Custom Settings
The Custom Settings area enables an administrator to configure the Web Inspector PCI scans, like specifying port range to be scanned, number of parallel checks to be done concurrently, selecting Port Scanner options, selecting plug-ins to be used for scanning and more.
To access the Advanced Options area
-
Switch to 'My Accounts' area of the Web Inspector PCI interface.
-
Click the 'Custom Settings' link in the 'My Accounts' area
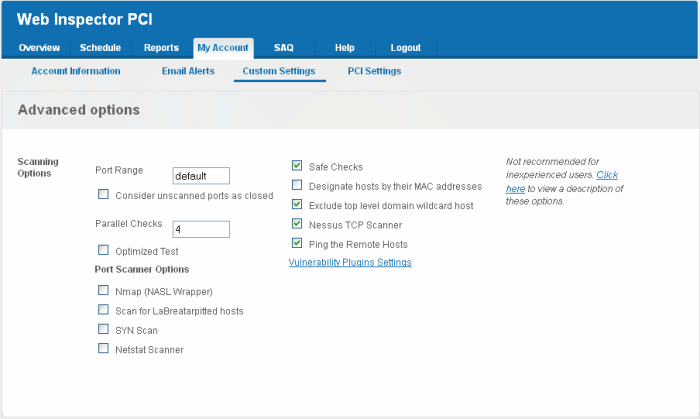
This area enables administrators to configure general options pertaining to the scans. The settings chosen in this area will apply to any scan performed on selected device in the 'Overview' and 'Scheduled Scans' areas.
|
Scan Option |
Element Type |
Description |
|---|---|---|
|
Port Range |
Text box |
Set the range of ports to be scanned. A special value of default is allowed which scans port 1-15000. To scan all TCP ports on the target host, enter '1-65535'. Enter single ports, such as "21, 23, 25" or more complex sets, such as "21, 23, 25, 1024-2048, 6000", or enter "default" to scan default ports. |
|
Consider unscanned ports as closed |
Check box |
Ports that are not specifically scanned will be assumed as in closed state. |
| Parallel Checks |
Text box |
Set the maximum number of security checks that will be performed in parallel. This may be reduced to a minimum of one to reduce network load. The maximum number of parallel checks allowed is 10% of the number of IP addresses in your account and not exceeding 25. To illustrate, If your license covers 50 IP addresses, you can run scans on five IP addresses concurrently. Lesser the number of concurrent scans, faster will be the process. |
| Optimized Test | Check box |
Allows the scan to be optimized by only performing tests if information previously collected indicates a test is relevant. When disabled all tests are performed. |
| Port Scanner Options |
||
|---|---|---|
| Nmap (NASL Wrapper) | Check box |
Runs nmap(1) to find open ports. |
|
Scan for La Breatarpitted hosts |
Check box |
Performs a labrea tarpit scan, by sending a bogus ACK and ACK-windowprobe to a potential host. Also sends a TCP SYN to test for non-persisting lebrea machines. |
| SYN Scan |
Check box |
Performs a fast SYN port scan by computing the RTT (round trip time) of the packets moving back and forth between host and the target and using the value to quickly send SYN packets to the remote host. |
|
Netstat Scanner |
Check box |
Runs netstat on the remote machine to find open ports. |
|
Safe Checks |
Check box |
Some checks are potentially harmful to the target host being scanned. When this option is enabled scans which may harm the target host are not performed. This option should be disabled to perform a full scan. |
|
Designate hosts by their MAC address |
Check box |
This option will identify hosts in the scan report by their Ethernet MAC address rather than their IP address. This is useful for networks in which DHCP is used. |
|
Exclude top level domain wildcard hosts |
Check box |
Excludes the hosts whose addresses are returned by a wildcard on some top level domains or the web server. |
|
Nessus TCP Scanner |
Check box | Enables classical TCP port scanner. It shall be reasonably quick even against a firewalled target. Once a TCP connection is open, it grabs any available banner for the service identifications. TCP scanners are more intrusive than SYN (half open) scanners. |
|
Ping the Remote Hosts |
Check box |
Pings the remote hosts through TCP connection and reports to the plug-ins knowledge base on whether the remote host is dead or alive. This sends to the remote host a packet with the flag SYN, and the host will reply with a RST or a SYNACK. |
Select the Vulnerability Plug-ins to be Deployed
Each individual vulnerability test is known as a HackerGuardian 'Plug-in'. Each individual plug-in is written to test for a specific vulnerability. These can be written to actually exploit the vulnerability or just test for known vulnerable software versions.
HackerGuardian is continuously updated with the latest plug-in vulnerability tests via a direct feed available to all PCI Scanning Service subscribers - providing up to the second security against the latest vulnerabilities. At the moment there are over 30,000 with more being developed and added weekly.
This area enables the administrator to choose which plug-ins are deployed during a scan. Plug-ins can be enabled or disabled by their family type basis.
To choose the vulnerability plug-in families, click the Vulnerability Plugins Settings link from the Advanced Options interface.
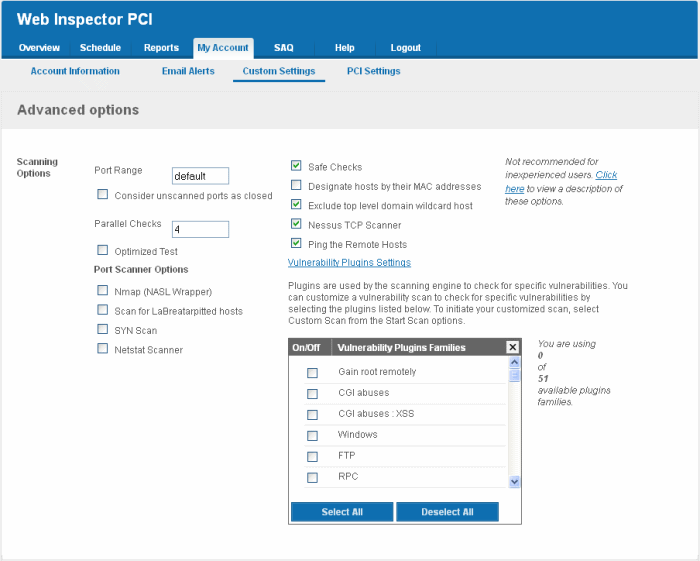
-
Select the plug-in families you wish to deploy.
| Note: You must select Custom Scan for the chosen plug-ins to be deployed, while starting / scheduling a scan. |
- Click 'Save Changes' for your settings to take effect.



