HIPS Configuration
- Click 'Settings' > 'HIPS'
- The host intrusion protection system (HIPS) constantly monitors system activity and stops processes from modifying important files and interfaces.
- Comodo Client Security ships with a default HIPS ruleset that works 'out of the box' - providing extremely high levels of protection.
- For example, HIPS automatically protects system-critical files, folders and registry keys to prevent unauthorized modifications by malicious programs.
- Advanced users looking to take a firmer grip on their security posture can quickly create custom policies and rulesets using the powerful rules interface.
Configure HIPS settings
- Click
'Settings' on the CCS home screen
- Click 'HIPS' on the left:
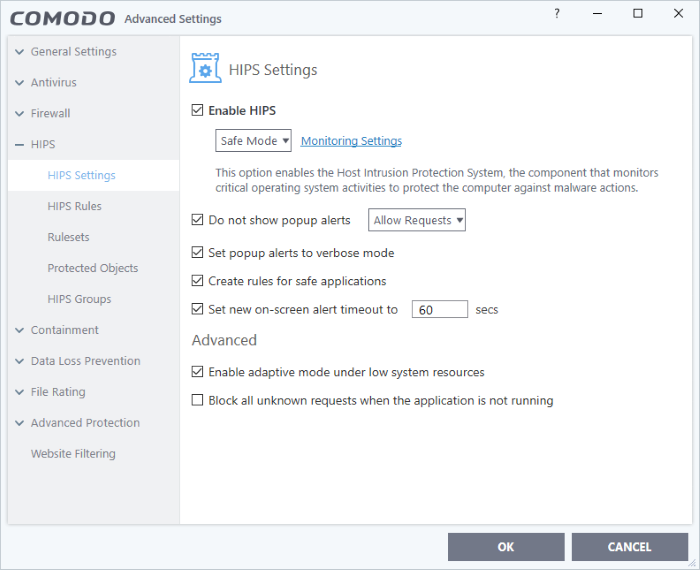
- HIPS Settings - General settings that govern the overall behavior of the HIPS component.
- HIPS Rules - These rules determine what actions an application is allowed to perform, and what level of protection it enjoys from other processes.
- Rulesets – View predefined rulesets and create new rulesets that can be applied to your applications in your system.
-
Protected Objects - Define objects to be protected by HIPS such as specific folders, system critical registry keys and so on.
- HIPS Groups – View and edit predefined 'Registry Groups' and 'COM Groups', create new groups so as to add them to Protected Objects.
|
Note
for beginners:
|



