Manual Scanning
The Manual Scanning area allows you to set the properties and parameters for Run a Scan (On Demand Scan).
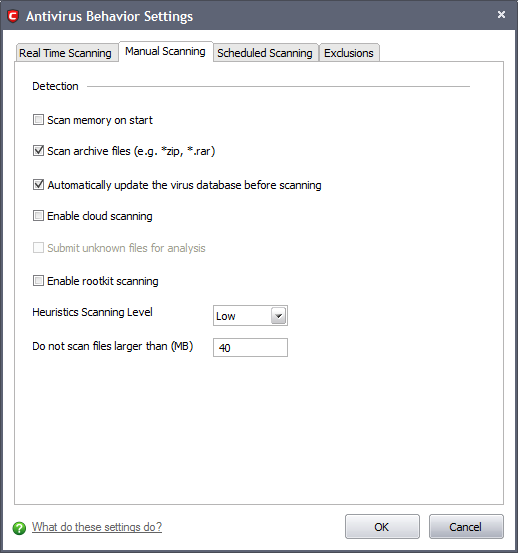
-
Scan memory on start - When this check box is selected, the Antivirus scans the system memory while starting a manual scan i.e. Run a Scan option. (Default = Enabled)
-
Scan archive files - When this check box is selected, the Antivirus scans archive files such as .ZIP and .RAR files. You are alerted to the presence of viruses in compressed files before you even open them. These include RAR, WinRAR, ZIP, WinZIP ARJ, WinARJ and CAB archives (Default = Enabled).
-
Automatically update virus database before scanning - Instructs Comodo Internet Security to check for latest virus database updates from Comodo website and download the updates automatically before starting an on-demand scanning (Default = Enabled).
-
Enable Cloud Scanning - Instructs Comodo Internet Security to perform cloud based antivirus scanning. Selecting this option enables CIS to detect the very latest viruses more accurately because the local scan is augmented with a real-time look-up of Comodo's online signature database. With Cloud Scanning enabled your system is capable of detecting zero-day malware even if your local antivirus database is out-dated (Default = Disabled).
- Submit unknown files for analysis - Files which are identified as 'unknown' i.e. the files are neither in the safe-list or black list, from the cloud based scanning to Comodo for analysis. The files will be analyzed by experts at Comodo and added to the white list or black list accordingly. This will help maintaining the white list and black list more up-to-date and benefit all the users of CIS (Default = Disabled).
- Enable rootkit scanning - Instructs Comodo Internet Security to scan the file system and Windows registry for (malicious) files or registry values that have been hidden by rootkits. If any such rootkits are found, they are listed in the scan results - enabling you to remove them from your system. (Default = Disabled)
|
Background Note:
A rootkit is a type of malware that is designed to conceal the fact that the user's system has been compromised. Once installed, they camouflage themselves as (for example) standard operating system files, security tools and APIs used for diagnosis, scanning, and monitoring. Rootkits then store hidden malicious files into the Window's file system and/or store hidden registry values into the Window's Registry. These malicious files and registry values can be used by hackers to steal user passwords, credit card information, computing resources, or conduct other unauthorized activities. Rootkits are usually not detectable by normal virus scanners as they camouflage themselves as system files. However, Comodo AntiVirus features a dedicated Rootkit detection scanner that identifies rootkits and, if any, the hidden files and the registry keys stored by them. Any discovered rootkits, hidden malicious files or registry values are listed along with the Antivirus Scan results at the end of each manual scan. |
-
Heuristics Scanning Level - Comodo Internet Security employs various heuristic techniques to identify previously unknown viruses and Trojans. ‘Heuristics’ describes the method of analyzing the code of a file to ascertain whether it contains code typical of a virus. If it is found to do so then the application deletes the file or recommend it for quarantine. Heuristics is about detecting virus-like behavior or attributes rather than looking for a precise virus signature that matches a signature on the virus blacklist.
The drop-down menu allows you to select the level of Heuristic scanning from the four levels:
-
Off – Selecting this option disables heuristic scanning. This means that virus scans only uses the ‘traditional’ virus signature database to determine whether a file is malicious or not.
-
Low (Default) - 'Lowest' sensitivity to detecting unknown threats but will also generate the fewest false positives. This setting combines an extremely high level of security and protection with the fewest number of alerts. Comodo recommends this setting as suitable for most users.
-
Medium - Detects unknown threats with greater sensitivity than the 'Low' setting but with a corresponding rise in the possibility of false positives.
-
High - Highest sensitivity to detecting unknown threats but this also raises the possibility of more false positives too.
- Do not scan files larger than - This box allows you to set a maximum size (in MB) for the individual files to be scanned during manual scanning. Files larger than the size specified here, are not scanned (Default =40MB).
Click 'OK' for the settings to take effect.
Comodo Internet Security User Guide | © 2012 Comodo Security Solutions Inc. | All rights reserved



