Handle Malware on Scanned Devices
- Click 'Security' > 'Endpoint Security Status'
- Click the 'Protective Action' button to remove, ignore or quarantine the malware.
|
Tip:
|
Apply actions to ALL malware on selected devices
- Click 'Security' > 'Endpoint Security Status'
- Click a company name/group on the left to view their devices
Or
- Select 'Show All' on the left menu to view every device enrolled to EM
- Select device(s) with a malware status of 'Infected' using the check-box(es) on the left.
|
Tip: You can filter the list to search for specific devices by clicking the funnel icon at the top right of the table. |
- Click
'Protective Action' above the table and select your desired action:
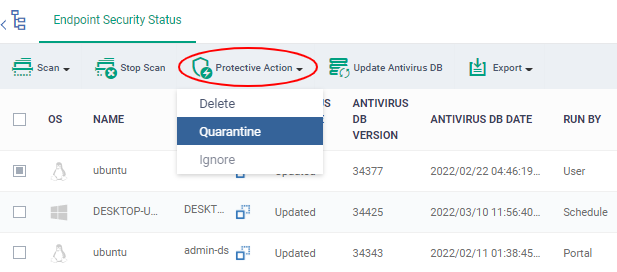
The actions available depend on the OS of the device chosen:
For Android Devices:
- Delete - Removes the malicious app
- Ignore - Ignores malware found by the last scan.The item will be identified as malware again on the next scan.
For the 'Delete' operation, a notification will be sent to the selected devices to uninstall the app(s):
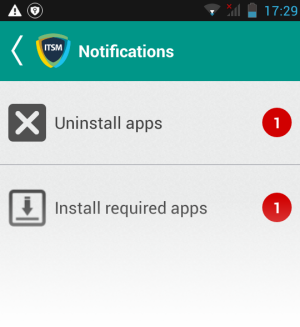
The notification shows the number of threats which will be removed from the device.
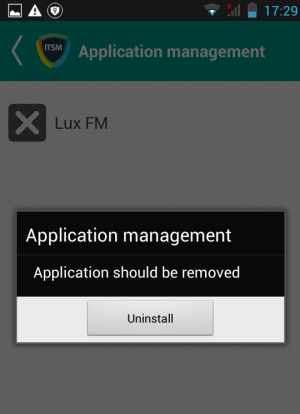
- Touch
the alert to view all items which are ready for removal.

- Tap on the malware to be removed, confirm the removal in the next dialog and follow the uninstall wizard.
For Windows, Mac OS and Linux Devices
- Delete - Instructs XCS on the endpoint to clean the malware.
- If a disinfection routine is available, XCS will disinfect it and retain the original file.
- If a disinfection routine is not available, XCS will delete the application.
- Quarantine - Moves the malware to quarantine on the device.
- Click 'Security' > 'Quarantined Threats' to manage quarantined files.
- Based on their trustworthiness, you can remove them from the device or restore them to their original locations. See View and Manage Quarantined Items for more details.



