HIPS Behavior Settings
HIPS constantly monitors system activity and only allows executables and processes to run if they comply with the prevailing security rules that have been enforced by the user. For the average user, Comodo Client Security ships with a default HIPS ruleset that works 'out of the box' - providing extremely high levels of protection without any user intervention. For example, HIPS automatically protects system-critical files, folders and registry keys to prevent unauthorized modifications by malicious programs. Advanced users looking to take a firmer grip on their security posture can quickly create custom policies and rulesets using the powerful rules interface.
|
Note for beginners: This page often refers to 'executables' (or 'executable files'). An 'executable' is a file that can instruct your computer to perform a task or function. Every program, application and device you run on your computer requires an executable file of some kind to start it. The most recognizable type of executable file is the '.exe' file. (e.g., when you start Microsoft Word, the executable file 'winword.exe' instructs your computer to start and run the Word application). Other types of executable files include those with extensions .cpl .dll, .drv, .inf, .ocx, .pf, .scr, .sys.
Unfortunately, not all executables can be trusted. Some executables, broadly categorized as malware, can instruct your computer to delete valuable data; steal your identity; corrupt system files; give control of your PC to a hacker and much more. You may also have heard these referred to as Trojans, scripts and worms. |
- The HIPS Settings panel allows you to enable/disable HIPS, set its security level and configure its general behavior.
- The HIPS Settings panel can be accessed by clicking 'Advanced Settings' > 'Security Settings' > 'Advanced Protection' > 'HIPS' > 'HIPS Settings'
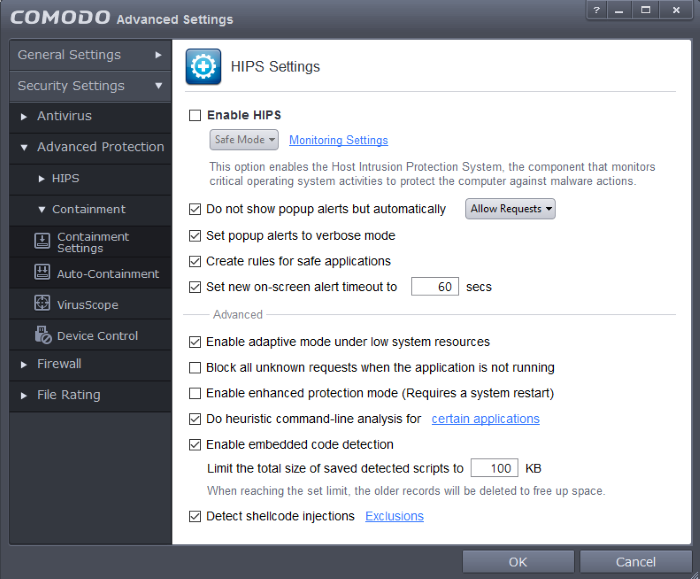
If enabled, you can choose the security level and configure the monitoring settings for the HIPS component.
Configuring Security Level of HIPS
The security level can be chosen from the drop-down that becomes active only on enabling HIPS:
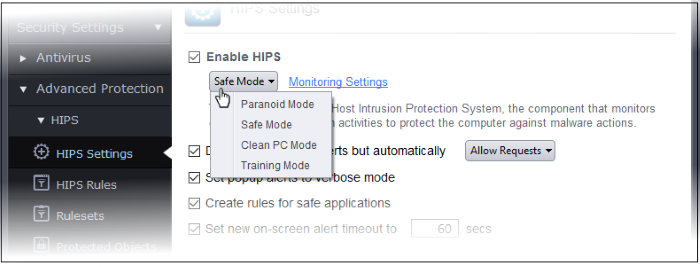
The choices available are:
-
Paranoid Mode: This is the highest security level setting and means that 'Advanced Protection' monitors and controls all executable files apart from those that you have deemed safe. Comodo Client Security does not attempt to learn the behavior of any applications - even those applications on the Comodo safe list and only uses your configuration settings to filter critical system activity. Similarly, the Comodo Client Security does automatically create 'Allow' rules for any executables - although you still have the option to treat an application as 'Trusted' at the HIPS alert. Choosing this option generates the most amount of HIPS alerts and is recommended for advanced users that require complete awareness of activity on their system.
-
Safe Mode: While monitoring critical system activity, 'Advanced Protection' automatically learns the activity of executables and applications certified as 'Safe' by Comodo. It also automatically creates 'Allow' rules these activities, if the checkbox 'Create rules for safe applications' is selected. For non-certified, unknown, applications, you will receive an alert whenever that application attempts to run. Should you choose, you can add that new application to the safe list by choosing 'Treat this application as a Trusted Application' at the alert. This instructs 'Advanced Protection' not to generate an alert the next time it runs. If your machine is not new or known to be free of malware and other threats as in 'Clean PC Mode' then 'Safe Mode' is recommended setting for most users - combining the highest levels of security with an easy-to-manage number of HIPS alerts.
-
Clean PC Mode: From the time you set the slider to 'Clean PC Mode', 'Advanced Protection' learns the activities of the applications currently installed on the computer while all new executables introduced to the system are monitored and controlled. This patent-pending mode of operation is the recommended option on a new computer or one that the user knows to be clean of malware and other threats. From this point onwards HIPS alerts the user whenever a new, unrecognized application is being installed. In this mode, the files with 'Unrecognized' rating in the 'File List' are excluded from being considered as clean and are monitored and controlled.
-
Training Mode: 'Advanced Protection' monitors and learn the activity of any and all executables and create automatic 'Allow' rules until the security level is adjusted. You do not receive any HIPS alerts in 'Training Mode'. If you choose the 'Training Mode' setting, we advise that you are 100% sure that all applications and executables installed on your computer are safe to run.
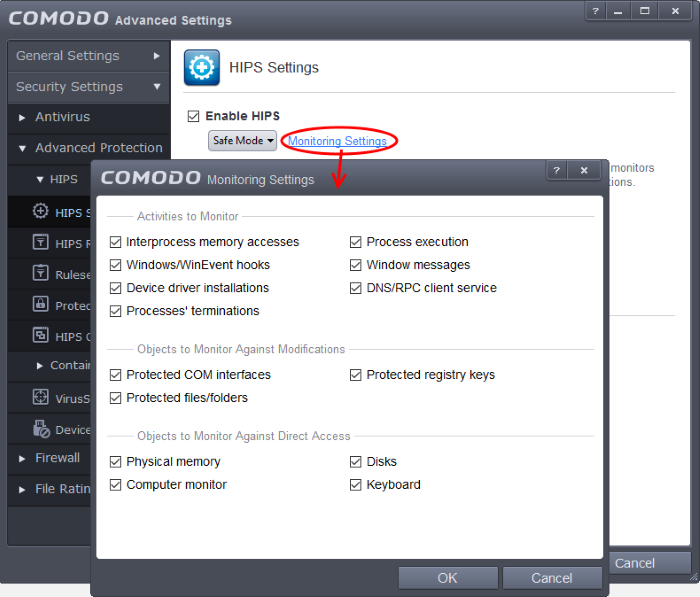
Configuring the Monitoring Settings
The activities, entities and objects that should monitored by HIPS can be configured by clicking the Monitoring Settings link.
|
Note: The settings you choose here are universally applied. If you disable monitoring of an activity, entity or object using this interface it completely switches off monitoring of that activity on a global basis - effectively creating a universal 'Allow' rule for that activity . This 'Allow' setting over-rules any Ruleset specific 'Block' or 'Ask' setting for that activity that you may have selected using the 'Access Rights' and 'Protection Settings' interface. |
-
Interprocess Memory Access - Malware programs use memory space modification to inject malicious code for numerous types of attacks, including recording your keyboard strokes; modifying the behavior of the invaded application; stealing confidential data by sending confidential information from one process to another process etc. One of the most serious aspects of memory-space breaches is the ability of the offending malware to take the identity of the invaded process, or 'impersonate' the application under attack. This makes life harder for traditional virus scanning software and intrusion-detection systems. Leave this box checked and HIPS alerts you when an application attempts to modify the memory space allocated to another application. (Default = Enabled)
-
Windows/WinEvent Hooks - In the Microsoft Windows® operating system, a hook is a mechanism by which a function can intercept events (messages, mouse actions, keystrokes) before they reach an application. The function can act on events and, in some cases, modify or discard them. Originally developed to allow legitimate software developers to develop more powerful and useful applications, hooks have also been exploited by hackers to create more powerful malware. Examples include malware that can record every stroke on your keyboard; record your mouse movements; monitor and modify all messages on your computer; take over control of your mouse and keyboard to remotely administer your computer. Leaving this box checked means that you are warned every time a hook is executed by an untrusted application. (Default = Enabled)
-
Device Driver Installations - Device drivers are small programs that allow applications and/or operating systems to interact with a hardware device on your computer. Hardware devices include your disk drives, graphics card, wireless and LAN network cards, CPU, mouse, USB devices, monitor, DVD player etc. Even the installation of a perfectly well-intentioned device driver can lead to system instability if it conflicts with other drivers on your system. The installation of a malicious driver could, obviously, cause irreparable damage to your computer or even pass control of that device to a hacker. Leaving this box checked means HIPS alerts you every time a device driver is installed on your machine by an untrusted application. (Default = Enabled)
-
Processes' Terminations - A process is a running instance of a program. (for example, the Comodo Client Security process is called 'CCS.exe'. Press 'Ctrl+Alt+Delete' and click on 'Processes' to see the full list that are running on your system). Terminating a process, obviously, terminates the program. Viruses and Trojan horses often try to shut down the processes of any security software you have been running in order to bypass it. With this setting enabled, 'Advanced Protection' monitors and alerts you to all attempts by an untrusted application to close down another application. (Default = Enabled)
-
Process Execution - Typical malware like rootkits, keylogger etc. would often invoke by itself and runs its process mostly at the background. These processes, invisible at the foreground will act as agents for infecting your computer and to steal your confidential and sensitive information like your credit card details and passwords and pass to hackers. With this setting enabled, the HIPS monitors and alerts you to whenever a process is invoked by an untrusted application. (Default = Enabled)
-
Windows Messages - This setting means Comodo Client Security monitors and detects if one application attempts to send special Windows Messages to modify the behavior of another application (e.g. by using the WM_PASTE command). (Default = Enabled)
-
DNS/RPC Client Service - This setting alerts you if an application attempts to access the 'Windows DNS service' - possibly in order to launch a DNS recursion attack.A DNS recursion attack is a type of Distributed Denial of Service attack whereby an malicious entity sends several thousand spoofed requests to a DNS server. The requests are spoofed in that they appear to come from the target or 'victim' server but in fact come from different sources - often a network of 'zombie' pc's which are sending out these requests without the owners knowledge. The DNS servers are tricked into sending all their replies to the victim server - overwhelming it with requests and causing it to crash. Leaving this setting enabled prevents malware from using the DNS Client Service to launch such an attack. (Default = Enabled)
|
Background Note: DNS stands for Domain Name System. It is the part of the Internet infrastructure that translates a familiar domain name, such as 'example.com' to an IP address like 123.456.789.04. This is essential because the Internet routes messages to their destinations on the basis of this destination IP address, not the domain name. Whenever you type a domain name, your Internet browser contacts a DNS server and makes a 'DNS Query'. In simplistic terms, this query is 'What is the IP address of example.com?'. Once the IP address has been located, the DNS server replies to your computer, telling it to connect to the IP in question. |
Objects To Monitor Against Modifications:
-
Protected COM Interfaces enables monitoring of COM interfaces you specified from the COM Protection pane. (Default = Enabled).
-
Protected Registry Keys enables monitoring of Registry keys you specified from the Registry Protection pane. (Default = Enabled).
-
Protected Files/Folders enables monitoring of files and folders you specified from the File Protection pane. (Default = Enabled)
Objects To Monitor Against Direct Access:
Determines whether or not Comodo Client Security should monitor access to system critical objects on your computer. Using direct access methods, malicious applications can obtain data from a storage devices, modify or infect other executable software, record keystrokes and more. Comodo advises the average user to leave these settings enabled:
-
Physical Memory: Monitors your computer's memory for direct access by an applications and processes. Malicious programs attempt to access physical memory to run a wide range of exploits - the most famous being the 'Buffer Overflow' exploit. Buffer overruns occur when an interface designed to store a certain amount of data at a specific address in memory allows a malicious process to supply too much data to that address. This overwrites its internal structures and can be used by malware to force the system to execute its code. (Default = Enabled)
-
Computer Monitor: Comodo Client Security raises an alert every time a process tries to directly access your computer monitor. Although legitimate applications sometimes require this access, there is also an emerging category of spyware programs that use such access to monitor users' activities. (for example, to take screen shots of your current desktop; to record your browsing activities etc). (Default = Enabled)
-
Disks: Monitors your local disk drives for direct access by running processes. This helps guard against malicious software that need this access to, for example, obtain data stored on the drives, destroy files on a hard disk, format the drive or corrupt the file system by writing junk data. (Default = Enabled)
-
Keyboard: Monitors your keyboard for access attempts. Malicious software, known as 'key loggers', can record every stroke you make on your keyboard and can be used to steal your passwords, credit card numbers and other personal data. With this setting checked, Comodo Client Security alerts you every time an application attempts to establish direct access to your keyboard. (Default = Enabled)
Checkbox Options
-
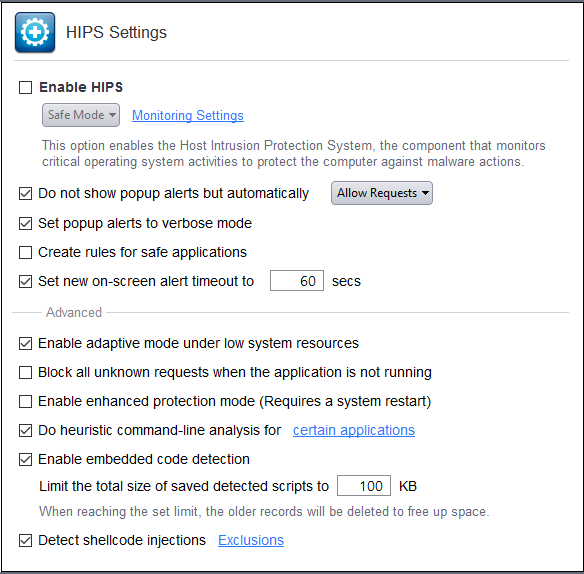
Do NOT show popup alerts - Configure whether or not you want to be notified when the HIPS encounters a malware. Choosing 'Do NOT show popup alerts' will minimize disturbances but at some loss of user awareness. (Default = Enabled)
If you choose not to show alerts then you have a choice of default responses that CCS should automatically take – either 'Block Requests' or 'Allow Requests'.
-
Set popup alerts to verbose mode - Enabling this option instructs CCS to display HIPS Alerts in verbose mode, providing more more informative alerts and more options for the user to allow or block the requests. (Default = Enabled)
- Create rules for safe applications - Automatically creates rules for safe applications in HIPS Ruleset. (Default = Enabled)
|
Note: HIPS trusts the applications if:
|
By default, CCS does not automatically create 'allow' rules for safe applications. This helps saving the resource usage, simplifies the rules interface by reducing the number of 'Allowed' rules in it, reduces the number of pop-up alerts and is beneficial to beginners who find difficulties in setting up the rules.
Enabling this checkbox instructs CCS to begin learning the behavior of safe applications so that it can automatically generate the 'Allow' rules. These rules are listed in the HIPS Rules interface. The Advanced users can edit / modify the rules as they wish.
|
Background Note: CCS automatically adds an allow rule for 'safe' files to the rules interface. This allows advanced users to have granular control over rules but could also lead to a cluttered rules interface.The constant addition of these 'allow' rules and the corresponding requirement to learn the behavior of applications that are already considered 'safe' also takes a toll on system resources. In this version, 'allow' rules for applications considered 'safe' are not automatically created - simplifying the rules interface and cutting resource overhead with no loss in security. Advanced users can re-enable this setting if they require the ability to edit rules for safe applications. |
-
Set new on-screen alert time out to: Determines how long the HIPS shows an alert for without any user intervention. By default, the timeout is set at 120 seconds. You may adjust this setting to your own preference.
Advanced HIPS Settings
-
Enable adaptive mode under low system resources - Very rarely (and only in a heavily loaded system), low memory conditions might cause certain CCS functions to fail. With this option enabled, CCS will attempt to locate and utilize memory using adaptive techniques so that it can complete its pending tasks. However, the cost of enabling this option may be reduced performance in even lightly loaded systems. (Default = Enabled)
-
Block all unknown requests if the application is closed - Selecting this option blocks all unknown execution requests if Comodo Client Security is not running/has been shut down. This is option is very strict indeed and in most cases should only be enabled on seriously infested or compromised machines while the user is working to resolve these issues. If you know your machine is already 'clean' and are looking just to enable the highest CCS security settings then it is 'OK' to leave this box unchecked. (Default = Disabled)
- Enable enhanced protection mode - On 64 bit systems, enabling this mode will activate additional host intrusion prevention techniques to countermeasure extremely sophisticated malware that tries to bypass regular countermeasures. Because of limitations in Windows 7/8 x64 systems, some HIPS functions in previous versions of CCS could theoretically be bypassed by malware. Enhanced Protection Mode implements several patent-pending ways to improve HIPS. CCS requires a system restart for enabling enhanced protection mode. (Default = Disabled)
-
Do heuristic command-line analysis for certain applications - If enabled, CCS will perform heuristic analysis on programs that are capable of executing code. Code that is executed includes visual basic scripts and java applications. Example programs that are affected by this option are wscript.exe, cmd.exe, java.exe and javaw.exe. For example, the program wscipt.exe can be made to execute visual basic scripts (.vbs file extension) via a command similar to 'wscript.exe c:/tests/test.vbs'. If this option is selected, CCS detects c:/test/stest.vbs from the command-line and applies all security checks based on this file. If test.vbs attempts to connect to the Internet, for example, the alert will state 'test.vbs' is attempting to connect to the internet. (Default = Enabled)
-
If this option is disabled, the alert would only state 'wscript.exe' is trying to connect to the Internet'.
|
Background note: 'Heuristics' describes the method of analyzing a file to ascertain whether it contains codes typical of a virus. Heuristics is about detecting virus-like behavior or attributes rather than looking for a precise virus signature that matches a signature on the virus blacklist. This helps to identify previously unknown (new) viruses. |
Click the 'certain applications' link to view the list of programs that are included by default:
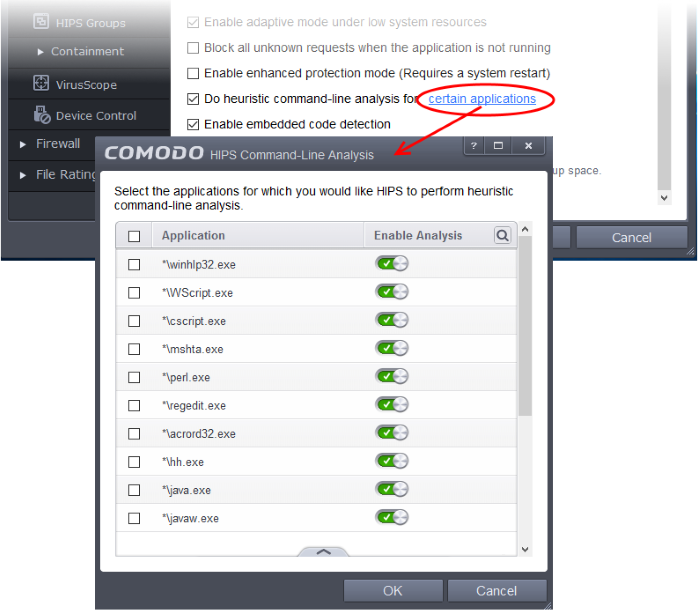
- Application - List of applications which will be analyzed, including defined custom applications.
- Enable Analysis – Enabledisable command-line analysis for a particular application(s)
To manually add a new application to the list for analysis
- Click the handle at the bottom
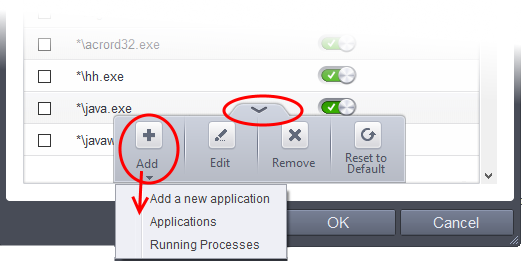
You can add an application using any of the following methods:
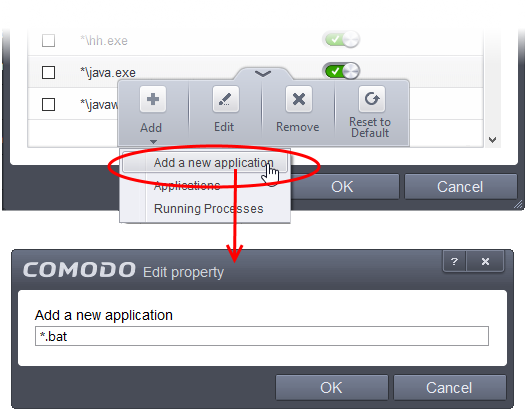
- Click the 'Add' button at the bottom of the list then select 'Add new application'
- Type the name of the application or extension in the 'Edit Property'
- Click 'OK' to apply your changes
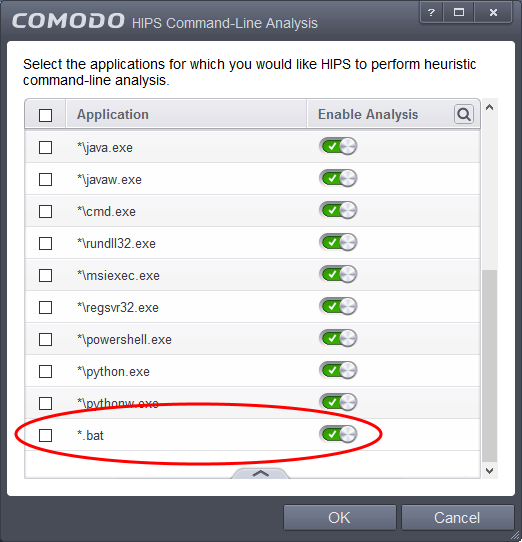
The application will be added and displayed in the list:
- Click the 'Add' button at the bottom of the list then select 'Applications'
- Navigate to the file you want to add in the 'Open' dialog and click 'Open'
- The file will be added to the list
- Click “OK” to apply your settings
Add application from running processes
- Click the 'Add' button at the bottom of the list then select 'Running Applications'
- A list of processes currently running on your computer will be displayed
- Select the process whose parent application you wish to add for analysis
- Click 'OK' to confirm your choice
- The application will be added to the list
- Use the slider beside an application to enable or disable analysis.
- Click the 'Edit' button to update the details of an application.
- To remove an application, select it from the list, click the handle at the bottom then 'Remove'
- Click the handle at the bottom then 'Reset to Default' to revert the list to the default, predefined, applications.
- Click
'OK' at the bottom to apply your changes.
- Enable embedded code detection – If enabled, CCS will also scan for embedded codes (scripts) to provide 'Fileless Malware' protection.
The total size of saved scripts can be limited. Enter the total size to be saved in the 'Limit the total size of saved detected scripts to' field. When the limit is reached, the older records will be deleted to free up space.
- Detect shellcode injections (i.e. Buffer overflow protection) - Enabling this setting turns-on the Buffer over flow protection.
Background: A buffer overflow is an anomalous condition where a process/executable attempts to store data beyond the boundaries of a fixed-length buffer. The result is that the extra data overwrites adjacent memory locations. The overwritten data may include other buffers, variables and program flow data and may cause a process to crash or produce incorrect results. They can be triggered by inputs specifically designed to execute malicious code or to make the program operate in an unintended way. As such, buffer overflows cause many software vulnerabilities and form the basis of many exploits.
Turning-on buffer overflow protection instructs the Comodo Client Security to raise pop-up alerts in every event of a possible buffer overflow attack. You can allow or deny the requested activity raised by the process under execution depending on the reliability of the software and its vendor.
Comodo recommends that this setting to be maintained selected always. (Default = Enabled)
To exclude some of the file types from being monitored under Detect Shellcode injections
-
Select the 'Detect shellcode injections' checkbox and click the Exclusions link. The 'Manage Exclusions' dialog will appear.
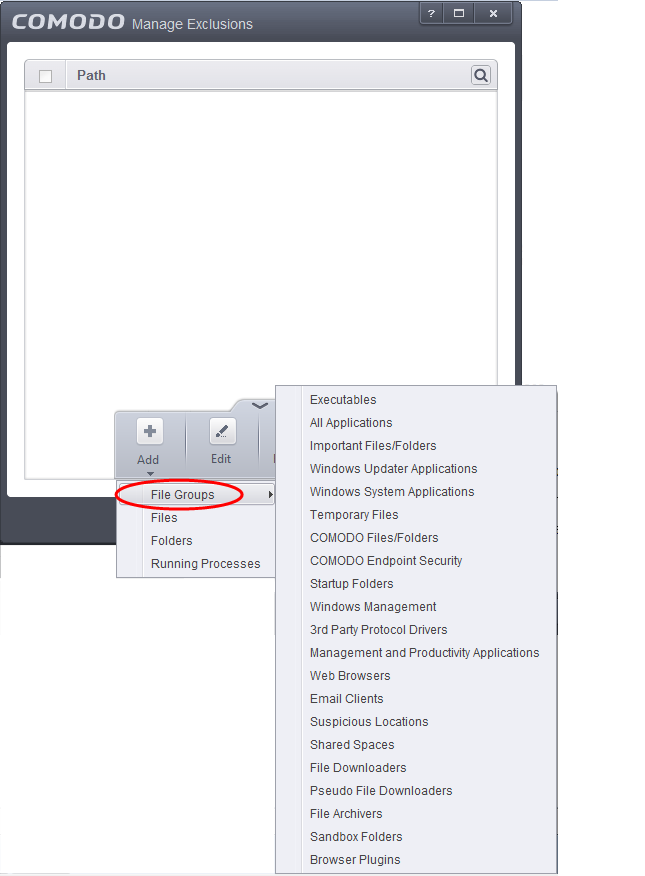
- Click the handle from the bottom of the interface and choose 'Add'
- You can add items by selecting the required option from the drop-down:
- File Groups - Enables you to select a category of pre-set files or folders. For example, selecting 'Executables' would enable you to create a ruleset for all files with the extensions .exe .dll .sys .ocx .bat .pif .scr .cpl . Other such categories available include 'Windows System Applications' , 'Windows Updater Applications' , 'Start Up Folders' etc. For more details on file groups, refer to the section File Groups.
- Running Processes - As the name suggests, this option allows you to select an application or executable from the processes that are currently running on your PC.
- Folders - Opens the 'Browse for Folders' window and enables you to navigate to the folder you wish to add.
- Files - Opens the 'Open' window and enables you to navigate to the application or file you wish to add.
|
Note: These settings are recommended for advanced users only. |
- Click 'OK' to implement your settings.



