Executive Report
An Executive Report is a condensed view of the information available by viewing reports individually, but present it in an more easily digested manner - allowing admins to quickly pick out where insecurities lie and to assess then investigate any surges in the trends.
To view an executive summary of a
device, click the Executive Report button in the row.
| Tip: You can also click Executive Report button beside the device name from the 'Device List' area to view the report. |
An example of an executive report is shown below.
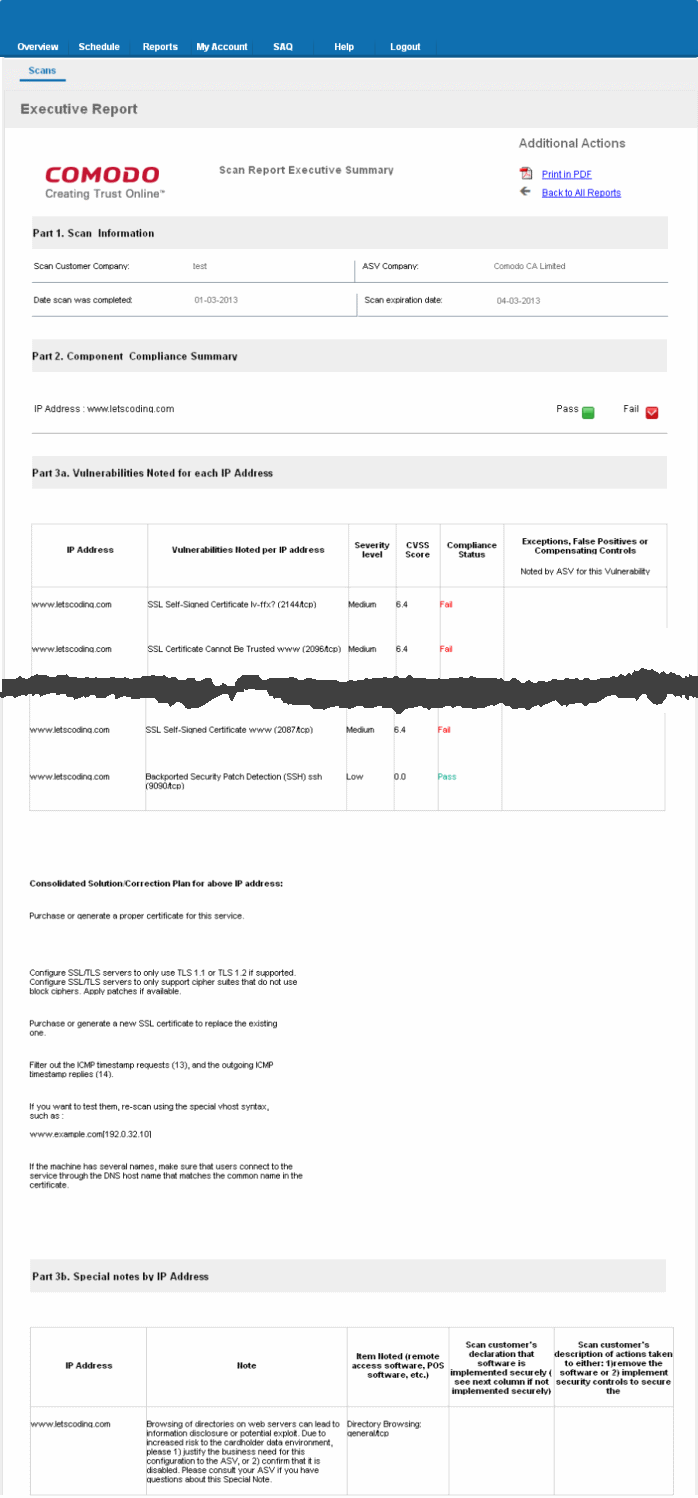
The Executive report contains the following information:
|
1. Scan Information |
- |
Provides information on the Company name of the subscriber, scanning vendor (Comodo CA Ltd.,), date of scan and the scan expiry date. |
|
2. Component Compliance Summary |
- |
Provides an at-a-glance indication of PCI Compliance status of your systems. |
|
3a. Vulnerabilities noted for each IP address |
- |
Provides details on types of vulnerabilities identified for each IP address, with their severity level, CVSS base score and compliance status. If no vulnerabilities with a CVSS base score greater than 4.0 (named 'security holes' in Web Inspector PCI) are detected then the scanned IP addresses, hosts and Internet connected devices have passed the test and the report can be submitted to your acquiring bank. If the report indicates 'Fail' on any of the IP address, then the merchant or service provider must re mediate the identified problems and re-run the scan until compliancy is achieved. |
|
3b. Special Notes by IP Address |
- |
Provides any special details or notes of the vulnerabilities found and any special declarations given by the subscriber. |
If the Component Compliance Summary section of your HackerGuardian Executive Report indicates a failure in the Compliancy Status, then vulnerabilities with a CVSS base score greater than 4.0 were discovered on your externally facing IP addresses. The accompanying Vulnerability Report contains a detailed synopsis of every vulnerability prioritized by threat severity. Each discovered vulnerability is accompanied with solutions, expert advice and cross referenced links to help you fix the problem. You should fix all vulnerabilities identified as a 'Security Hole'.
Furthermore, each report contains a condensed, PCI specific, 'Mitigation Plan' - a concise, bulleted list of actions that you need to take to achieve compliance.
After completing the actions specified in the Mitigation Plan you should run another scan until the report returns a 'Compliant' status.



