View Contained Threats
Click 'Security' > 'Contained Threats'> 'Containment Logs'
- The container is a secure environment in which files with an 'unknown' trust rating are run. 'Unknown' files have not yet been classified as either 'safe' or 'malware'.
- Contained threats are not permitted to modify files, user data or other processes on the host machine.
- You can also submit unknown applications to Valkyrie, Comodo's file analysis system. Valkyrie will test the file and attempt to classify it as 'safe' or 'malware'.
A threats could be run inside the container because:
- It was auto-contained by rules in the EM configuration profile applied to the endpoint. See 'Containment Settings' in the section Create Windows Profiles for more details about containment rules in a profile.
- It was auto-contained by local Comodo Client Security rules on the endpoint
- The endpoint user ran the program inside the container on a 'one-off' basis. This can be helpful to test the behavior of new executables that have they downloaded.
You can view
all programs that ran inside the container from the 'Containment'
interface. Admins can also view the activity of processes
started by contained threats. Admins have the option to rate a
contained file as trusted or malicious.
Open the containment list interface:
- Click 'Security' > 'Contained Threats'> 'Containment Logs'
- Select a company or group to view contained programs in that group
OrSelect 'Show all' to view all contained programs.
.png)
|
Containment - Column Descriptions |
|
|---|---|
|
Column Heading |
Description |
|
File Name |
The executable that was run in the container.
|
|
File Path |
The location of the contained file on the local endpoint.
|
|
File Hash |
SHA1 hash value of the file.
|
|
Number of Devices |
The quantity of endpoints on which the item was identified.
|
|
Contained By |
The reason the file was contained. |
| Parent Process Name |
The program or service that launched the contained threats. |
|
Action |
The permission level at which the file was executed in the container, or the action that was taken upon it. The possible values are:
|
|
Status |
The execution state of the file inside the container. The possible values are:
|
|
Comodo Rating |
The present trust rating of the file as per the Comodo File Look-up Service (FLS). |
|
Admin Rating |
The trust rating of the file as set by the administrator. Files can be rated as trusted, malicious or unrecognized. |
|
Date and Time |
Date and time the file ran in the contained environment. |
|
Controls |
|
|
File Details |
View full information of the contained file including the devices on which it was contained and its activity. |
|
Change Rating |
You can change the rating of the contained file as trusted, malicious or unrecognized. |
|
Hide file(s) |
Conceal contained file record(s) from the list. |
| Unhide file(s) | Reveal concealed file record(s). |
|
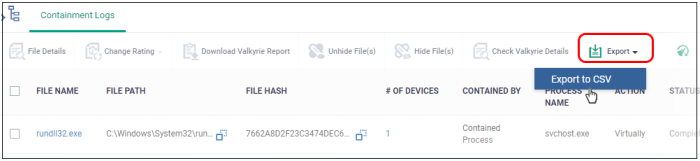
Export |
Export the list of contained files to a .csv file. The exported file can be viewed in 'Dashboard' > 'Reports'. |
|
Download Valkyrie report |
Valkyrie is Comodo's advanced file analysis and verdicting system. Each report contains an in-depth breakdown on the activity an unknown file, along with an overall verdict on its trustworthiness. |
|
Check Valkyrie details |
View Valkyrie file analysis of the contained file at https://valkyrie.comodo.com |
- Click
any column header to sort items in ascending/descending order of
entries in that column.
- Click the
funnel icon
 on the right to search for contained threats by
name, file path, SHA1 file hash, admin rating, action, status
and/or execution date.
on the right to search for contained threats by
name, file path, SHA1 file hash, admin rating, action, status
and/or execution date.
- To display all the items again, remove / deselect the search key from filter and click 'Apply'.
- EM returns 20 results per page when you perform a search. To increase the number of results displayed per page up to 200, click the arrow next to 'Results per page' drop-down and choose the number.
Manage
Contained Items
The 'Containment' interface allows you to:
View details of a contained threats
- Click 'Security' > 'Contained Threats'> 'Containment Logs'
- Select a company or group to view contained programs in that group
Or
- Select 'Show all' to view all contained programs
- Click on a specific file-name in the list OR select a file and click 'File Details'
- This will open the file details interface which shows:
- File Info - General information such as file-name, path, age, hash and file-size.
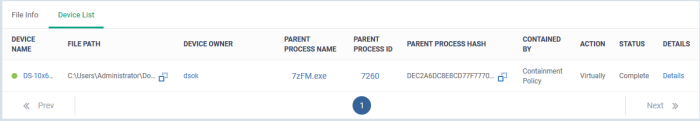
- Device - Shows endpoints upon which the file was found. This tab also tells you the device owner and lists any activities by the file.
- Click 'Security' > 'Contained Threats'> 'Containment Logs'
- Click on a specific file-name in the list OR select a file and click 'File Details'
- Click the 'Device List' tab
Rate files as trusted / malicious
If required, admins can rate contained files as unrecognized, trusted or malicious. Please make sure before marking a file as trusted. Any new file ratings will be sent to endpoints during the next sync.
- Click 'Security' > 'Contained Threats'> 'Containment Logs'
- Select a company or group to view contained programs in that group
Or
- Select 'Show all' to view all contained programs
- Select the file(s) whose rating you wish to change
- Click the 'Change Rating' button
- Set your preferred rating from the options:
.png)
The new rating will be propagated to all endpoints during the next synchronization.
Export
file records as a CSV file
- Select a company or group to view contained programs in that group
Or
- Select 'Show all' to view all contained programs
- Click
the funnel
 icon to filter which records are included in the
report.
icon to filter which records are included in the
report.
- Click the 'Export' button and choose 'Export to CSV':
The report is generated in .csv file format.
You can access the report in the 'Dashboard' > 'Reports' interface. See Reports if you need more help with this interface.
- You can hide records of contained threats from the list. For example, you can hide unimportant hash records.
Hide contained file record(s)
- Click 'Security' > 'Contained Threats'> 'Containment Logs'
- Select a company or group to view contained programs in that group
Or
- Select 'Show all' to view all contained programs
- Select the files that you want to hide and click 'Hide file(s)'
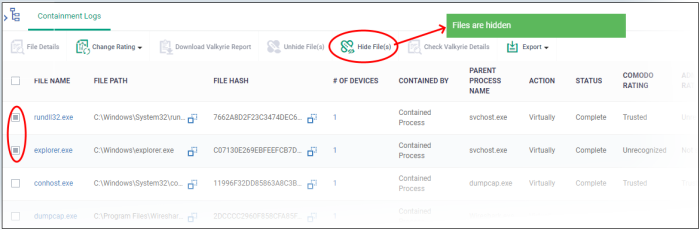
To view the hidden files again, you have to unhide them.
- Click 'Security' > 'Contained Threats'> 'Containment Logs'
- Select a company or group to view contained programs in that group
Or
- Select 'Show all' to view all contained programs
- Click
the funnel icon
 on the right, select 'Show hidden files' and click
'Apply'
on the right, select 'Show hidden files' and click
'Apply'
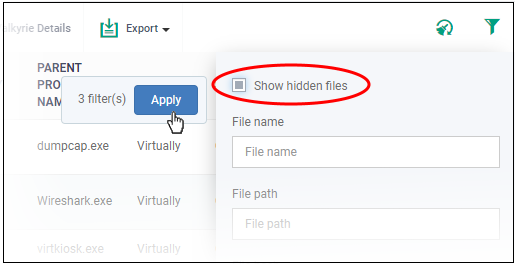
- The hidden files are shown with dark gray background stripe.
- Select the hidden files from the list and click 'Unhide file(s)'
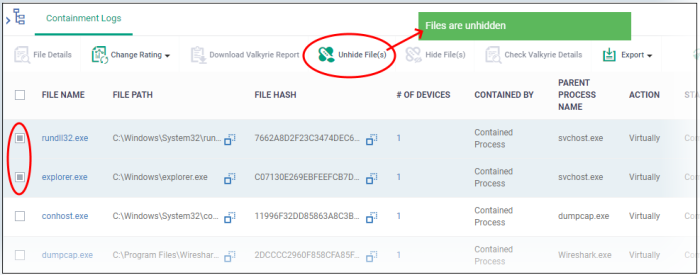
A confirmation message is displayed. The files are re-added to the list.
Valkyrie Reports
Files running in the container are analyzed and rated by Comodo's behavior analysis system, Valkyrie. Valkyrie tests unknown files with a range of static and dynamic behavioral checks to identify whether they are malicious or safe.
You can view the file rating in the 'Application Control' interface also. You can download a Valkyrie report or view it online at https://valkyrie.comodo.com/
- Click 'Security' > 'Contained Threats'> 'Containment Logs'
- Select a company or group to view contained programs in that group
Or
- Select 'Show all' to view all contained programs
- Select any file
- Click 'Download Valkyrie report':
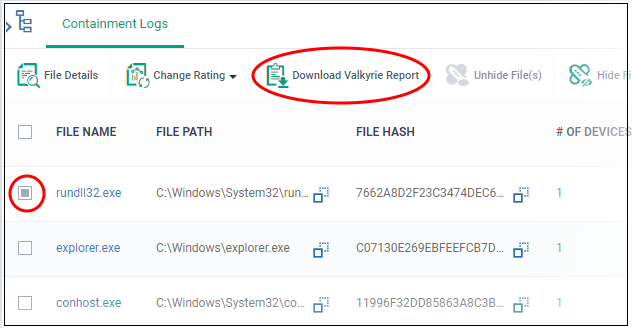
This will open the Valkyrie report on the contained file in PDF format:
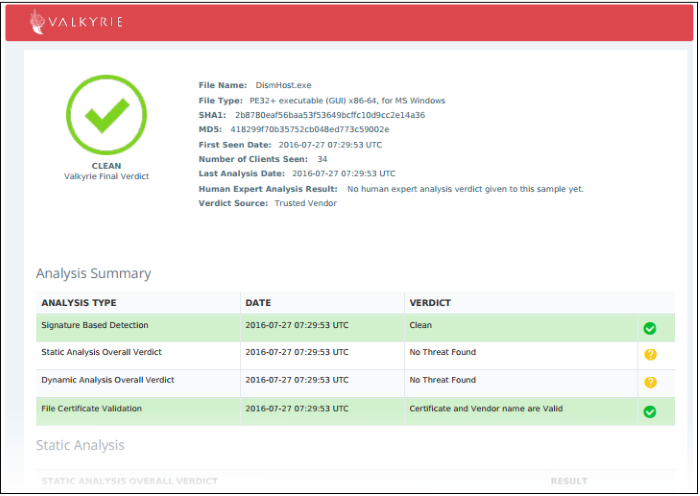
You can also download and view the report at https://valkyrie.comodo.com/ after signing into your Valkyrie account.
View Valkyrie fie analysis report online
- Select the file from the list and click 'Check Valkyrie Details' at the top.
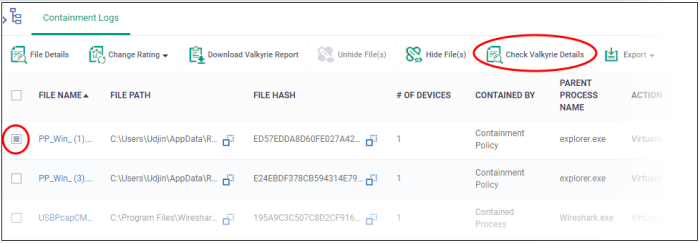
You will be taken to the report summary page of the selected file at https://valkyrie.comodo.com/.
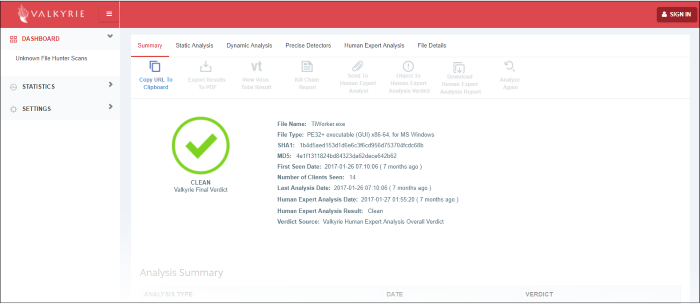
- View a more detailed version of the Valkyrie analysis by logging in at https://valkyrie.comodo.com/. You can use your Comodo One username and password to login.
- See https://help.comodo.com/topic-397-1-773-9563-Introduction-to-Comodo-Valkyrie.html for help to use the Valkyrie online portal.



