Introduction to Endpoint Manager
Endpoint Manager (EM) lets you manage, monitor and secure devices which connect to your network.
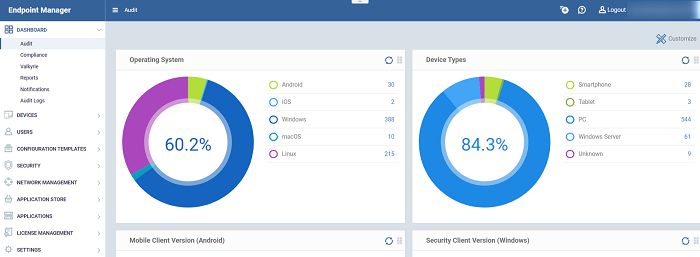
- Admins must first add users to EM then enroll devices/endpoints for those users. Supported operating systems include Android, iOS, Mac OS, Windows and Linux.
- Once
a device has been added, admins can apply profiles which determine
the device's network access rights, security settings and other
features.
- Each license covers one device per user. You will need additional licenses for each device you add for a user.
Guide
Structure
This guide will take you through
the configuration and use of Endpoint Manager
and is broken down into the following sections:
The Administrative Console
The Dashboard
Devices and Device Groups
Users and User Groups
Configuration Templates
Security Systems
Network Management Application Store
- Security Events
- View Security Events By Time
- View Security Events By Files
- View Security Events By Device
- View Android Threat History
- View And Manage Blocked Threats
- View And Manage Quarantined Threats
- View Contained Threats
- View And Manage Autorun Alerts
License Management
Configure Endpoint Manager
Appendix 1b: Endpoint Services - IP Nos, Host Names and Port Details - US Customers
Appendix 2 - Endpoint Manager License Types
Appendix 3: Pre-configured Profiles



