Vulnerability Report
A Vulnerability Report provides a detailed overview of scan results on a single IP/Domain. It includes a prioritized list of the vulnerabilities found, expert remediation advice and thousands of cross-referenced online advisories.
To view a Vulnerability Report of a
IP/Domain, click the '+' beside the respective device and then click
the 'Vulnerability Report' button in the row of the respective
IP/Domain.
| Tip: You can also click Vulnerability Report button beside the IP/Domain name from the 'Device List' area to view the report. |
An example of the Vulnerability Report is given below.

The Vulnerability Report consists of a summary of the scan details and the prioritized list of the vulnerabilities found.
Scan
Summary
The scan summary contains the
following details:
- Company Name - The Company name of the subscriber.
- ASV company name - Name of the approved scanning vendor (Comodo CA Ltd.,).
- Scan expiration date - The expiry date of the scan for which the report was generated.
- Start Time - The date and time at which the scan was started.
- Finish Time - The date and time at which the scan was completed.
- Total Scan Duration Time - The total time taken for the scan.
- Plugins Used - The number of vulnerability plug-ins deployed during the scan.
- A table providing the number of Security Holes, Security Warnings and Security Notes identified the IP/Domain.
- A list of open ports detected on the IP/Domain and their respective communication protocols and dedicated services.
Following the scan summary, the identified vulnerabilities are listed with their descriptions, priority, the plug-in that identified the flaw, risk factor, expert advices for remediation etc. An example is shown below.
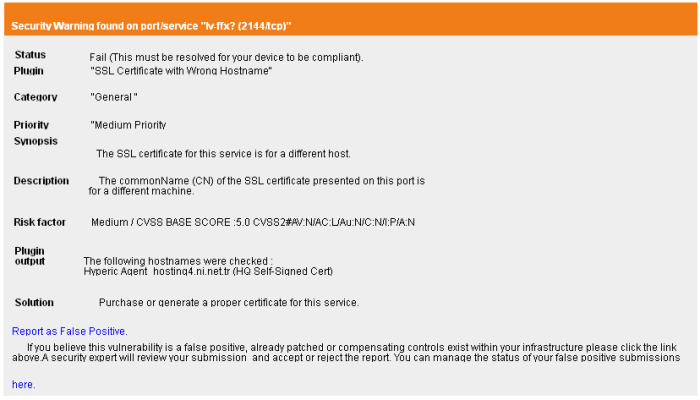
The title bar indicates the type of the vulnerability and the port/service in which it is identified.
|
Status |
- |
Indicates the status of the device whether it has passed or failed. |
|
Plugin |
|
The vulnerability plug-in that has detected the vulnerability. |
|
Category |
- |
The category of the flaw that is responsible for the vulnerability. |
|
Priority |
- |
Indicates the priority at which the vulnerability has to be re mediated. |
|
Synopsis |
- |
The Synopsis in the report provides a short description of the vulnerability. For example: if the protocol is encrypted, if debugging is enabled etc. |
|
Description |
- |
A detailed description of the vulnerability and its effects. This section also contains links for additional reading about the vulnerability. |
|
Risk Factor |
- |
Shows the severity of the vulnerability according to the CVSS score. The NVD provides severity rankings of "Low", "Medium", and "High" in addition to the numeric CVSS scores but these qualitative rankings are simply mapped from the numeric CVSS scores:
|
|
Additional Information |
- |
Provides CVE index of
standardized names for vulnerabilities and other information
security exposures, BID numbers and other references to the
vulnerability. CVE aims to standardize the names for all publicly known vulnerabilities and security exposures. Examples of universal vulnerabilities include:
Examples of exposures include:
Each CVE name includes the following:
|
|
Solution |
- |
Provides expert advices on the action to be taken by giving a set of rules to be configured for the specific port/service vulnerability. This gives the best suited remediation measure for the vulnerability found. |



