IPSec Configuration
This area allows administrators to configure IPsec tunnels between different networks and sites. Dome Cloud Firewall supports the following types of connection:
- Host to Net VPN – Allows remote mobile devices, desktops and laptops to securely connect to internal networks
- Net to Net VPN – Allows network to network IPsec VPN connections
- L2TP Host to Net VPN – Enables external clients using L2TP clients to connect to internal networks through an IPsec VPN
To open the 'IPSec' interface, click 'VPN' > 'IPSec' on the left menu:
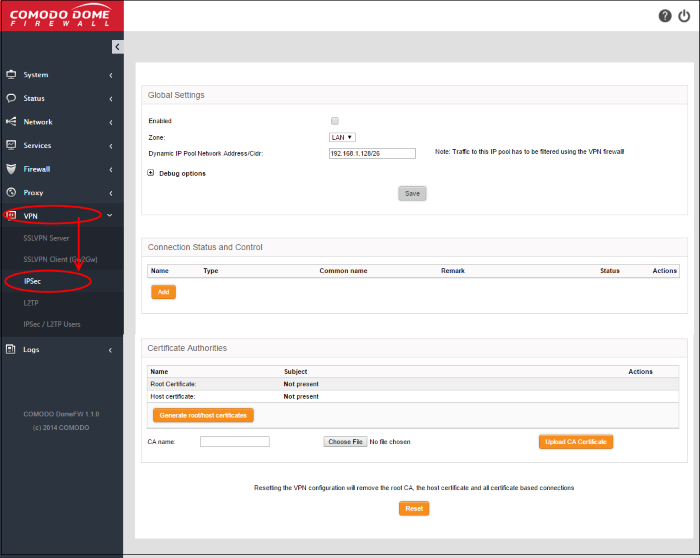
Administrators can use the interface to create, enable, configure and monitor IPsec connections, and to configure authentication preferences. Authentication between IPsec connected interfaces can be implemented via certificate-based authentication or by pre-shared key.
The interface contains three areas:
The 'Global Settings' area allows administrators to enable or disable the IPsec VPN service, to configure which internal network zones can be accessed over IPsec and to specify the dynamic IP address pool that should be used when assigning addresses to external clients. The 'Debug Options' area allows administrators to choose how much information is included in IPsec events in debugging logs.
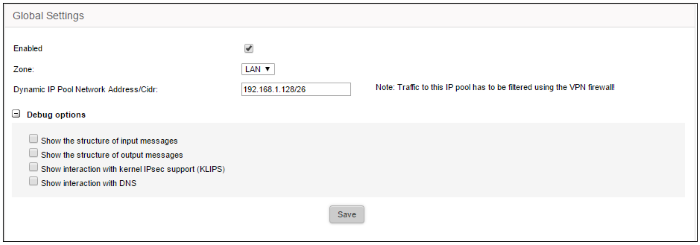
- Enabled – Select the checkbox to enable the IPsec VPN service
- Zone – Choose the internal network zone to allow external clients and networks to access through the IPsec VPN
- Dynamic IP pool network address/cidr – Specify the IP addresses for dynamic assignment to the external clients in CIDR notation
- Debug options – Allows the administrator to configure the level of detail recorded for IPsec events in the debug log file in the event of connection failures. The log file is located at /var/log/messages in the internal storage of the appliance. Click the '+' button to view the list of available options
- Click Save for your settings to take effect
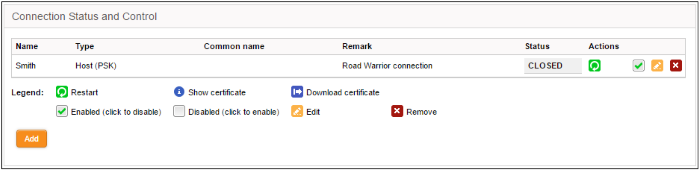
The 'Connection Status and Control' area displays a list of IPsec tunnels that have been added, their connection status and controls for enabling, disabling and editing them.
|
IPsec Connection Status and Control table - Column Descriptions |
|
|---|---|
|
Column |
Description |
|
Name |
The name for identifying the connection. |
|
Type |
Indicates the type of the tunnel and the authentication type used. The IPsec service supports two types of authentication:
|
|
Common Name |
If certificate type authentication is used, the Common Name fields included in the certificate is displayed here. |
|
Remark |
A short description of the tunnel. |
|
Status |
Indicates the connection status of the tunnel. The possible values are:
|
|
Actions |
Displays control buttons for managing the tunnel.
|
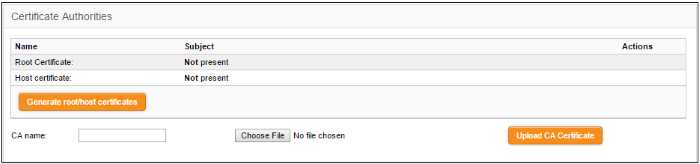
The 'Certificate authorities' area allows the administrator to manage the Root certificate / Host certificate or the server certificate for authentication of remote clients connecting through the IPsec tunnel.
The external client/network can authenticate itself by using a client certificate:
- That was generated by the DCF appliance and sent to the client ;
- Generated by the DCF appliance by signing the certificate request received from the client; or
- Obtained from an external CA.
Initially, no certificate will be available with DCF. If a new tunnel configuration is created with certificate type authentication, the administrator should first generate self-signed root and host certificates or upload a server certificate obtained from an external CA for deployment on to DCF. This certificate will be used to generate a new client certificate for the client or to sign the certificate request received from the client.
The following sections explain on:
To generate new self-signed certificates
- Click 'Generate root/host certificates'. The 'Generate root/host certificates' pane will open. The pane allows the administrator to create a new certificate or upload a previously generated certificated stored locally in PKCS12 format.
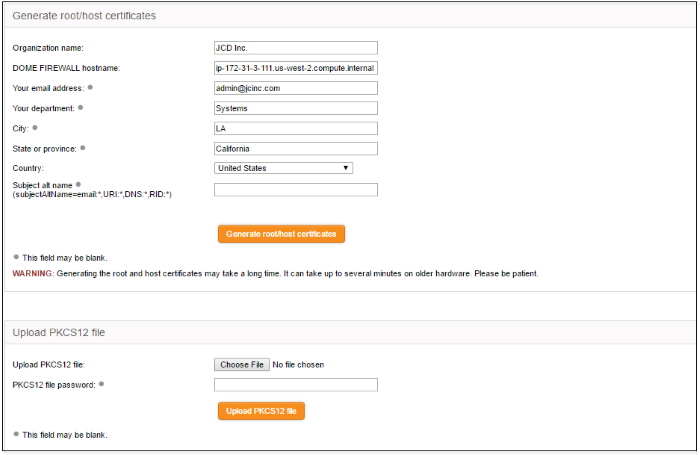
- Organization name – Enter the name of your organization. This will appear in the 'Organization' field of your certificate
- Dome Firewall hostname – Enter the IP address or host name of the Dome Cloud Firewall appliance.
- Your email address – Enter your email address, to be included in the certificate
- Your department – Enter your department. This will appear in the 'Organizational Unit' (OU) field of the certificate
- City – Enter your city
- State or province – Enter your state or province
- Country – Choose your country from the drop-down
- Subject alt name – Enter the alternative host names of the DCF appliance, if any.
- Click 'Generate root/host certificate'
Alternatively, if the administrator has any of the previously generated certificates stored in PKCS12 format, then the certificate can be uploaded to the appliance, instead of creating new certificates.
To upload an existing certificate
- Click the Browse button beside 'Upload PKCS12 file and navigate to the location in the local storage or the network wher the certificate was exported and stored'
- Enter the password entered while exporting the certificate
- Upload PKCS12 certificate.
The certificates will be created and listed under 'Certificate authorities'
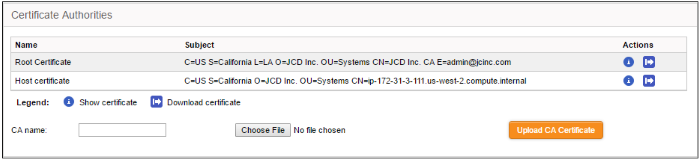
At a time only one certificate can
be stored which serves for a single connection. If a new tunnel need
to be configured, the existing certificate and the connection using
the existing certificate can be removed by resetting the certificate
store. The administrator can view the certificates by clicking the ![]() button or download the certificate by clicking the
button or download the certificate by clicking the ![]() button. The
downloaded certificates can then be exported to PKCS12 format for
importing into the appliance in future.
button. The
downloaded certificates can then be exported to PKCS12 format for
importing into the appliance in future.
To upload server certificate obtained from external CA
- Enter the CA name for identification in the CA name text field.
- Click the Browse button beside the text field and navigate to the location in the local storage or the network where the certificate is stored and click 'Open'.
- Click 'Upload CA certificate'.
The certificate will be imported into DCF.
Adding a New Tunnel Configuration
Three types of IPsec VPN Tunnels
can be created in Comodo Dome Cloud Firewall:
- Host to Net VPN – Enabling mobile and portable computers (a.k.a Road Warriors) to connect to the internal networks
- Net to Net VPN – For connection from external IPsec VPN servers enabling network to network VPN connection
- L2TP Host to Net VPN – Enabling external clients using L2TP clients to connect to the internal networks through IPsec VPN
|
Note: In order to allow L2TP Hosts to connect to the VPN, the L2TP server must be enabled and configured in DCF. See L2TP server Configuration for more details. By default only one connection is allowed at a time for L2TP/IPsec connection. To enable more number to users to connect simultaneously, the L2TP/IPsec user accounts are to be added to the server. See IPsec / L2TP Users Configuration for more details. |
To create a new tunnel
-
Click 'Add' from the 'Connection Status and Control' area in the 'IPsec' interface.
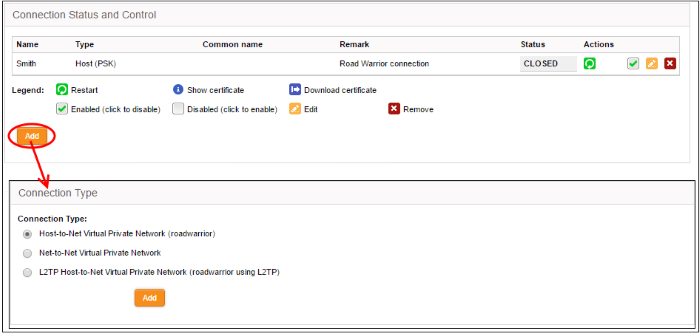
The Connection type interface will open.
-
Choose the connection type and click 'Add'. The interface for specifying the connection configuration parameters and the authentication parameters will open. The interface is similar for all the three types of connection, except for an additional parameter 'Remote subnet', if you are creating Net to Net connection type. The interface contains two areas:
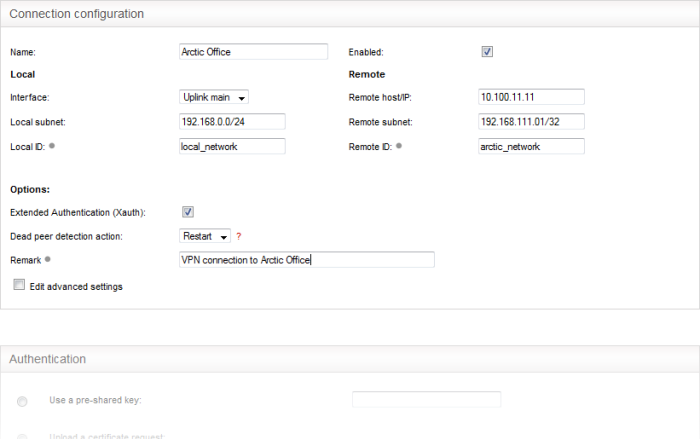
- Name – Enter a name to identify the connection tunnel
- Enabled – Select this checkbox if you wish the tunnel to be enabled upon creation. Do not select this, if you just want to create the connection this time and enable it at a later time.
Local
- Interface – Choose the uplink interface device connected to the DCF appliance, through which the external client should connect to the local network infrastructure
- Local Subnet – This field is auto populated with the local sub network of LAN. If you want to specify a different subnet, enter the address in CIDR format.
- Local ID – Enter an identification string for the local network.
Remote
- Remote host/IP – Enter the IP address or hostname of the external host or network
- Remote subnet – The option is available only if you are creating 'Net to Net' connection type. Specify the sub network of the external network that can connect through the tunnel
- Remote ID - Enter an identification string for the local network.
Options
- Extended Authentication (Xauth) – Select this option if you wish to enable extended certificate based authentication for the remote client. You must install the client certificate on to the external client, if you select this option.
- Dead peer detection action – Choose the action to be taken by the DCF appliance if the peer disconnects. The options available are:
- Clear – Disconnect the connection
- Hold – Wait for the peer to reconnect
- Restart – Restart the peer
- Remark – Enter a short description for the connection
- Edit advanced settings – Select this option if you wish to edit advanced configuration parameters of the tunnel. The advanced parameters can be edited only after saving the tunnel configuration. See the section explaining editing advanced parameters of IPsec tunnel configuration for more details
Authentication
The
'Authentication Settings' area allows the administrator to select the
authentication type. If certificate authentication type is chosen,
the administrator can configure for generating the client certificate
from this area. The certificate will be available for download from
the Connection status
and control area.
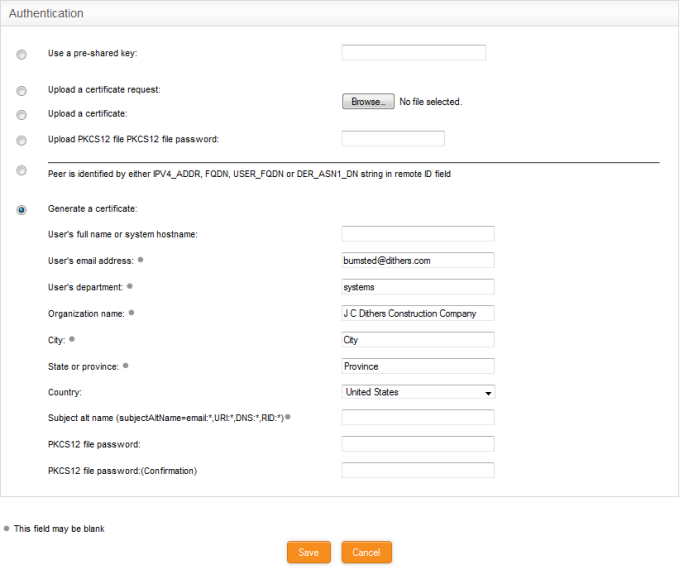
- Select the authentication type from the options available in this interface:
- Use a pre-shared key – Select this option if you wish to apply PSK type authentication for the remote client and enter the password to be used for authentication by the remote client.
|
Warning: It is recommended to not to choose PSK type authentication type for 'Host to Net' connection type. |
The following options are for client certificate type authentication and will be available only if Root and Host certificates are generated or a server certificate obtained from CA has been uploaded for the IPsec server in DCF. See the section Certificate Authority for more details.
- Upload a certificate request – If the IPsec tunnel implementation in the remote host does not have its own CA, a certificate request, which is a partial X.509 certificate can be generated at the host. The certificate request can be transferred to the computer from which the administrative console is accessed and uploaded to DCF. Dome Cloud Firewall will sign the request using its root certificate. The signed client certificate will be available from the Connection status and control area, which can then be transferred to the remote host and deployed. To upload a client certificate request, select this option and click the 'Choose File' button. Navigate to the location where the request file is stored and click 'Open.'
- Upload a certificate – If the remote host already has a client certificate in X.509 format, the certificate can be transferred to the computer from which the administrative console is accessed and uploaded to DCF. To upload the certificate, select this option and click the 'Choose File' button. Navigate to the location where the certificate file is stored and click 'Open.'
- Upload PKCS12 file PKCS12 file password – If the client certificate is exported to PKCS format from the remote host, the .p12 file can be transferred to the computer from which the administrative console is accessed and uploaded to DCF. To upload the certificate, select this option and click the 'Choose File' button. Navigate to the location where the certificate file is stored and click 'Open.'
- Peer is identified by either IPV4_ADDR, FQDN, USER_FQDN or DER_ASN1_DN string in remote ID field - Select this option if you wish the remote host is to be authenticated based on its IP Address, domain name, or by other unique information of the IPsec tunnel entered in the Remote ID field of the Connection Configuration area.
- Generate Certificate – Select this option if you wish to generate a new client certificate for the remote host signed by the Root certificate of IPsec server in DCF. Enter the parameters for the certificate in the fields below. Upon generation, the client certificate will be available for download from the Connection status and control area. The certificate can be transferred to the remote host and deployed for authenticating itself to the server.
- User's full name or system hostname – Enter the username or the hostname of the remote host. This name will be included in the CN field of the certificate.
- User's email address – Enter the email address of the user of the host.
- User's department – Enter the department to which the en-user belongs.
- Organization name – Enter the name of the organization to which the end-user belongs.
- City, State or province, Country – Enter the address details of the end-user
- Subject alt name – Enter the alternative host names, if any, for the remote host.
- PKCS12 file password – Enter the password for storing the certificate file in .p12 format and re-enter it for confirmation in the next field. This password needs to be entered while importing the certificate at the remote host.
- Click 'Save'.
If
you have chosen to edit advanced settings while creating the
connection, the 'Advanced
Connection Parameters'
interface will open after clicking 'Save'. Else, the
connection will be added to the Connection
status and control area. The
certificates generated can be downloaded and imported onto the remote
host. The remote host will now be able to connect to the sub network
of the internal network specified under Connection Configuration, by
configuring the IPsec VPN connection at the host.
Editing Advanced Configuration Parameters of IPsec Tunnel Configuration
|
Warning: The Advanced connection parameters are automatically selected for optimal performance. It is recommended to leave these settings to default, unless you are an expert and understand the risk of altering encryption parameters. |
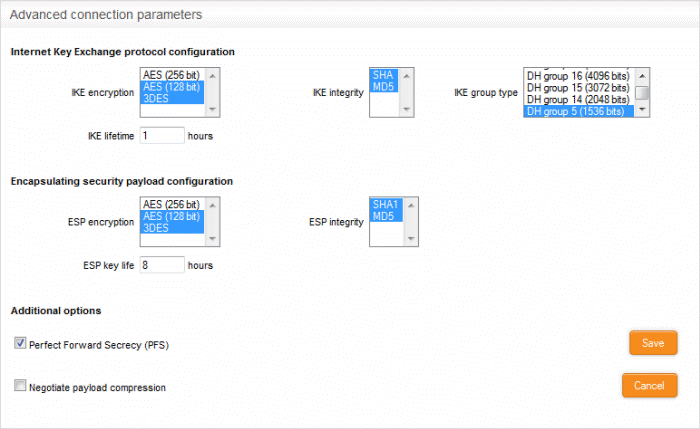
Internet Key Exchange (IKE) Protocol Configuration
- IKE Encryption – Select the encryption method(s) to be supported by IKE.
- IKE Integrity – Select the encryption algorithms to be used for checking the integrity of IKE data packets
- IKE group type – Select the group type of IKE packets
- IKE lifetime – Specify how long the IKE packets are to be valid
Encapsulating security payload configuration
- ESP Encryption – Select the encryption method(s) to be supported for encapsulation.
- ESP Integrity – Select the encryption algorithms to be used for checking the integrity of encapsulated data packets
- ESP key life – Specify how long the encapsulated data packets are to be valid
Additional options
- Perfect Forward Secrecy (PFS) – Select this option to enable perfect forward secrecy, so that the keys exchanged during long-term connection sessions are protected from being compromised.
- Negotiate payload compression – Select this option If you wish to allow compression of payload in data packets.
- Click 'Save' for your configuration to take effect.
The
connection will be added to the Connection
status and control area. The
certificates generated can be downloaded and imported onto the remote
host. The remote host will now be able to connect to the sub network
of the internal network specified under Connection Configuration, by
configuring the IPsec VPN connection at the host.




 - Allows the administrator to switch the
connection between enabled and disabled states.
- Allows the administrator to switch the
connection between enabled and disabled states. - Removes the tunnel configuration.
- Removes the tunnel configuration.