access
-
Load Driver
-
Send Message
-
Install Hook
-
Access COM Interface
-
Execute Image
-
DNS/RPC Client Access
-
Change Defense+ Mode
-
Shellcode Injection
-
Block File
-
Suspicious
-
Hook
-
Alert Suppressed
The filtered entries are shown directly underneath.
-
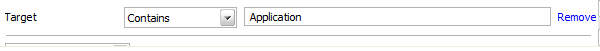
Target: Selecting the 'Target' option displays a drop-down menu and text entry field.
-
Select 'Contains' or 'Does Not Contain' option from the drop-down menu.
-
Enter the text or word that needs to be filtered.
The filtered entries are shown directly underneath.
|
Note: More than one filters can be added in the ‘Advanced Filter’ pane. After adding one filter type, the option to select the next filter type automatically appears. You can also remove a filter type by clicking the 'Remove' option at the end of every filter option. |
Other Logs – Advanced Filters
Refer to Antivirus Tasks Overview > View Antivirus Events > Log Viewer > Creating Custom Filters > Other Logs – Advanced Filters for the process of Creating Custom Filters for Alerts Displayed, Task Launched and Configuration Changes.
DateFilter
Click here to know more about Date Filter functionality.
Exporting log files is useful for archiving and troubleshooting purposes. There are two ways to export log files in the Log Viewer interface - using the context sensitive menu and via the 'File' menu option. After making your choice, you are asked to specify a name for the exported HTML file and the location you wish to save it to.
-
File Menu
Click 'File' Menu.
Move cursor to 'Export'
Click on anyone of 'Firewall Logs', 'Defense+ Logs', 'Antivirus Logs' and 'All', as required.
Firewall Logs - Exports the Firewall log that is currently being displayed in the right hand side panel.
Defense+ Logs - Exports the Defense+ log that is currently being displayed in the right hand side panel .
Antivirus Logs - Exports Antivirus log that is currently being displayed in the right hand side panel.
All - Exports ALL logs for ALL TIME for Firewall, Defense+ and Antivirus logs as a single HTML file.
Select the location where the log has to be stored in the 'Save Firewall Log as' window and click 'Save'.
-
Context Sensitive Menu
- Right click in the log display window to export the currently displayed log file to HTML.
You can export a custom view that you created using the available Filters by right clicking and selecting 'Export' from the context sensitive menu. Again, you are asked to provide a filename and save location for the file.
Comodo Internet Security User Guide | © 2012 Comodo Security Solutions Inc. | All rights reserved



