Log Settings
- Click 'Settings' > 'General Settings' > 'Logging'.
- Comodo Client Security keeps detailed records of all antivirus, firewall, HIPS, containment, device control, VirusScope and autorun events.
- Logs are also created for 'Alerts Displayed', 'Tasks Launched', 'File List' changes, 'Vendor list changes' and 'CCS Configuration Changes'.
- Log settings let you specify the storage location, the maximum size of log files, and how CCS should react if the maximum file size is exceeded.
|
Note: You can view logs themselves at 'Tasks' > 'Advanced Tasks' > 'View Logs'. |
Configure Log settings
- Click 'Settings' on the CCS home screen
- Click
'General Settings' > 'Logging':
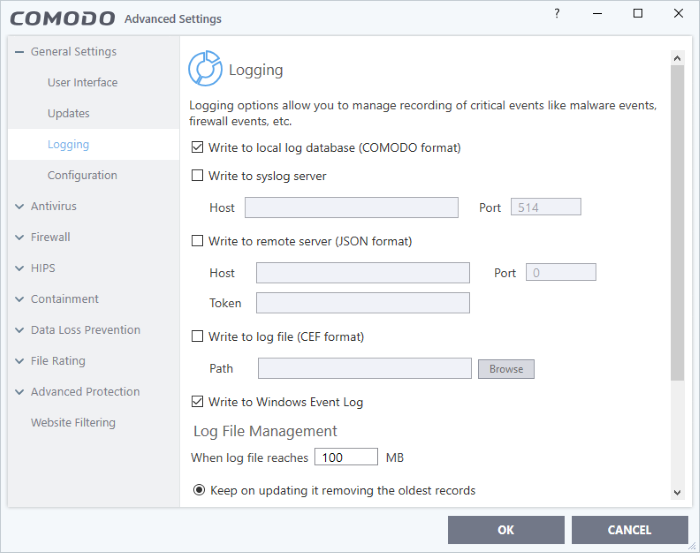
Logging
- Write to local log database (COMODO format) - Enable or disable logs in Comodo format.(Default = Enabled)
- Write
to Syslog Server (CEF Format) - CCS
forwards the logs to an external Syslog server integrated with
Endpoint Manager (EM). Enter the IP/hostname and port of the Syslog
server in fields provided. (Default
= Disabled)
- Write to remote server (JSON format) - CCS forwards the logs over https to a server integrated with Endpoint Manager. (Default = Disabled)
- Host - Enter the IP address or the host name of the server
- Port - The port through which the server listens to the CCS logs
Token - Enter the client authentication token so CCS can connect and forward logs to the server. The token is generated when you configure the HTTP Event Collector (HEC) on the server.
- See https://docs.splunk.com/Documentation/Splunk/7.2.6/Data/UsetheHTTPEventCollector if you need help to setup the event collector and generate a token.
- Enter the IP/hostname and port of the server in fields provided. Enter the security token to access the remote server in the field provided.
- Write to Log file (CEF) Format - CCS stores the logs at a specific local or network location. Click 'Browse' to select the storage location. (Default = Disabled)
- Write to Windows Event Logs - CCS logs are appended to 'Windows Event' logs. (Default = Enabled)
- Type 'Event Viewer' in Windows search to view Windows logs
- Specify what should happen when the log file reaches a certain size. You can choose keep the older logs or discard them.
- When log file reaches - Enter the maximum size of a log file in MB. (Default = 100MB)
- Keep on updating it removing the oldest records– When a log file reaches the max. size, CCS will delete the earliest log entries to make room for the new entries. (Default = Enabled)
- Move it to the specified folder – When a log file reaches the max. size, CCS starts a new log file and moves the old one to a folder of your choice. (Default = Disabled)
- Select the option and click 'the specified folder' to choose the storage folder:
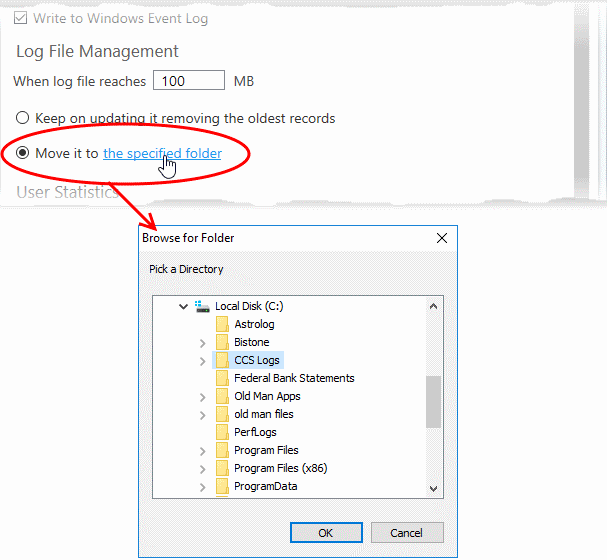
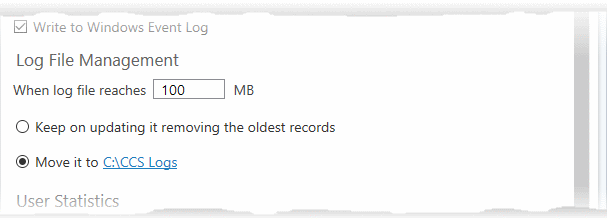
The selected folder path will appear beside 'Move it to'.
User Statistics
- Send anonymous program usage statistics to Comodo - Comodo collects usage details so we can analyze how our users interact with CCS. This real-world data allows us to create product improvements which reflect the needs of our users. If you enable this option, CCS will periodically send usage data to Comodo servers through a secure, encrypted channel. Your privacy is not affected because the data is anonymized. Disable this option if you don't want to send usage details to Comodo. (Default = Enabled)
- Click 'OK' for your changes to take effect.



