Advanced Threat Protection
- Click 'Services' > 'Advanced Threat Protection' in the left-menu to access this interface
- Advanced Threat Protection (ATP) safeguards your network against malware, hack attempts, data breaches and more.
- ATP intercepts files downloaded from websites or email attachments and uses a combination of antivirus scans, behavior analysis and blacklist checks to quickly and accurately threats.
- Application containment protects your endpoints from unknown threats. Unknown threats are those that have not yet been identified as malware by the antivirus industry. If enabled, all files with an 'Unknown' trust rating will be run in an isolated sandbox on your endpoints. This prevents them from modifying other processes, stealing user data or otherwise infecting the local machine.
- The settings you save in the profile section will be applied to all rules in your firewall policy that have 'Advanced Threat Protection' enabled.
ATP uses the following techniques to analyze the files:
- Comodo Antivirus – Continuously updated antivirus scanner which provides dependable protection against known malicious files.
- Comodo Automated Malware Analysis (CAMAS) – A cloud based behavior analysis service which improves detection of zero-day threats by rigorously testing the run-time actions of unknown files.
Based on the analysis files are identified as:
- Safe – Files identified as known good files from the whitelist/clean/safe are allowed to be downloaded at the endpoint
- Threats – Files identified as known bad from the blacklist/malicious/threats are blocked and a warning is displayed at the endpoint
- Unknown – Files that could not be identified are classified as 'Unknown'. These files are subjected to containment technology - meaning the files are wrapped and forwarded to the endpoint. Upon execution, the file is made to run in a isolated sandbox environment at the endpoint, whereby it is not allowed to modify other processes running on the endpoint nor access user data. This ensures the download is secure because it is not possible for the file to infect the endpoint, even if it transpires to be malicious. Please note that containment for unknown applications are only applied to Windows endpoints.
|
Note: Containment for Unknown Applications are only applied to Windows endpoints. |
ATP automatically creates
whitelist and blacklist of domains based on malware analysis of the
files accessed by them and also allows the administrators to manually
add domains to these lists.
The Advanced Threat Protection interface allows the administrator to create and manage the profile for ATP which can be applied for web protection Firewall Policy rules. Application containment can only be used with Full License of Dome Firewall Virtual Appliance.
To access the
Advanced Threat Protection interface, click 'Services' > 'Advanced
Threat Protection' from the left hand side navigation.
The interface contains two tabs:
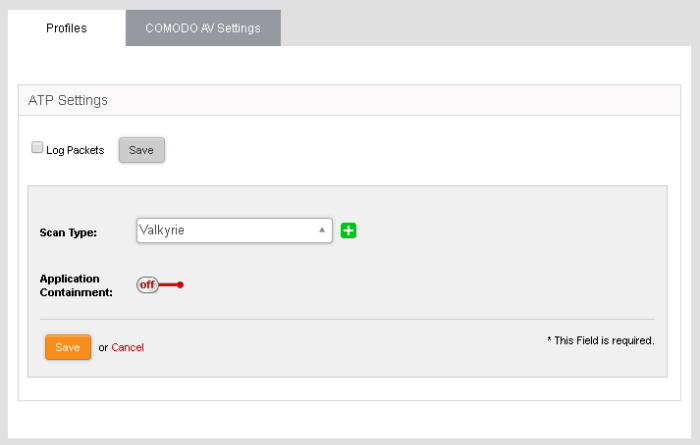
- Profiles – Define the file scan type, application containment settings and domains which should not be monitored by the ATP technologies. The settings you choose here will be applied to all rules in your firewall policy which have 'Advanced Threat Protection' enabled. See Manage ATP profiles for more details.
-
Scan Type - Allows the administrator to view the engine setting for anti-malware analysis. Currently only 'Valkyrie' is available.
- Comodo AV Settings – Allows the administrator to configure the AV engine and schedule AV scans. See Comodo Antivirus for more details.



