Create Rules for Auto-Containing Applications
CCS ships with a set of pre-defined auto-containment rules that are configured to provide maximum protection for your system. Before creating a rule, first check if your requirement is met by the default rules. Refer to the section Configuring Rules For Auto-Containment for more details.
To create auto-containment rules
2. Open 'Containment Tasks' then click 'Open Advanced Settings'.
3. Click 'Security Settings' > 'Advanced Protection' > 'Containment' > 'Auto-Containment' on the left hand menu.
4. Click the handle at the bottom of the interface to open the option panel:
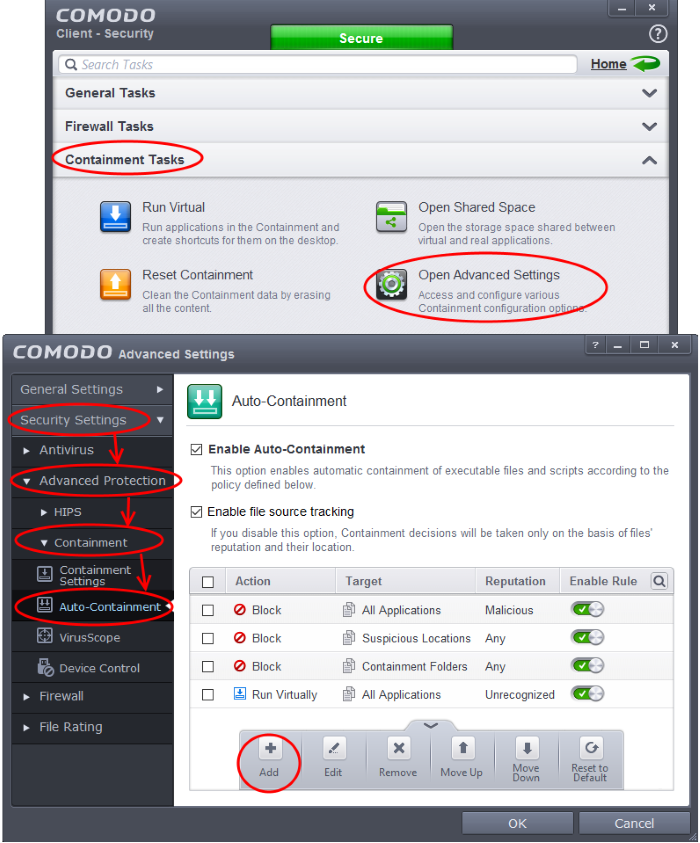
-
Click the 'Add' button
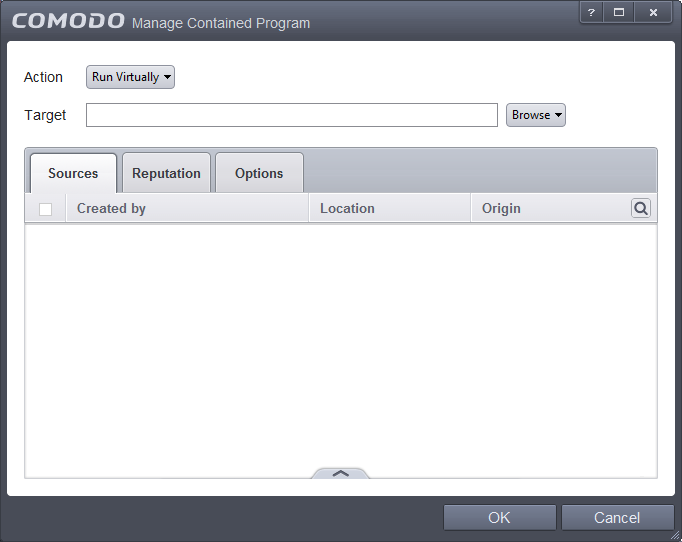
The 'Manage Contained Program' screen will appear:
- Step 1 – Select the Action
- Step 2 – Select the Target
- Step 3 – Select the Sources
- Step 4 – Select the File Reputation
- Step 5 – Select the Options
The options in the 'Action' drop-down button combined with the 'Set Restriction Level' setting in the 'Options' tab determine the privileges a contained application has to access other software and hardware resources on your computer.
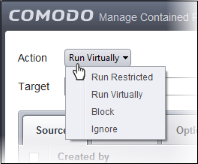
The
options available are:
- Run Virtually - The application will be run in a container, completely isolated from your operating system and files on the rest of your computer.
- Run Restricted - The application is allowed to access very few operating system resources. The application is not allowed to execute more than 10 processes at a time and is run with very limited access rights. Some applications, like computer games, may not work properly under this setting.
- Block - The application is not allowed to run at all.
- Ignore - The application will not be contained and is allowed to run with all privileges.
The next step is to select the target to which the auto-containment rule should be applied. Click the 'Browse' button beside the 'Target' field.
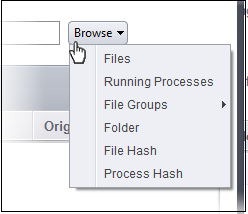
You have six options available to add the target path:
- Files – Specify individual files as targets of the rule.
- Running Processes – Add any process that is currently running on your computer as a target of the rule.
- File Groups – Add predefined file groups as the rule target. For information about creating or modifying a predefined file group, refer to File Groups for more details.
- Folder – Allows you to add a folder or drive as the target
- File Hash – Allows you to add a file as target based on its hash value
- Process Hash - Allows you to add any process that is currently running on your computer as a target based on its hash value
Click here to know more about adding each of the options.
If you want to include a number of items in a rule but want the rule to be applied only in certain conditions, then you can do so in this step. For example, if you want your target to be executables downloaded from the internet, then you would add 'All Applications' then apply a filter in 'Sources' tab. Another example is you want to exclude from containment any unrecognized files from your internal network share. You could create an ignore rule with 'All Applications' set as the target and specify your source as your intranet.
Please note that the 'Enable file source tracking' check box should be enabled in the 'Auto-Containment' screen for the source parameter to be taken account in the rule. If this is not enabled then the source parameter will be ignored and the rule will be applied based on the other parameters.
The following example describes how to add an 'Ignore' rule for Unrecognized files from a network source:
- In Step 1, select the action as Ignore
- In Step 2, select the Target as File Groups > All Applications
- In Step 3, click the 'Add' button and select 'Folder'. Navigate to the source folder on the network and click 'OK'.
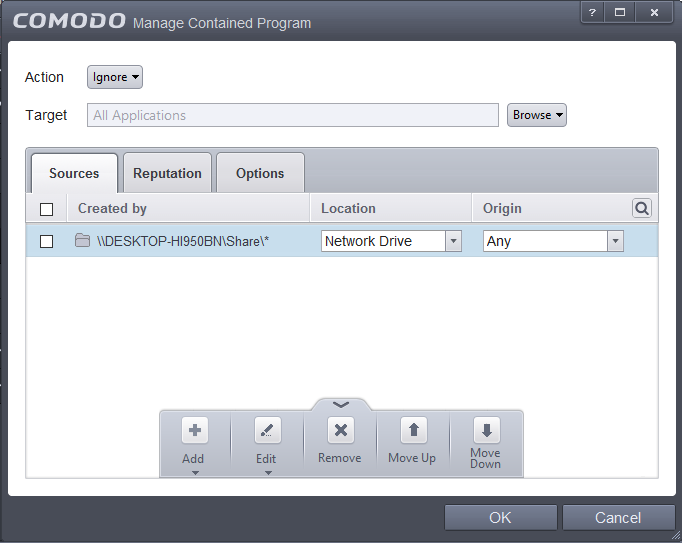
The selected network source folder will be added under the 'Created by' column and the screen displays the options to specify the location and from where the files were downloaded.
- Location – Apply the rule to files found in one of the following locations:
- Any
- Local Drive
- Removable Drive
- Network Drive
Since the source is located in a network, select Network Drive from the options.
- Origin – The options available are:
- Any – The rule will apply to files that were downloaded to the source folder from both Internet and Intranet.
- Internet – The rule will apply to files that were downloaded to the source folder from Internet only.
- Intranet – The rule will apply to files that were downloaded to the source folder from Intranet only.
Since the example rule is created for files that are categorized as Unrecognized, the same has to be selected from the rating options in Step 4.
Step 4 – Select the File Reputation
-
Click the Reputation tab in the 'Manage Contained Program' interface.
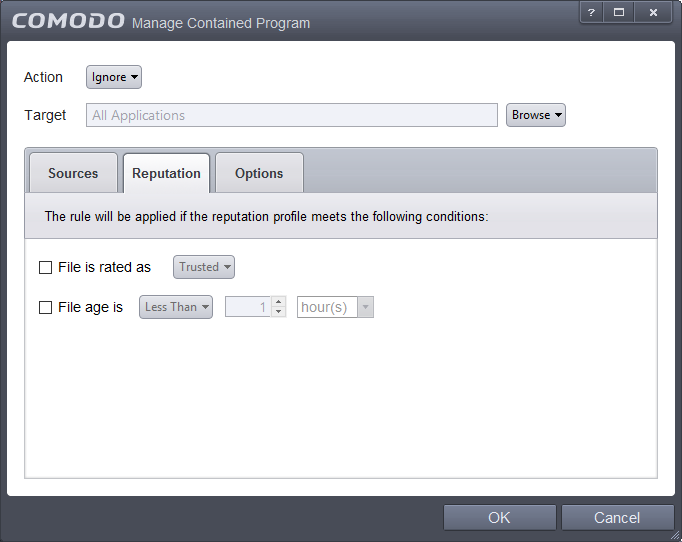
By default, the file rating is not selected meaning the rating could be Any. The options available are:
- Trusted – Applications that are signed by trusted vendors and files installed by trusted installers are categorized as Trusted files by CCS. Refer to the sections File Rating Settings and File List for more information.
- Unrecognized – Files that are scanned against the Comodo safe files database not found in them are categorized as Unrecognized files. Refer to the section File List for more information.
- Malware – Files are scanned according to a set procedure and categorized as malware if not satisfying the conditions. Refer the section Unknown Files – The Scanning Process for more information.
By default, file age is not selected, so the age could be Any. The options available are:
- Less Than – CCS will check for reputation if a file is younger than the age you set here. Select the interval in hours or days from the first drop-down combo box and set hours or days in the second drop-down box. (Default and recommended = 1 hours)
- More Than - CCS will check for reputation if a file is older than the age you set here. Select the interval in hours or days from the first drop-down combo box and set hours or days in the second drop-down box. (Default and recommended = 1 hours)
Select the category from the options. Since the example rule is created for files that are categorized as Unrecognized, the same has to be selected from the rating options.
-
Click the 'Options' tab in the 'Manage Contained Program' interface.
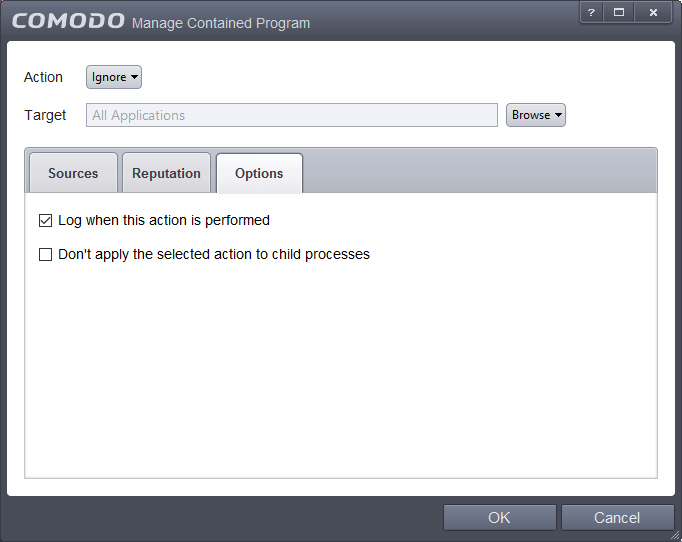
By default, the 'Log when this action is performed' The options available for Ignore action are:
- Log when this action is performed – Whenever this rule is applied for the action, it will be logged.
- Don't apply the selected action to child processes – Child processes are the processes initiated by the applications. For example, the process may launch another app or plugin. CCS treats all child processes as individual processes and forces them to run as per their file rating and the containment rules.
- This option is disabled by default, so the ignore rule will usually be applied to all child process of the target application(s).
- If this option is enabled, then the Ignore rule will be applied only to the target application. All child processes will be checked individually and containment rules applied as per the child's file rating.
- The 'Don't apply to child processes' option is available only for the 'Ignore' action. For 'Run Restricted' and 'Run Virtually', the following options are available:
- Log when this action is performed – Whenever this rule is applied for the action, it will be logged.
- Set Restriction Level – When Run Restricted is selected in Action, then this option is automatically selected and cannot be unchecked while for Run Virtually action the option can be checked or unchecked. The options for Restriction levels are:
- Partially Limited - The application is allowed to access all operating system files and resources like the clipboard. Modification of protected files/registry keys is not allowed. Privileged operations like loading drivers or debugging other applications are also not allowed. (Default)
- Limited - Only selected operating system resources can be accessed by the application. The application is not allowed to execute more than 10 processes at a time and is run without Administrator account privileges.
- Restricted - The application is allowed to access very few operating system resources. The application is not allowed to execute more than 10 processes at a time and is run with very limited access rights. Some applications, like computer games, may not work properly under this setting.
- Untrusted - The application is not allowed to access any operating system resources. The application is not allowed to execute more than 10 processes at a time and is run with very limited access rights. Some applications that require user interaction may not work properly under this setting.
- Limit maximum memory consumption to – Enter the memory consumption value in MB that the process should be allowed.
- Limit program execution time to – Enter the maximum time in seconds the program should run. After the specified time, the program will be terminated.
For Block action, the following options are available:
- Log when this action is performed – Whenever this rule is applied for the action, it will be logged.
- Quarantine program – If checked, the programs will be automatically quarantined. Refer to the section Manage Quarantined Items for more information.
Choose the options and click 'OK'. The rule will be added and displayed in the list.
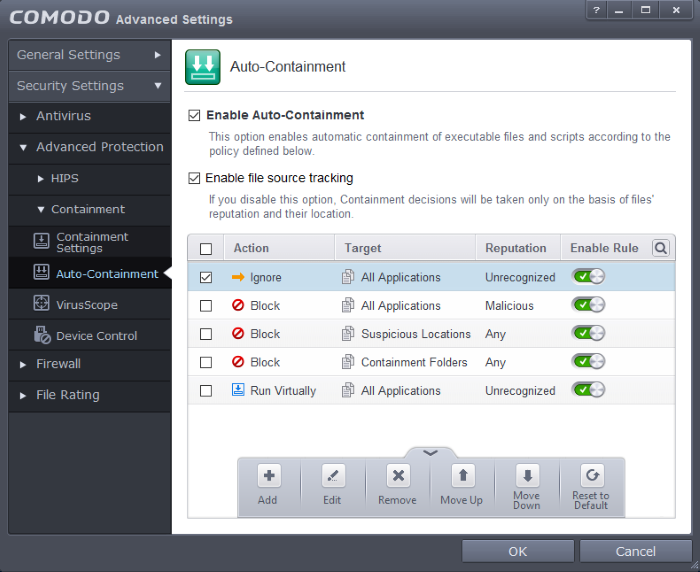
That's it. You have created an Ignore auto-containment rule for unrecognized files with a Network drive as source.



