Setting Up The Firewall For Maximum Security And Usability
This page outlines the functions of Comodo's Firewall and helps you to set up a secure connection to the Internet.
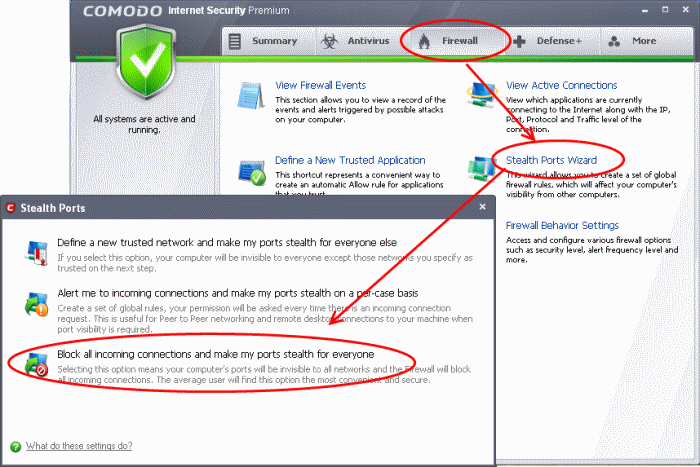
Stealth Ports Settings
Port Stealthing is a security feature whereby ports on an Internet connected PC are hidden from sight, sending no response to opportunistic port scans.
-
Click the ‘Firewall’ button along the top navigation
-
Click 'Stealth Ports Wizard' in Firewall Tasks menu
-
Select "Block All Incoming connections and make my ports stealth for everyone" to make computer's ports are invisible to all networks
-
Click 'Ok'.
Click here for more details on Stealth Port Wizard
Network Zones Settings
The Network Zones option allows you to configure the protection level for network connection to a Router/home network. (This is usually done automatically for you).
To view the configurations:
-
Click the 'Firewall' button along the top navigation
-
Click 'Network Security Policy' in Firewall Tasks menu
-
Click 'Network Zones' tab
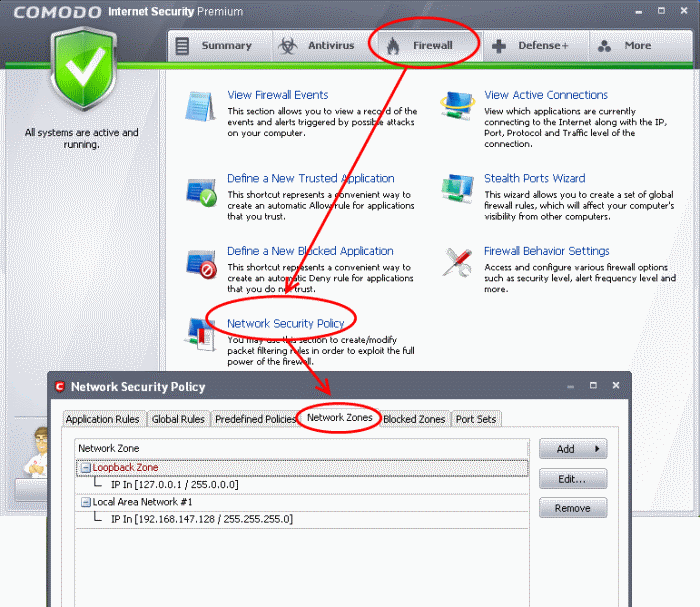
Check the Loopback zone and Local Area Network #1. In most cases, the loopback zone IP address should be 127.0.01/255.0.0.0
In most cases, the IP address of the auto detected Network zone should be 192.168.1.100/255.255.255.0 .
-
Check these addressees and click 'OK'.
Click here for more details on Network Zones settings
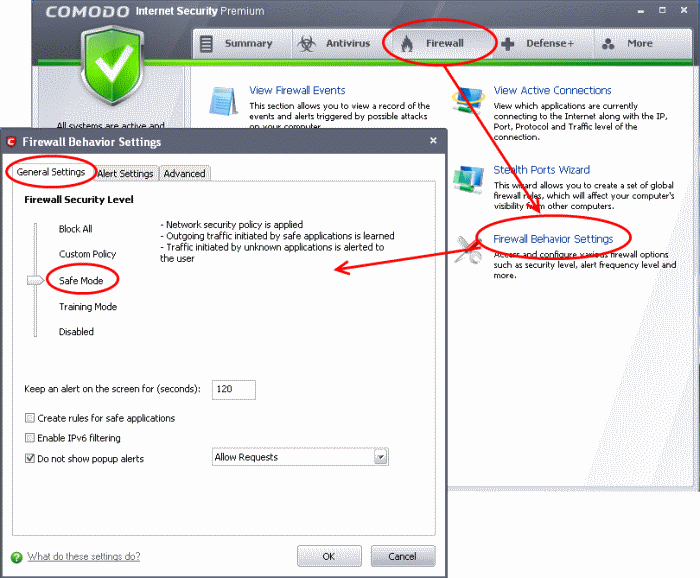
Firewall Behavior Settings
The Firewall Behavior Settings option allows you to configure the protection level for your Internet connection and the frequency of alerts generated.
To open Firewall Behavior Settings panel:
-
Click the 'Firewall' button along the top navigation
-
Click 'Firewall Behavior Settings' in Firewall Tasks menu
General Settings
-
Click on 'General Settings' tab to move the Firewall Security Level slider
-
Choose Safe mode
Safe Mode: While filtering network traffic, the firewall will automatically create rules that allow all traffic for the components of applications certified as 'Safe' by Comodo. For non-certified new applications, you will receive an alert whenever that application attempts to access the network. Should you choose, you can grant that application Internet access by choosing 'Treat this application as a Trusted Application' at the alert. This will deploy the predefined firewall policy 'Trusted Application' onto the application.
-
Click 'OK' for the changes to take effect.
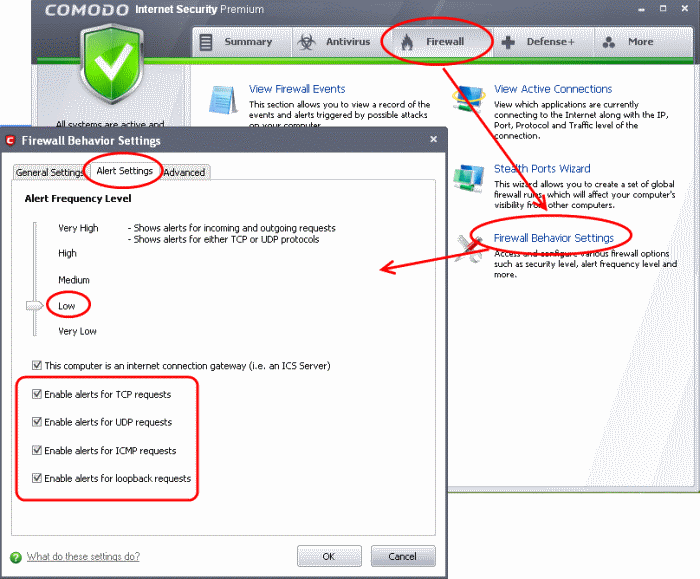
Alert Settings
-
Click the 'Alert Settings' tab in the same window.
-
Move the Alert Frequency Level slider to Low and select all the check boxes except 'This computer is an internet connection gateway'. Only enable this box if your system is configured as an ICS server (your computer is connected to Internet and shares its single Internet connection with other computers connected to it by LAN).
At the 'Low' setting, the firewall shows alerts for outgoing and incoming connection requests for an application. This is the setting recommended by Comodo and is suitable for the majority of users.
Enabling 'This computer is an Internet connection gateway' (i.e. an ICS server) allows other computers access to the Internet through this computer.
Click here for more details on Firewall Behavior settings
Advanced Settings
Advanced Settings option allows you to configure the protection level against common types of denial of service (DoS) attack.
To open Advanced Settings panel:
-
Click the 'Advanced Settings' tab in the same window.
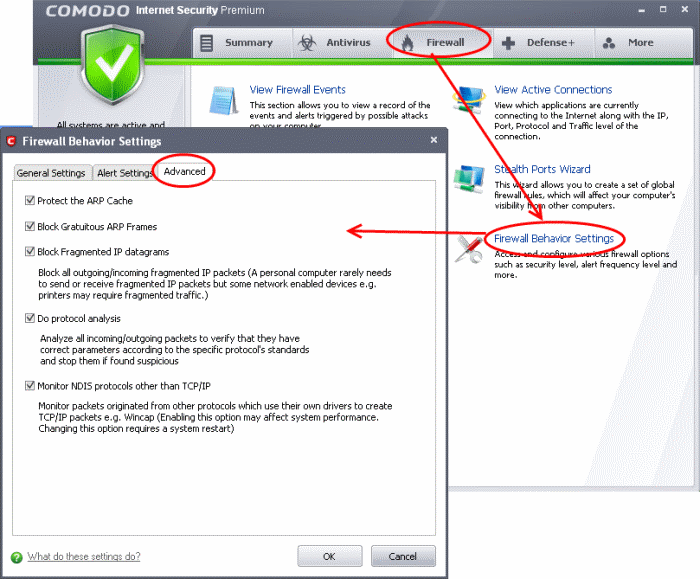
When launching a denial of service or 'flood' attack, an attacker bombards a target machine with so many connection requests that your computer is unable to accept legitimate connections, effectively shutting down your web, email, FTP or VPN server.
-
Select both the check boxes Protect the ARP Cache and Block Gratuitous ARP Frames
-
The option Block fragmented IP Datagrams is selected by default
-
Block fragmented IP Datagrams - When a connection is opened between two computers, they must agree on a Maximum Transmission Unit (MTU). IP Datagram fragmentation occurs when data passes through a router with an MTU less than the MTU you are using i.e when a datagram is larger than the MTU of the network over which it must be sent, it is divided into smaller 'fragments' which are each sent separately. Fragmented IP packets can create threats similar to a DOS attack. Moreover, these fragmentations can double the amount of time it takes to send a single packet and slow down your download time.
-
Select the Do Protocol Analysis checkbox to detect fake packets used in denial of service attacks
-
Select the Monitor NDIS protocols other than TCP/IP checkbox to capture the packets belonging to any other protocol driver than TCP/IP
-
Click 'OK'.
Click here for more details on Advanced Settings
Setting-up Network Security Policy
The Network Security Policy option allows you to configure and deploy traffic filtering rules and policies on an application specific and global basis.
To open Network Security Policy configuration panel:
-
Click the 'Firewall' button along the top navigation
-
Click 'Network Security Policy' in Firewall Tasks menu
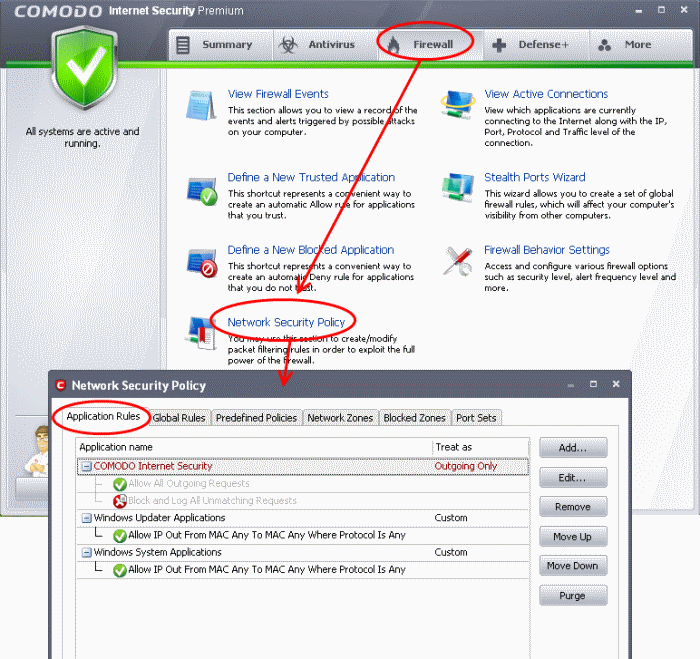
Application Rules
-
Click the 'Application Rules' tab in 'Network Security Policy' interface.
-
Click 'Add...'/'Edit...' rules for specific applications manually or 'Remove' them.
-
Click 'OK' for the change to take effect.
Click here for more details on Network Security Policy
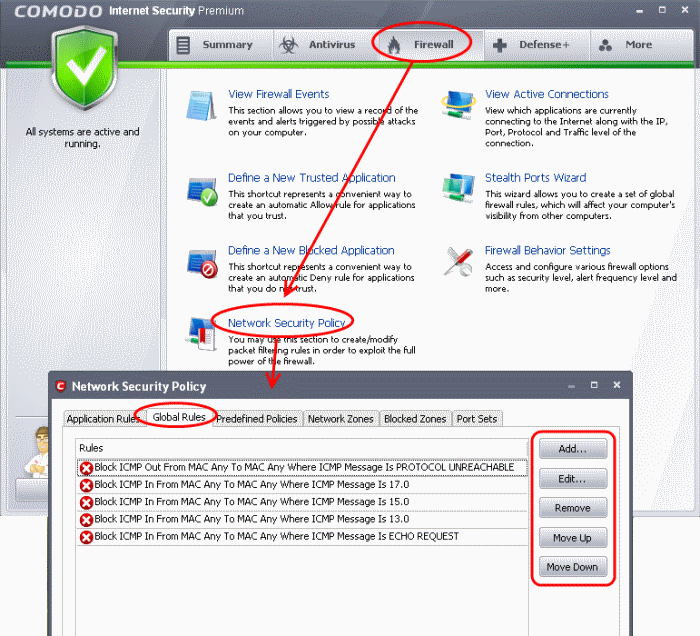
Global Rules
The Global rules can be changed manually although the defaults are usually enough. (Earlier we chose to block all incoming connections and stealthed ports to everyone).
-
Click on 'Global rules' in 'Network Security Policy'.
-
Click 'Add...'/'Edit...' rules for specific applications manually or 'Remove' them
-
Click 'OK' for the change to take effect.
Click here for more details on Network Security Policy
Predefined Policies
To view Predefined Firewall Policies:
-
Click the 'Predefined Policies' tab in the same window.
-
Click 'Edit' to view the restrictions placed by a particular policy
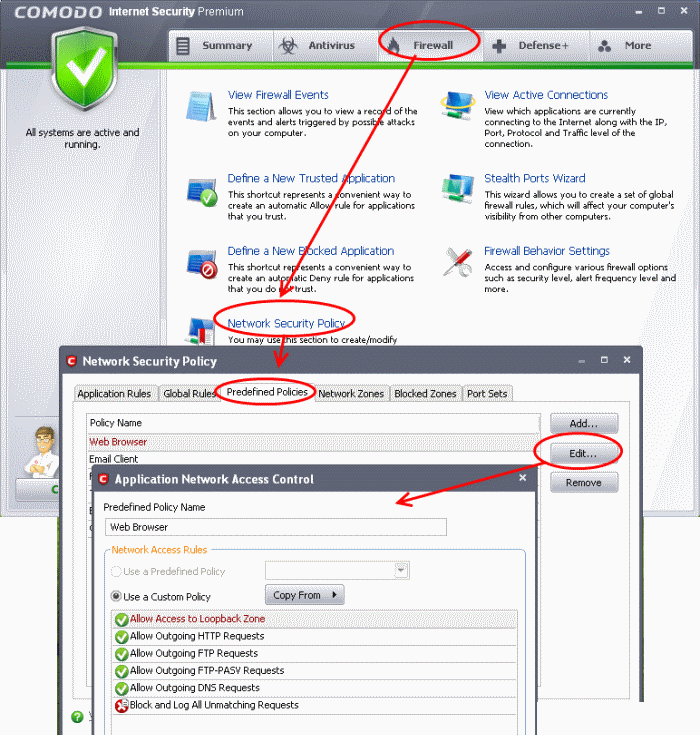
You need not make your own predefined policies, the defaults are usually enough.
Click here for more details on Predefined Firewall Policies
Comodo Internet Security User Guide | © 2012 Comodo Security Solutions Inc. | All rights reserved



