Manage Firewall Policy Rules
The Firewall Policy interface allows the administrator to enable/disable the firewall policy and to create and manage the firewall rules for outgoing, incoming and inter-zone traffic.
To access the Policy Firewall interface, click 'Firewall' > 'Policy' from the left hand side navigation and select the 'Firewall Policy' tab.
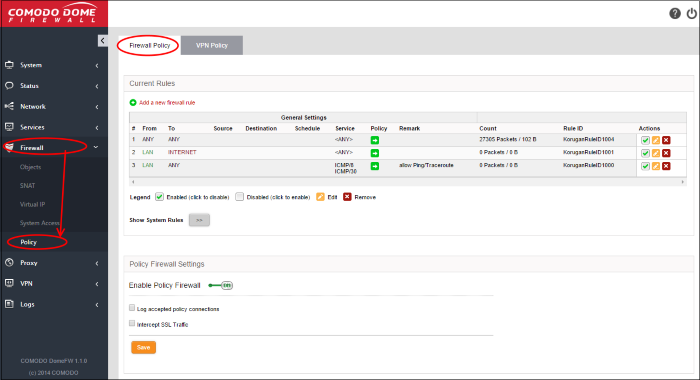
The interface displays two panes:
-
Current Rules - The upper 'Current Rules' pane displays a list of rules in action and allows the administrator to add new rules and edit existing rules. See Managing Firewall Rules for more details on viewing and managing the rules.
-
Policy Firewall Settings - The lower ' Policy Firewall Settings' pane displays the current enabled/status of the policy firewall, allows the administrator to change the status and to configure the policy firewall log. See Configuring the Policy Firewall Settings for more details.
The 'Current Rules' pane displays a list of rules in action with their configuration parameters and allows the administrator to manage them and to create new rules.
|
|
Policy Firewall Rules Table - Column Descriptions |
|
|---|---|---|
|
Category |
Column |
Description |
|
General Settings |
# |
Serial number of the rule. |
|
From |
The interface device or the network zone from which the traffic originates. |
|
|
To |
The interface device or the network zone to which the traffic is directed. |
|
|
Source |
The Firewall Object or Object Group containing the IP address, IP Address Range or the subnet of the host(s) from which the traffic originates. |
|
|
Destination |
The Firewall Object or Object Group containing the IP address, IP Address Range or the subnet of the host(s) to which the traffic is directed. |
|
|
Schedule |
The schedule object that covers the time period for which the rule is active. |
|
|
Service |
The service that uses the traffic, indicated as the protocol and the port used |
|
|
Policy |
Indicates the allow/block policy of the rule. |
|
|
Remark |
A short description of the rule. |
|
|
|
Count |
Indicates the number of packets and size of data intercepted by the rule. |
|
Rule ID |
Identity number of the rule as per the order of creation in DCF. The traffic is allowed or denied based on the first matching rule in the ascending order of the ID numbers, regardless of order of the rules as displayed in the table. |
|
|
Actions |
Displays control buttons for managing the rule. |
|
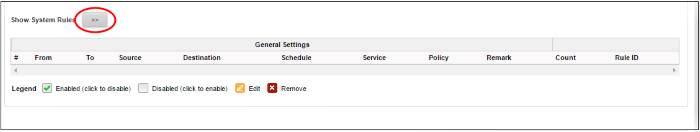
- Click the right arrow button beside 'Show system rules' to view a list of firewall rules auto generated by DCF. These rules cannot be modified or removed.
Creating Policy Firewall rules
To create a new firewall rule
- Open the 'Firewall Policy' interface by clicking 'Firewall' > 'Policy' from the left hand side navigation and selecting 'Firewall Policy' tab.
- Click the 'Add a new firewall rule' link at the top left. The 'Policy Firewall Rule Editor' will open.
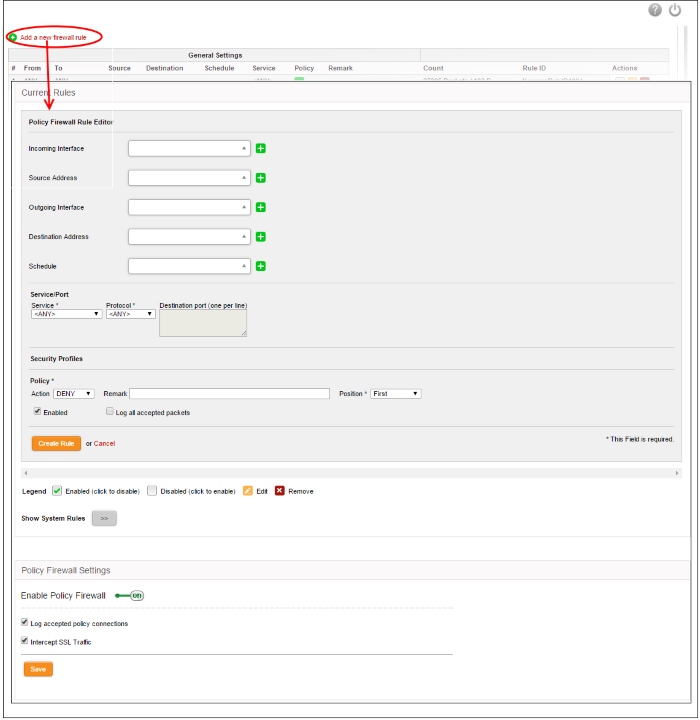
The 'Policy Firewall Rule Editor' interface is divided into four areas for specifying the different components of the rule:
|
- |
Choose the source and destination of the traffic and set a schedule for the rule to be active. |
|
|
- |
Specify the service pertaining to the traffic to be intercepted by the rule. |
|
|
- |
Configure to allow or block the traffic intercepted by the rule. |
Address Settings and Schedule
-
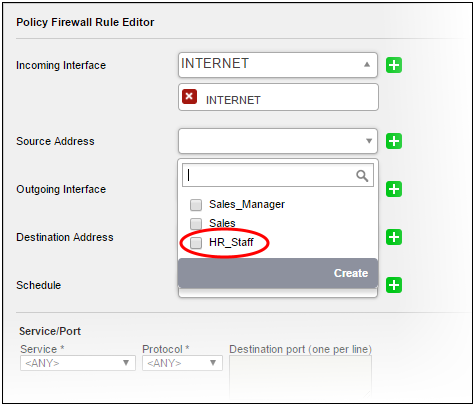
Incoming Interface - Choose the interface device or the physical port at which the traffic is received, from the drop-down.
-
Source Address - Choose the firewall object or the object group that covers the IP address, IP address range or the subnet, at which the traffic to be intercepted by the rule, is received.
If a firewall object covering the IP address/IP Address range or the subnet to be specified has not been created under the 'Firewall Objects' interface previously, you an create a new object from this interface too.
- Click the drop-down arrow and click 'Create' at the bottom of the list. A new pane for creating a new object will appear.
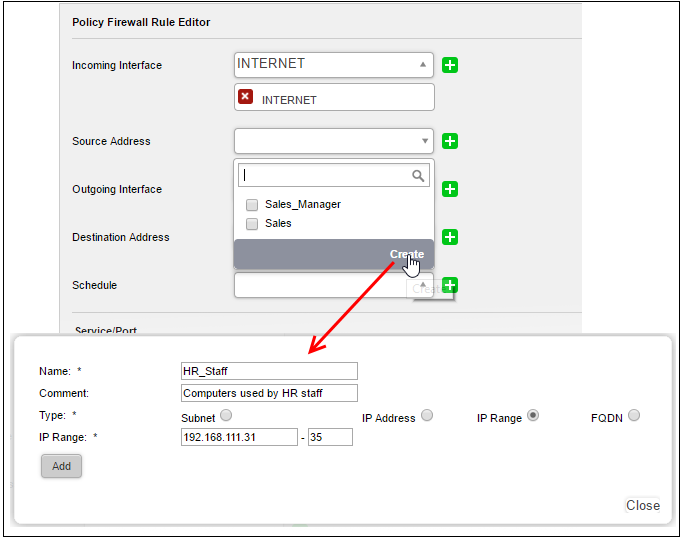
- Name - Specify a name for the object (15 characters max) representing the host(s) included in the object.
- Comment – Enter a short description of the object.
- Type - Select the type by which the hosts are to be referred in the object. The available options are:
- Subnet - Select this if a sub network of computers is to be covered by the object and enter the sub network address
- IP address - Select this if a single host is to be covered by the object and enter the IP address of the host
- IP range - Select this if more than one host is to be covered by the object and enter the IP address range of the hosts
- FQDN - Select this if a fully qualified domain name is to be covered by the object and enter the same.
- Click 'Add'.
The new object will be added and will be available for selection from the Select network/IPs drop-down.
The new object will also be added to the list of objects under 'Firewall Objects' and will be available for selection for creating other firewall rules too.
-
Outgoing Interface - Choose the interface device or the physical port to which the traffic is directed, from the drop-down.
-
Destination Address - Choose the 'Firewall Object' or 'Object Group' containing the IP address, IP Address Range or the subnet of the host(s) to which the traffic is directed, from the drop-down.
If a firewall object covering the IP address/IP Address range or the subnet to be specified has not been created under the 'Firewall Objects' interface previously, you an create a new object from this interface too. See explanation above for more details.
-
Schedule - The Schedule Objects added to the Firewall Objects > Schedule interface will be available in the drop-down. Choose the schedule object(s) that cover the time period(s) for which the rule needs to be active from the drop-down.
If the schedule object covering the required time period P to be specified has not been created under the Firewall Objects > Schedule previously and hence not available in the drop-down, you can create a new object from this interface too.
To create a new schedule object
- Click the drop-down arrow and click 'Create' at the bottom of the list. A new pane for creating a new object will appear.
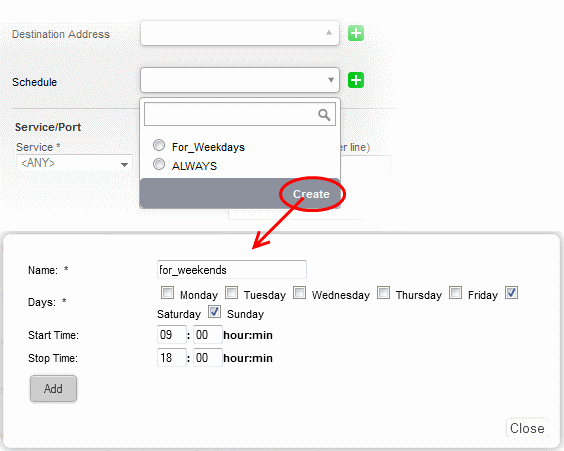
- Name - Specify a name for the schedule.
- Days - Select the days of the week at which the firewall should be active.
- Start Time and Stop Time - Enter a time at which the firewall should be started and stopped at the selected days in 24 Hrs time format. Click 'Add' for the new schedule to be created.
- Click 'Add' for the new schedule to be created.
The new schedule object will also be available for selection in the drop-down and also will be added to the list of schedule objects under Firewall Objects > Schedule interface. The new object will be available for selection for creating other firewall rules too.
Service/Port - Select the type or the service hosted by the source, the protocol and the port used by the service.
- Service - Choose the type of service from the drop-down
- Protocol - Choose the protocol used by the service
- Destination port - Specify the destination port(s) of the service one by one, in the 'Destination Port' text box.
|
Tip: DCF is configured with predefined combinations of service/protocol/port, like HTTP/TCP/80, [ALL]/TCP+UDP/0:65535, or [ANY], which is a shortcut for all services, protocols, and ports. If you want to specify custom protocol/port combination, then select 'User Defined' from the service. You can also specify additional destination ports for standard combinations, for the services that run on ports different from the standard ones. |
-
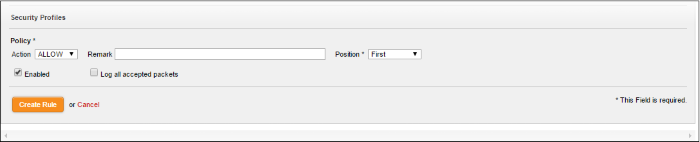
Action - Specify whether the packets matching the rule should be allowed or denied from the Policy drop-down. The options available are:
- Allow - The data packets will be allowed without filtering
- Deny - The packets will be dropped
- Reject - The packets will be rejected, and error packets will be sent in response
-
Remark - Enter a short description for the rule. The description will appear in the Remark column of the Rules table.
-
Position - Set the priority for the rule in the list of rules in the respective rules interface. The rules in the iptables are processed in the order they appear on the list.
-
Enabled - Leave this checkbox selected if you want the rule to be activated upon creation.
-
Log all accepted packets - Select this checkbox if you want the packets allowed by the rule are to be logged. See View Logs for more details.

- Click 'Create Rule'. A confirmation dialog will appear.
Configuring the Policy Firewall Settings
The lower 'Policy Firewall Settings' pane allows the administrator to enable/disable the Policy firewall rules and to opt for logging the packets that pass the rule and analysis of HTTPS sites.
- Use the 'Enable policy firewall' toggle switch to switch the state of the VPN firewall
- Select the 'Log accepted policy connections' check box to log the packets that has passed the Firewall Policy. See View Logs for more details on viewing the logs
- Select the 'Intercept SSL Traffic' check box in order for analysis of HTTPS sites. Please note the SSL certificate of DCF should be installed on endpoints for this feature to work
- Click 'Save' for your settings to take effect




 - The checkbox allows the administrator to
switch the rule between enabled and disabled states.
- The checkbox allows the administrator to
switch the rule between enabled and disabled states. - Opens the 'Edit' interface and enables to
edit the parameters of the rule. The 'Edit' interface is similar
to 'Policy Firewall Rule Editor' interface from which the new
rules are created. See '
- Opens the 'Edit' interface and enables to
edit the parameters of the rule. The 'Edit' interface is similar
to 'Policy Firewall Rule Editor' interface from which the new
rules are created. See ' - Removes the rule.
- Removes the rule.