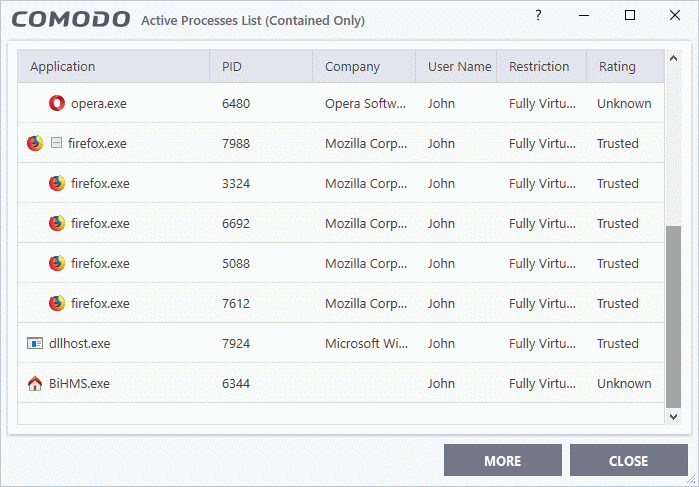
View Active Process List
Click 'Tasks' > 'Advanced Tasks' > 'View Active Processes'
- The active process list shows all processes started by applications currently running on your system.
- CCS can identify the parent application of a process to detect when a non-trusted application is trying to spawn a trusted application. CCS can then deny access rights to the trusted application.
- This deep level of inspection protects you against malware that tries to use trusted software to launch an attack.
- The interface also lets you run an online lookup on the parent application. Here, you can check its trust rating on the latest cloud databases. You can also submit an application to Comodo for analysis.
View the active process list
- Click 'Tasks' > 'Advanced Tasks'
- Click
the 'View Active Processes' tile:
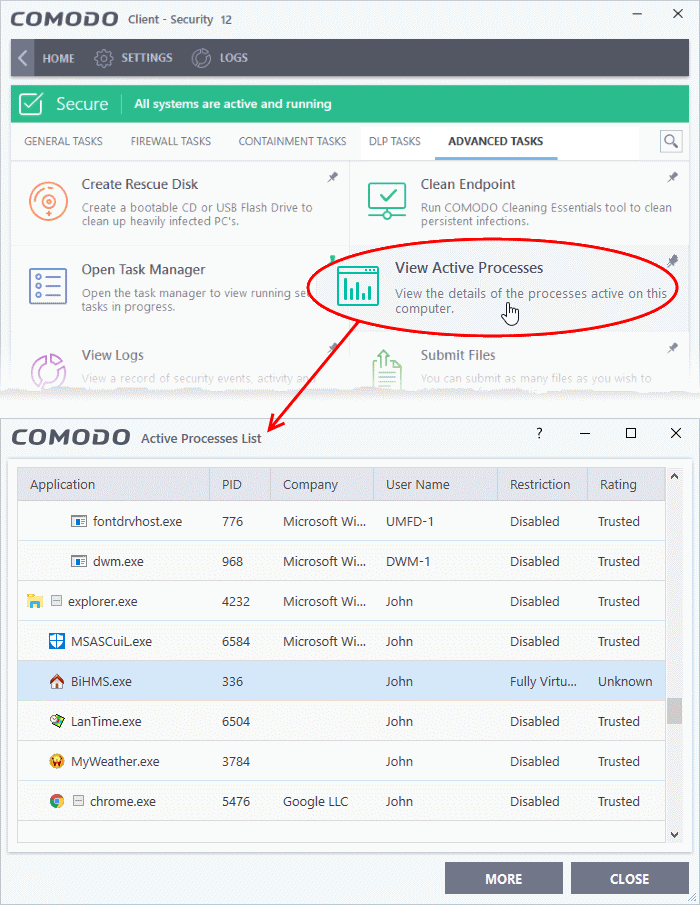
- Application - The name of the parent executable of the process.
- PID - The unique process identifier.
- Company - The vendor who created the software
- User Name - The user account under which the program is run
- Restriction - The security limitations placed on the program by the CCS containment module.
- Rating- The trust level of the program as per the local file list ('Settings' > 'File Rating' > File List')
- Right-click on any process to open the context sensitive menu:
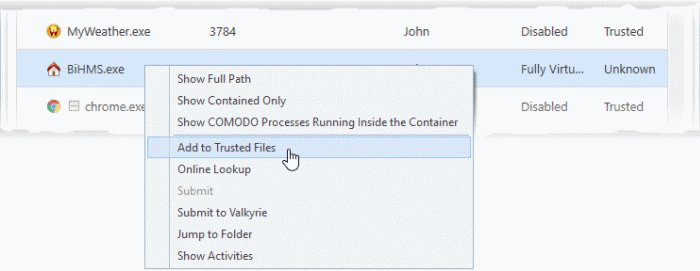
- Show Full Path – View the install location of the parent program
- Show Contained Only – Hides all processes except those running in the container.
- Show COMODO Processes Running Inside the Container – Hide all processes except Comodo processes running in the container.
- Add to Trusted Files – Assign 'Trusted' status to the executable that started the process. This allows the file to run as normal in future. You can view trusted files in the CCS 'File List' ('Settings' > 'File Rating' > 'File List').
- Online Lookup – Search for the executable in Comodo's global blacklist and whitelist. The results will tell you if the file is clean, malicious or unknown.
- Submit to Valkyrie - Uploads the parent executable to Comodo Valkyrie for analysis. Valkyrie is Comodo’s file testing and verdicting system that analyzes the submitted files with a range of static and dynamic tests to determine the file’s trust rating. The files are added to the Comodo safe list (white-listed) or to the database of virus signatures (blacklisted) depending on the results.
- Jump to Folder - Opens the folder containing the executable.
- Show Activities - Shows all actions by processes of the application. This option is available only for contained applications and if VirusScope is enabled ('Settings' > 'Advanced Protection > 'VirusScope').
-
Click the 'More' button to open Comodo KillSwitch - an advanced system monitor that lets you quickly identify and terminate any unsafe processes on your system.
If KillSwitch is not yet installed, clicking this button will prompt you to download the application. See Identify and Kill Unsafe Running Processes for more details.
View 'Active Processes' list of contained applications
Click the shortcut on the widget to view processes by applications inside the container. These applications include:
- Auto-Containment - Applications that are made to run in the container by a containment rule. See 'Auto-Containment Rules' for more details on defining auto-containment rules.
- Run Virtual - Applications that were manually run in containment. See 'Run an Application in Containment' for more details.
- Applications that are run inside the containment using the context sensitive menu - Click here for more details.
- Running browsers inside the containment from widget - Click here for more details.
- Programs that are added manually - See 'Auto-Containment Rules' for more details.
View active process from contained applications
- Click the first box in the second row in the CCS Widget.

The Active Processes List (Contained Only) screen appears: