Manage Firewall Address Objects
Click 'Firewall' > 'Objects' to open the firewall objects interface.
- Firewall address objects represent a specific address or a group of addresses in your network.
- Firewall objects can then be referenced when creating a firewall rule, saving you time.
- You can also create firewall object groups to further streamline policy and rule creation.
Firewall address objects can be edited at anytime. Any change to an object will be reflected in all rules which include the object.
To create or manage firewall address objects
- Click 'Firewall' > 'Objects' in the left-hand menu.
- Click the 'Firewall Addresses' tab.
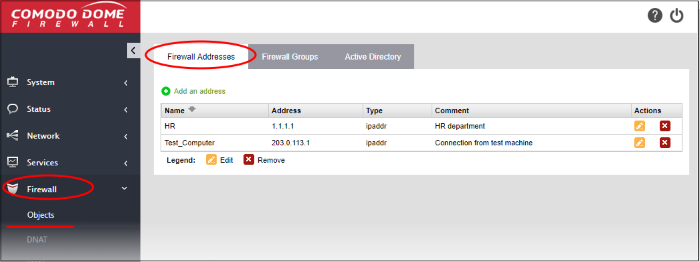
The addresses interface shows all firewall address objects added to Dome Firewall and allows you to create new objects.
|
Firewall Address Objects Table - Column Descriptions |
|
|---|---|
|
Column |
Description |
|
Name |
Label of the firewall address object. The object name will become available for selection in the 'source' and 'destination' address fields when creating a policy. |
|
Address |
The IP address(s) of the host computer(s) contained in the object. |
|
Type |
The reference type of the hosts in the object. Can be IP address, IP range, subnet or fully qualified domain name (FQDN). |
|
Comment |
A short description of the object. |
|
Actions |
Control buttons to manage the object.
Note: The object which is currently referenced in a firewall rule or in a group cannot be removed. To remove a group, the group is to be first removed from the firewall rule or group in which it is included. |
Create a Firewall Address Object
A firewall address object can be created in two ways:
-
In the 'Add an Address' area. You need to define a name and addresses for the object. See below for more details.
- Import users from Active Directory. See Add User to Firewall Objects in Active Directory Integration.
- Click 'Firewall' > 'Objects' in the left-hand navigation
- Click the 'Firewall Addresses' tab
- Click 'Add an address':
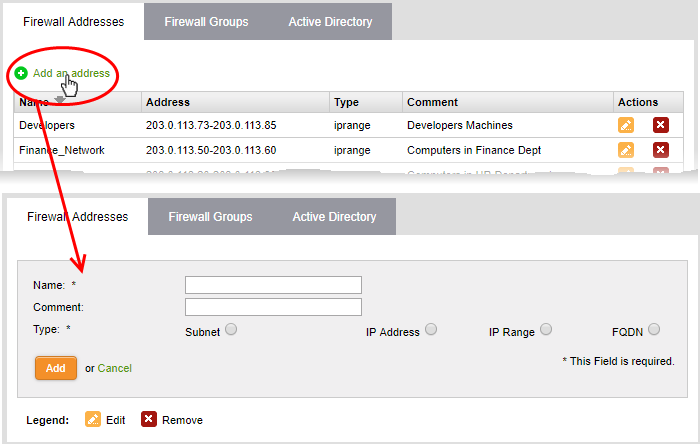
- Name - Create a label for the object (15 characters max). Only alphanumeric characters and two special characters '-' and '_' are allowed. Ideally, the object name should clearly identify the hosts in the object.
- Comment - Enter a short description of the object.
- Type – Address type. The available options are:
- Subnet - Select if the object should point to a sub-network of computers. Enter the subnet address in the space provided.
- IP address - Select if the object should point to a single IP address. Enter the address in the space provided.
- IP range - Select if the object should point to a range of IP addresses. Enter the range in the space provided.
- FQDN – Select if the object should point to a fully qualified domain name. Enter the domain in the space provided.
- Click 'Add'. The new object will be added to the list.
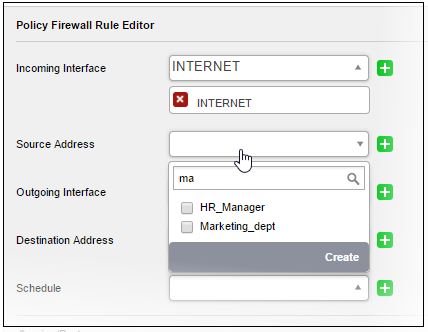
- The object will become available for selection as a source or destination when creating a firewall rule. You can locate the object by typing the first few letters of its name:




 - Removes the object.
- Removes the object.