Firewall Logs
CCS
records a history of all actions taken by the firewall. Firewall
'Events' are generated and recorded for various reasons - including
whenever an application or process makes a connection attempt that
contravenes a rule in your Rule sets or whenever there is a change in Firewall configuration.
The Firewall logs can be viewed by selecting 'Firewall Events' from the 'Show' drop-down of the log viewer interface.
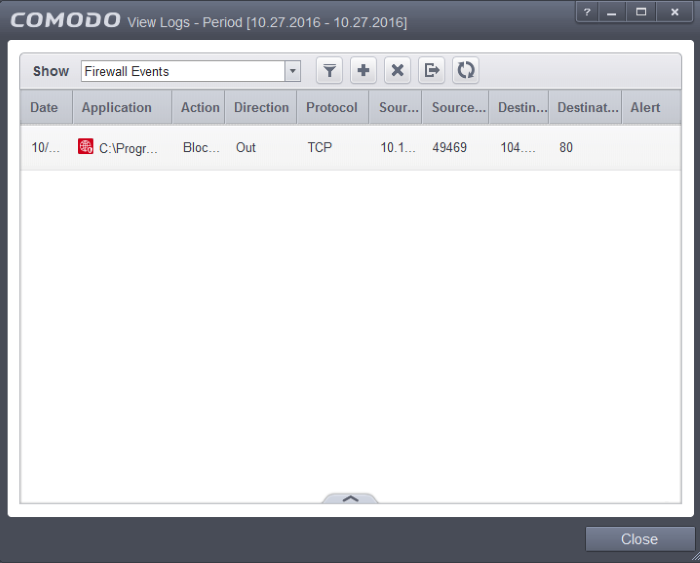
Column Descriptions
-
Date - Contains precise details of the date and time of the connection attempt.
-
Application - Indicates which application or process propagated the event. If the application has no icon, the default system icon for executable files are used
-
Action - Contains the flags attached to the events, indicating how the firewall has reacted to the connection attempt.
-
Direction - Indicates whether the connection attempt is inbound or outbound.
-
Protocol - Represents the Protocol used by the application that attempted to create the connection. This is usually TCP/IP or UDP - which are the most heavily used networking protocols.
-
Source IP - States the IP address of the host that made the connection attempt. This is usually the IP address of your computer for outbound connections.
-
Source Port - States the port number on the host at the source IP which was used to make this connection attempt.
-
Destination IP - States the IP address of the host to which the connection attempt was made. This is usually the IP address of your computer for inbound connections.
-
Destination Port - States the port number on the host at the destination IP to which the connection attempt was made.
-
Alert - Gives the details of the alert displayed for the event
- To export the Firewall logs as a HTML file click the 'Export' button
 .
.
- To open a stored CCS log file, click the 'Open' button
 .
.
- To refresh the Firewall logs, click the 'Refresh' button
 .
.
- To clear the Firewall logs click the 'Clear' button
 .
.



