Defense+ Tasks - Introduction
The Defense+ component of Comodo Internet Security (hereafter known simply as Defense+) is a host intrusion prevention system that constantly monitors the activities of all executable files on your PC. With Defense+ activated, the user is warned EVERY time an unknown application executable (.exe, .dll, .sys, .bat etc) attempts to run. The only executables that are allowed to run are the ones you give permission to.
Defense+ also protects against data theft, computer crashes and system damage by preventing most types of buffer overflow attacks. This type of attack occurs when a malicious program or script deliberately sends more data to its memory buffer than that the buffer can handle. It is at this point that a successful attack can create a back door to the system through which a hacker can gain access. The goal of most attacks is to install malware onto the compromised PC whereby the hacker can reformat the hard drive, steal sensitive user information, or even install programs that transform the machine into a Zombie PC. For more details refer Execution Control Settings.
Defense+ boasts a highly configurable security rules interface and prevents possible attacks from root-kits, inter-process memory injections, key-loggers and more. It blocks Viruses, Trojans and Spyware before they can ever get installed on your system and prevents unauthorized modification of critical operating system files and registry entries.
The Sandbox functionality of Defense+ allows you to run suspicious and unknown executables in an isolated environment to safeguard your system from the adverse effects of those executables. This is useful for software testers and users interested in testing out the new software available over Internet.
The Defense+ Tasks area can be accessed at all times by clicking on the Defense+ tab ![]() from the navigation panel.
from the navigation panel.
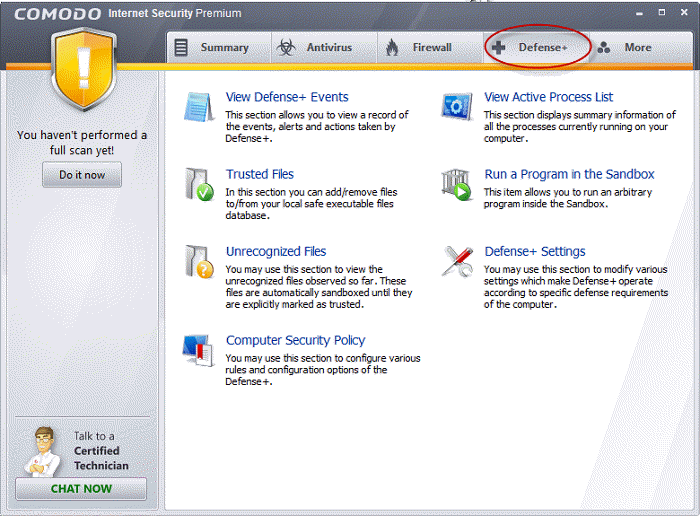
The Defense+ main configuration area provides easy access to all the features and allows you to create rules for applications and sandbox through a series of shortcuts and wizards. Click on the links below to see detailed explanations of each area in this section.
Comodo Internet Security User Guide | © 2012 Comodo Security Solutions Inc. | All rights reserved



