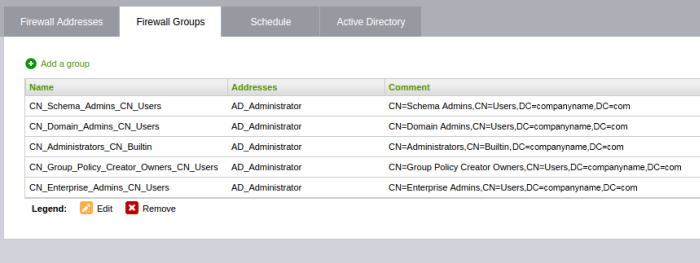
Active Directory Integration
Integrating Dome Cloud Firewall with your
Active Directory (AD) server allows you to implement identity-based
security on your network. Once a directory has been imported, Dome Firewall will map usernames to IP addresses, allowing
you to apply firewall policies to individuals or groups.
DCF uses LDAP (Lightweight Directory Access Protocol) to import network users from the AD server, track login activity and regulate user traffic to and from the IP addresses.
AD server
integration involves four steps:
Step 1- Install the Dome Cloud Firewall AD Agent onto the AD Server
You first need to install an agent on your AD server to facilitate communications:
-
Download the agent setup file:
- Login to your DCF account
- Click 'Firewall' on the left then 'Objects' > 'Active Directory'.
- Click the 'Download Active Directory Agent' link at the top right
- Copy the setup files to your AD server
-
Double-click the setup file to start the installation wizard.
-
Follow the wizard to complete the installation. By default, the agent will be installed at C:/Program Files (32 bit system) or C:/Program Files (x86) (64-bit system).
Step 2 - Add Socket Exception on the server for the AD Agent
The next step is to configure a socket exception for the agent in Windows Firewall on your server. This will allow the agent to communicate with DCF.
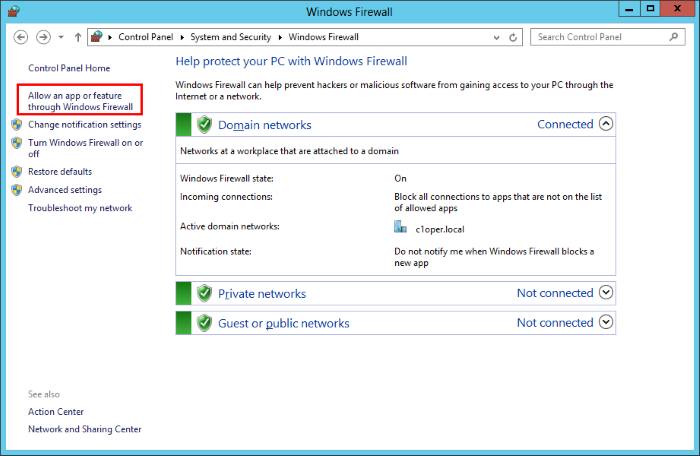
1. Open the Windows Server Control Panel
2. Click the 'Windows Firewall' icon to open the firewall configuration panel. Please note, the following instructions may vary slightly depending on your server version
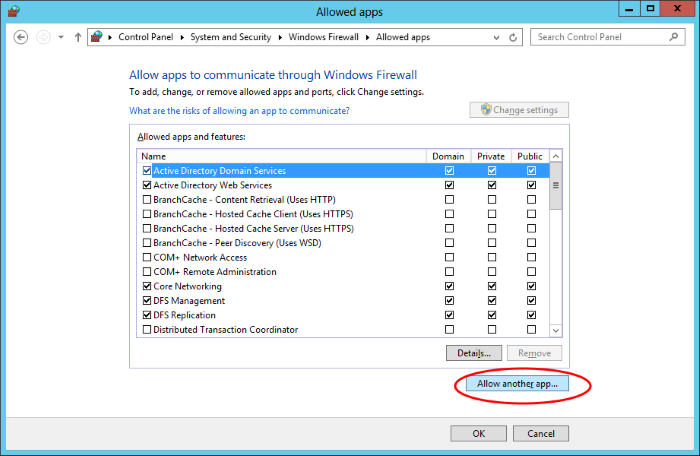
3. Click 'Allow a program or feature':
-
On the next screen, click 'Allow another program' to add the agent to the list of exceptions.
-
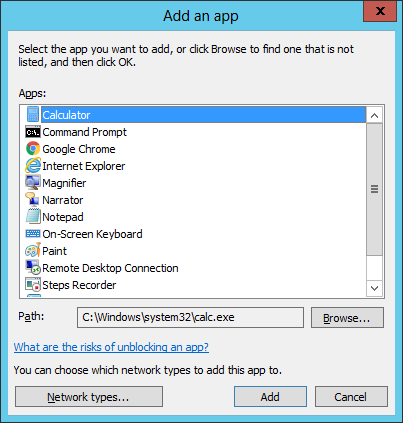
Click 'Browse' in the resulting 'Add a Program' dialog. Navigate to the agent's install folder, select 'ActiveADUsersService.vshost' and click 'Open'.
-
Click 'Add' in the 'Add a program' dialog then 'OK' in the 'Allow programs to communicate...' screen.
Step 3 - Configure the AD Agent
Next, the agent needs to be configured to connect to Dome Cloud Firewall.
-
Browse to the agent installation folder (C:/Program Files on 32-bit system and or C:/Program Files (x86)) and open 'ActiveADUsersService.exe'.
-
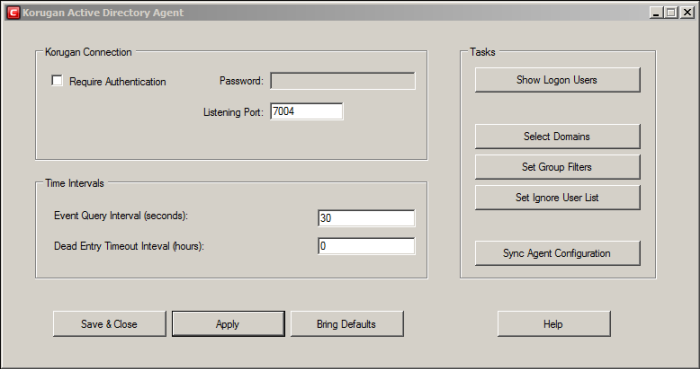
Configure the parameters as shown below:
Connection Parameters
- Require Authentication - If you require password authentication for DCF to connect to the server, enable 'Require Authentication' and specify the password.
- Listening Port - The agent communicates with DCF through port 7004 by default. If you want to change the port, enter the port number in the text field.
Time Intervals
- Every Query Interval - Enter the time interval (in seconds) at which the agent should poll DCF for updates. It is recommended to set the interval according to the size of the directory. Directories with larger numbers of users should be checked more frequently.
- Dead Entry Interval - Dome Cloud Firewall will delete a username-IP map entry if a user has not logged-in for a certain period of time. For example, if the 'Dead Entry Interval' is set as 720 hours, then the username-IP map entry for the user will be deleted if the user does not login for 30 days.
Tasks
- Show Logon Users – Shows currently logged-in users and their IP addresses
- Select Domains - By default, the agent tracks login events for all domains which have been added to the AD server. Click the 'Select Domains' button to enable or disable tracking on specific domains.
- Set Group Filters - By default, the agent tracks login events for all AD user groups. Click the 'Set Group Filters' button to enable or disable tracking on specific domains.
- Set Ignore List - By default, the agent tracks login events for all AD users. Click the 'Set Ignore Users' button to specify users who should not be tracked.
- Sync Agent Configuration - Enables you to export the current configuration of the agent.
- Click 'Apply' to save your configuration
- Click 'Save and Close' to close the application window. The agent process will continue to run in the background.
The agent is now configured to connect to DCF. The next step is to configure DCF to receive the connection.
The next step is to configure DCF to communicate with the agent and the AD server.
-
In order to allow access to DCF, Firewall Rules are to be created under Firewall > System Access interface, specifying the IP address/port and the service details. See Allow Access to DCF for more details on creating the system access rules. A detailed description of System Access rules can be found in Configure System Access.
- You need to enter the IP address and port details of the server in the firewall console so it can receive the username/IP address map tables and updates from the agent. See Configure the Active Directory Connection for more details.
'System Access' rules can be added to DCF as follows:
To add the rule for the server to access DCF
- Click 'Firewall' > 'System Access' to open the 'System Access' interface
- Click 'Add a new system access rule' link from the top left.
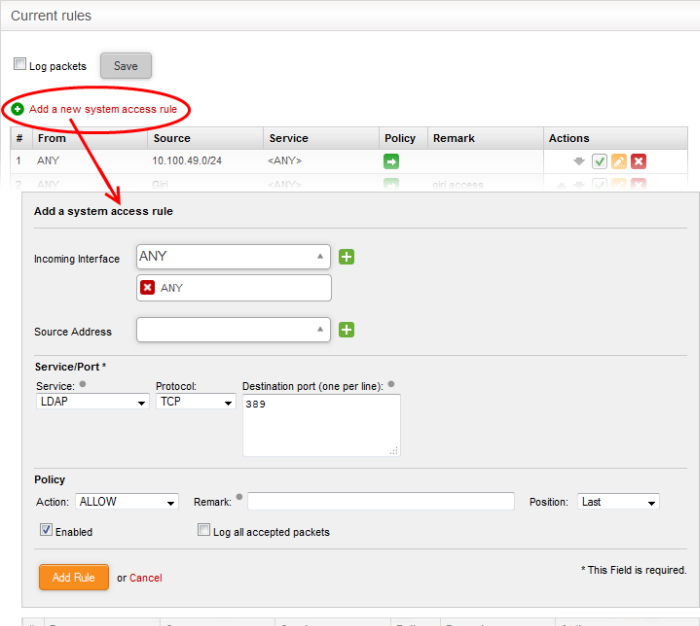
- Enter the following settings:
Incoming Interface - Select
'Any' from the drop-down
Source Address - Need not select any firewall object
Service/Port - Select LDAP service traffic received at port 389
- Service - Choose 'LDAP' from the drop-down
- Protocol - By default TCP will be chosen
- Destination port - The default port number of 389 will be auto-populated. Enter a new port number if the LDAP port of your server is different.
Policy - Choose 'Allow'.
General Settings -
Remark (optional) - Enter a short description for the rule. The description will appear in the Remark column of the rules interface.
Position - Set the priority of the rule with respect to other rules in the list. Rules in iptables are processed in the order they appear on the list.
Enabled – If selected, the rule will be activated immediately after saving.
Log all accepted packets - All packets allowed by the rule will be logged. See 'View Logs' for more details on configuring storage of logs and viewing the logs.
-
Click 'Add Rule'
To add the rule for the agent to access DCF
- Open the 'System Access' interface by clicking Firewall > System Access from the left hand side navigation
- Click 'Add a new system access rule' link from the top left.
- Enter the parameters for the new rule as shown below:
Incoming Interface - Select
'Any' from the drop-down
Source Address - Need not select any firewall object
Service/Port - Select the TCP traffic received at port 389
- Service - Choose 'User Defined' from the drop-down
- Protocol - Choose TCP from the drop-down
- Destination port - Enter the agent port as configured in the server in Step 3. (Default = 7004).
Policy - Choose 'Allow'.
General Settings -
- Remark (optional) - Enter a short description for the rule. The description will appear in the Remark column of the rules interface.
- Position - Set the priority of the rule with respect to other rules in the list. Rules in iptables are processed in the order they appear on the list.
- Enabled – If selected, the rule will be activated immediately after saving.
- Log all accepted packets - All packets allowed by the rule will be logged. See 'View Logs' for more details on configuring storage of logs and viewing the logs.
- Click 'Add Rule'.
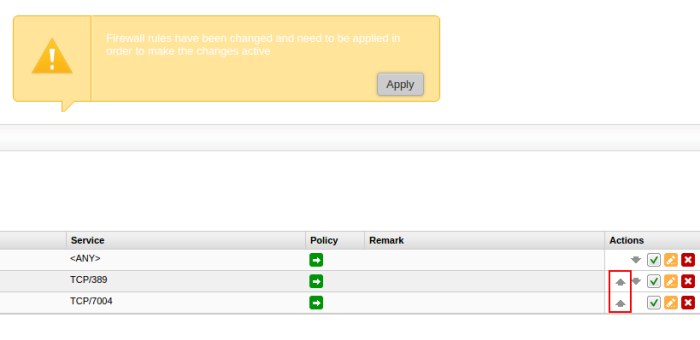
The rules will be added to the System Access interface.
- Place new two rules to uppermost levels by clicking arrow buttons / and Click 'Apply' to apply new order.
Configure the Active Directory Connection
The Active Directory interface in the administrative console allows you to configure the appliance for the connection.
To access the Active Directory interface
- Click 'Firewall' > 'Objects' from the left hand side pane
- Click the 'Active Directory' tab
-
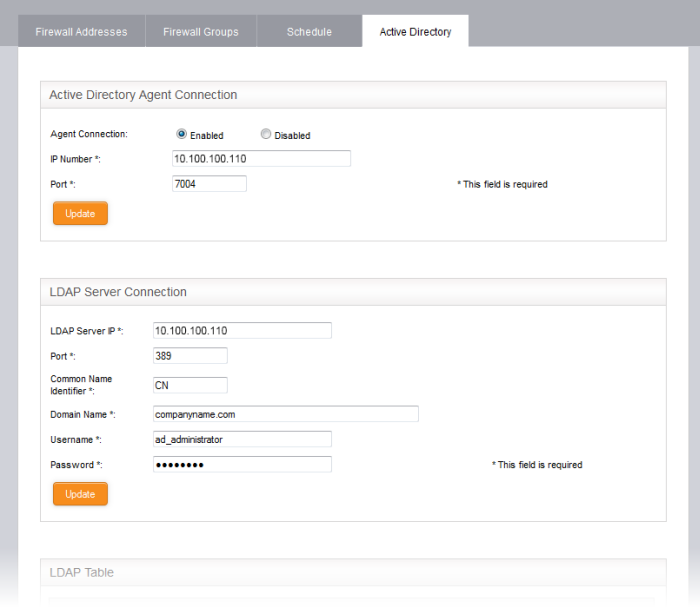
Enter the parameters for the agent and the AD server as shown below:
Active Directory Agent Connection
- Agent Connection - Choose 'Enabled' to enable the connection from the agent
- IP Number - Enter the IP address of the server on which the agent is installed
- Port - Enter the agent connection port as configured in the server in Step 3. (Default = 7004).
- Password - Enter the password if it is set on agent in Step 3
- Click 'Update' to save and activate the agent connection.
LDAP Server Connection
- LDAP Server IP - Enter the IP address of the AD server. The IP address is generally same with the agent's address.
- Port - Enter the LDAP service port of the server. By default, the LDAP port is 389. If you have configured a different port, enter the new port number.
- Common Name Identifier - Enter the Common Name Identifier of Active Directory. (Default = CN).
- Domain Name - Enter the Domain Name to select which domain is going to monitored on LDAP Table displayed at the bottom of the page.
- Username and Password - Enter the Username and Password of a user account that has the 'Read' access the AD server. 'Write' access is not required.
- Click 'Update' to save and activate the AD server connection.
The selected domain(s) will be displayed in the 'LDAP Table' at the bottom of the interface.
Clicking the Domain name expands the tree structure of the active directory.
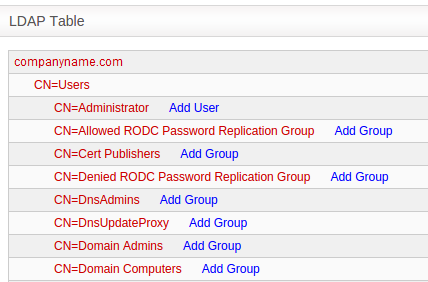
You can add the users to firewall objects and user groups to firewall object groups from the tree LDAP table.
Adding User to Firewall Objects
- Click the Domain name to expand the tree structure of the active directory.
- Locate the user by expanding the parents.
- Click
'Add User' to add the user to Firewall Objects.
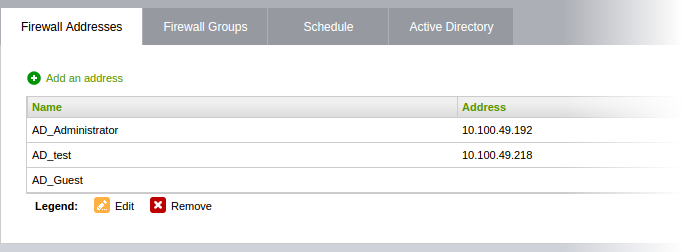
Adding User Groups to Firewall Objects
- Click the Domain name to expand the tree structure of the active directory.
- Locate the user group by expanding the parents.
- Click 'Add Group' to add the user group to Firewall Object Groups.