Manage Application Identification Rulesets
- Application ID rulesets let you allow or block TCP/P traffic from specific applications
To open the 'Application Identification' rules interface
- Click 'Services' > 'Intrusion Prevention' in the left-hand menu
- Click the 'Application Identification' tab
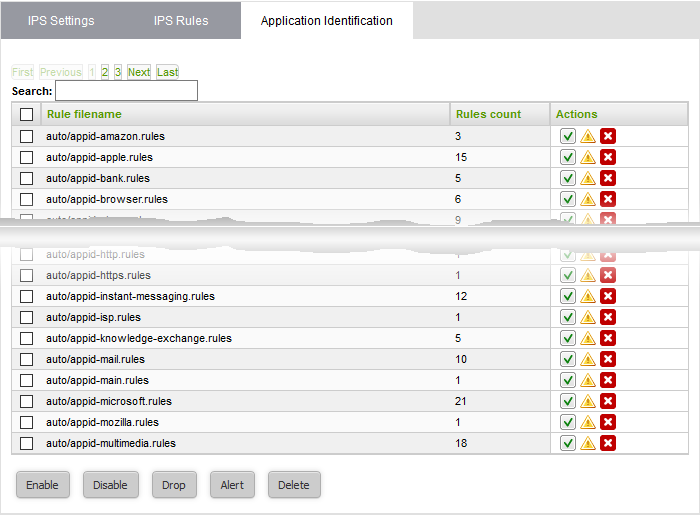
|
Rules Table - Column Descriptions |
|
|---|---|
|
Column |
Description |
|
Rule filename |
The name of the rules file that contains the constituent rules of the ruleset. |
|
Rules count |
Indicates the number of constituent rules in the rule set. |
|
Actions |
Displays control buttons for the ruleset.
|
The interface allows the administrator to:
The rules can be enabled or disabled individually or collectively.
- To enable or disable a single ruleset, select or unselect the checkbox beside the ruleset in the 'Actions' column
- To enable inactive rulesets collectively, select the rules by marking the checkboxes at the left of the rulesets to be enabled and click the 'Enable' button from the bottom of the right pane.
- To disable active rulesets collectively, select the rules by marking the checkboxes at the left of the rulesets to be disabled and click the 'Disable' button from the bottom of the right pane.
- After making the changes, click the 'Apply' button in the confirmation
pane that appears at the top to apply the changes.
Change application policy of rules
A rule can be applied in two ways:
- Alert Policy -The Intrusion Prevention system generates an alert when a data packet from applications identified by a rule in the ruleset is encountered and passes the packet. The policy is indicated by alert icon

- Drop Policy - The Intrusion Prevention system blocks the data packet from an application identified by a rule in the ruleset without generating an alert. The policy is indicated by shield icon The administrator can toggle the
application policy for individual rule or for group of rules
 .
.
- To toggle the policy of a ruleset from 'Alert' policy to 'Drop' policy, click the 'Alert' icon in the row of the ruleset under the 'Actions' column
- To toggle the policy of a ruleset from 'Drop' policy to 'Alert' policy, click the 'Shield' icon in the row of the ruleset under the 'Actions' column
- To toggle the policy of a group of rulesets with 'Alert' policy to 'Drop' policy, select the rulesets by marking the checkboxes at the left of the ruleset file names and click the 'Drop' button at the bottom of the interface
- To toggle the policy of a group of rulesets with 'Drop' policy to 'Alert' policy, select the rulesets by marking the checkboxes at the left of the ruleset file names and click the 'Alert' button at the bottom of the interface
- After making the changes, click the Apply button in the confirmation pane that appears at the top to apply the changes.
Unwanted Application Identification rulesets can be removed from Comodo Dome Firewall from the 'Application Identification' interface.
- To remove a single ruleset click the delete
 icon in the row of the ruleset filename, under 'Actions' column and click 'OK' in the confirmation dialog
icon in the row of the ruleset filename, under 'Actions' column and click 'OK' in the confirmation dialog
- To remove a group of rulesets collectively, select the them by marking the checkboxes at the left of the ruleset file names and click the 'Delete' button at the bottom of the interface. Click 'OK' in the confirmation dialog



