General Firewall Settings
- Click 'Settings' > 'Firewall' > 'Firewall Settings'
- Firewall settings let you quickly configure the overall behavior of the firewall. Settings are divided into three main areas:
Configure the firewall settings
- Click 'Settings' at the top of the CCS home screen
- Click 'Firewall' > 'Firewall Settings'
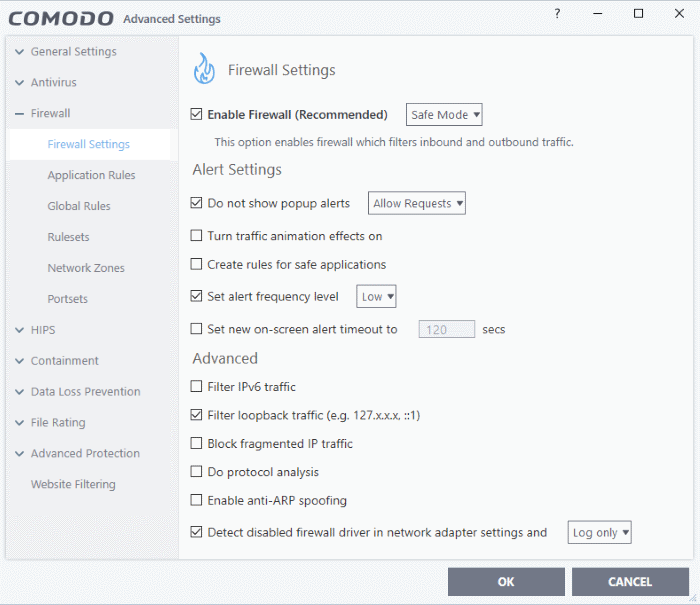
- Enable Firewall - Activate or deactivate firewall protection. (Default and recommended=Enabled)
- If enabled, you can also choose the security level from the drop-down menu:
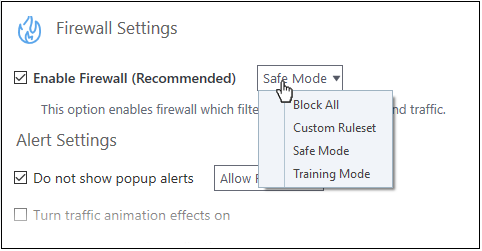
The choices available are:
- Block All: The firewall stops all traffic in and out of your computer, regardless of any other settings or rules. The firewall does not attempt to learn the behavior of any application, and does not create traffic rules for any applications. This option prevents your computer from accessing any networks, including the internet.
- Custom Ruleset Mode: The firewall applies ONLY network traffic rules that you have created. New users may want to think of this as the 'Do Not Learn' setting because the firewall does not attempt to learn the behavior of any applications. Nor does it automatically create network traffic rules for those applications. You will receive alerts every time there is a connection attempt by an application - even for applications on the Comodo Safe list (unless, of course, you have specified rules and policies that instruct the firewall to trust the application's connection attempt).
If any application tries to make a outbound connection, the firewall audits all the loaded components and checks each against the list of components already allowed or blocked. If a component is found to be blocked, the entire application is denied Internet access and an alert is generated. This setting is advised for experienced firewall users that wish to maximize the visibility and control over traffic in and out of their computer.
- Safe Mode (Default): If Create rules for safe applications is enabled then the firewall automatically creates rules to allow traffic by applications certified as 'Safe' by Comodo. For new, unknown applications, you will receive an alert whenever that application attempts to access the network. Should you choose, you can grant that application internet access by choosing 'Treat this application as a Trusted Application' at the alert. This deploys the predefined firewall ruleset 'Trusted Application' onto the application.
'Safe Mode' is the recommended setting for most users - combining the highest levels of security with an easy-to-manage number of connection alerts.
- Training
Mode: The
firewall monitors network traffic and creates automatic allow rules
for all new applications until the security level is adjusted. You
will not receive any alerts in 'Training Mode' mode. If you choose
the 'Training Mode' setting, we advise that you are 100% sure that
all applications installed on your computer are assigned the correct
network access rights.
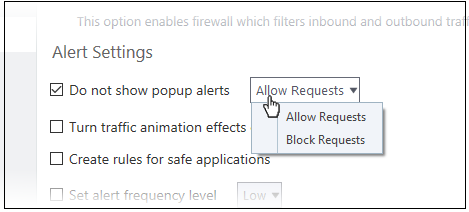
- Do not show popup alerts - Configure whether or not you want to be notified when the firewall encounters a request for network access. Choosing 'Do not show pop-up alerts' will minimize disturbances but at some loss of user awareness. (Default = Enabled)
If you choose this option then you have a choice of default responses that CCS should take - either 'Block Requests' or 'Allow Requests'.
- Turn traffic animation effects on - By default, the Comodo Client Security's 'Shield' tray icon displays a small animation whenever traffic moves to or from your computer.
![]()
If the traffic is outbound, you can see green arrows moving upwards on the right hand side of the shield. Similarly, for inbound traffic you can see yellow arrows moving down the left hand side. This provides a very useful indicator of the real-time movement of data in and out of your computer.
- Clear this check box If you would rather not see this animation. (Default = Disabled)
- The application is on the Comodo safe list, a global white-list of trusted software.
- The application has a 'Trusted' rating in the local file list File List if you need more details.
- The file is published and signed by a trusted vendor. The 'vendor' is the software company that created the file. See Vendor List if you need more details.
By default, CCS does not automatically create 'allow' rules for safe applications. This helps to lower resource usage and simplifies the rules interface. It also reduces the number of pop-up alerts and is beneficial to beginners who find difficulties in setting up the rules.
Enabling this checkbox instructs CCS to begin learning the behavior of safe applications so that it can automatically generate 'Allow' rules. These rules are listed in the Application Rules interface. The Advanced users can edit/modify the rules as they wish. (Default = Disabled)
- Set alert frequency level - Configure the amount of alerts that the firewall generates. Please note that this does not affect your security level, which is determined by the actual rules you have in place (for example, in 'Application Rules' and 'Global Rules'. For the majority of users, the default setting of 'Low' is the perfect level - ensuring you are kept informed of suspicious behavior while not getting overwhelmed with alerts. (Default=Disabled)
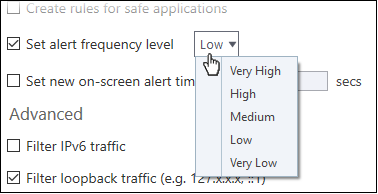
The options available are:
- Very High: The firewall shows separate alerts for outgoing and incoming connection requests for both TCP and UDP protocols on specific ports and for specific IP addresses, for an application. This setting provides the highest degree of visibility to inbound and outbound connection attempts but leads to a proliferation of firewall alerts. For example, using a browser to connect to your Internet home-page may generate as many as 5 separate alerts for an outgoing TCP connection alone.
- High: The firewall shows separate alerts for outgoing and incoming connection requests for both TCP and UDP protocols on specific ports for an application.
- Medium: The firewall shows alerts for outgoing and incoming connection requests for both TCP and UDP protocols for an application.
- Low: The firewall shows alerts for outgoing and incoming connection requests for an application. This is the setting recommended by Comodo and is suitable for the majority of users.
- Very Low: The firewall shows only one alert for an application.
The alert frequency settings refer only to connection attempts by applications or from IP addresses that you do not trust. For example, you could specify a very high alert frequency level, but not receive any alerts at all if you have chosen to trust the application that is making the connection attempt.
- Set new on-screen alert time out to: How long a firewall alert remains on-screen if it is not answered. The default timeout is 120 seconds. You may adjust this setting to your own preference.
Advanced detection settings help protect your computer against common types of denial of service (DoS) attack. When launching a denial of service or 'flood' attack, an attacker bombards a target machine with so many connection requests that your computer is unable to accept legitimate connections, effectively shutting down your web, email, FTP or VPN server.
- Filter IP v6 traffic - If enabled, the firewall will filter IPv6 network traffic in addition to IPv4 traffic. (Default = Disabled)
|
Background
Note: IPv6 stands for Internet Protocol Version 6 and
is intended to replace Internet Protocol Version 4 (IPv4). The
move is primarily driven by the anticipated exhaustion of
available IP addresses. IPv4 was developed in 1981 and is still
the most widely deployed version - accounting for almost all of
today's internet traffic. However, because IPv4 uses 32 bits for
IP addresses, there is a physical upper limit of around 4.3
billion possible IP addresses - a figure widely viewed as
inadequate to cope with the further expansion of the internet. In
simple terms, the number of devices requiring IP addresses is in
danger of exceeding the number of IP addresses that are available.
This hard limit has already led to the development of
'work-around' solutions such as Network Address Translation (NAT),
which enable multiple hosts on private networks to access the
Internet using a single IP address. IPv6 on the other hand, uses 128 bits per address (delivering 3.4×1038 unique addresses) and is viewed as the only realistic, long term solution to IP address exhaustion. IPv6 also implements numerous enhancements that are not present in IPv4 - including greater security, improved support for mobile devices and more efficient routing of data packets. |
- Filter loopback traffic: Loopback connections refer to the internal communications within your PC. Any data transmitted by your computer through a loopback connection is immediately received by it. This involves no connection outside your computer to the internet or a local network. The IP address of the loopback network is 127.0.0.1, which you might have heard referred to by its domain name of 'http://localhost'. This is the address of your computer. Loopback channel attacks can be used to flood your computer with TCP and/or UDP requests which can smash your IP stack or crash your computer. Leaving this option enabled means the firewall will filter traffic sent through this channel. (Default = Enabled).
- Block
fragmented IP traffic - When a connection is opened between two computers, they must agree on a Maximum Transmission Unit (MTU). IP datagram fragmentation occurs when data passes through a router with an MTU less than the MTU you are using. When a datagram is larger than the MTU of the network over which it must be sent, it is divided into smaller 'fragments' which are each sent separately. Fragmented IP packets can create threats similar to a DOS attack. Moreover, fragmentation can double the amount of time it takes to send a single packet and slow down your download time. (Default = Disabled)
- Do Protocol Analysis - Protocol Analysis is key to the detection of fake packets used in denial of service attacks. Enabling this option means Comodo Firewall checks that every packet conforms to that protocols standards. If not, then the packets are blocked. (Default = Disabled)
- Enable
anti-ARP spoofing - A
gratuitous Address Resolution Protocol (ARP) frame is an ARP Reply
that is broadcast to all machines in a network and is not in
response to any ARP Request. When an ARP Reply is broadcast, all
hosts are required to update their local ARP caches, whether or not
the ARP Reply was in response to an ARP Request they had issued.
Gratuitous ARP frames are important as they update your machine's
ARP cache whenever there is a change to another machine on the
network (for example, if a network card is replaced in a machine on
the network, then a gratuitous ARP frame informs your machine of
this change and requests to update your ARP cache so that data can
be correctly routed). However, while ARP calls might be
relevant to an ever shifting office network comprising many machines
that need to keep each other updated , it is of far less relevance
to, say, a single computer in your home network. Enabling
this setting helps to block such requests - protecting the ARP cache
from potentially malicious updates. (Default
= Disabled)
- Detect disabled firewall driver in network adapter settings – The firewall will take action if it discovers its driver is not enabled.
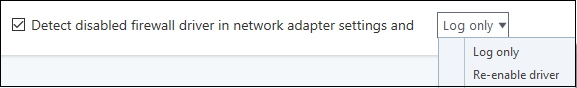
You can choose the following actions if this condition is met:
- Log only - Creates an event log but does not notify the administrator.
- Re-enable Driver - Attempts to turns the driver back on automatically.



