Protected Registry Keys
The 'Registry Keys' area lets you define system critical registry keys which should protected against modification. Irreversible damage can be caused to your system if important registry keys are corrupted or modified.
Open the 'Registry Keys' section
- Click 'Settings' on the CCS home screen
- Click 'HIPS' > 'Protected Objects' on the left.
- Click the 'Registry Keys' tab:
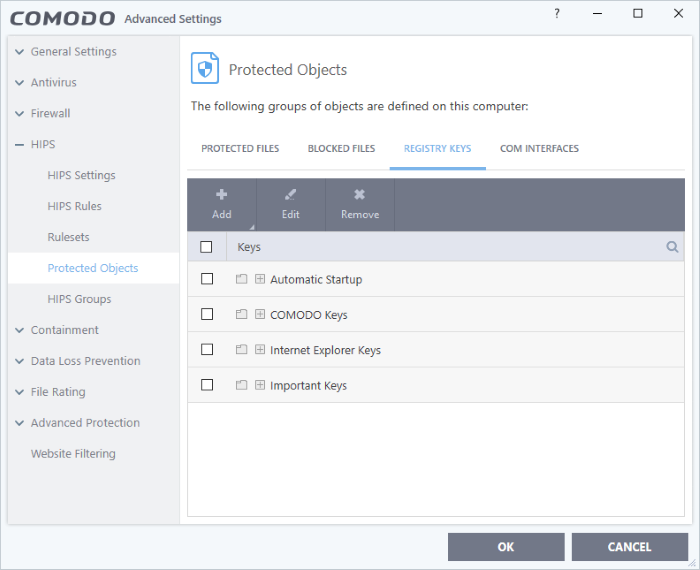
The buttons at the top provide the following options:
- Add - Select registry groups or individual keys that you want to protect
- Edit - Modify the path of the key or key group
- Remove - Delete the currently highlighted item
- Click the magnifying glass on the right to search for a specific item.
Manually add individual keys or registry groups
-
Click the 'Add' button
You can add keys individually or by registry group:
- Add Registry Groups - Adding a registry group allows you to batch select and import groups of important registry keys. Comodo Client Security provides the following, pre-defined groups - 'Automatic Startup' (keys), 'Comodo Keys', 'Internet Explorer Keys', 'Important Keys' and 'Temporary Keys'.
You can also create custom registry groups containing keys you wish to protect.
- To add a new group, click the 'Add' button > 'Registry Groups' and select the predefined group from the list and click 'OK'.
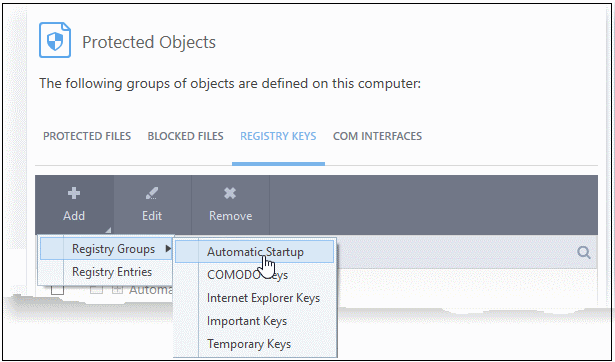
See Registry Groups in HIPS Groups section if you want to read more on this interface.
- Add
individual Registry Keys
- Click the 'Add' button and then select 'Registry Entries'
- Choose a key on the left then click the right arrow to add it to the protected list:
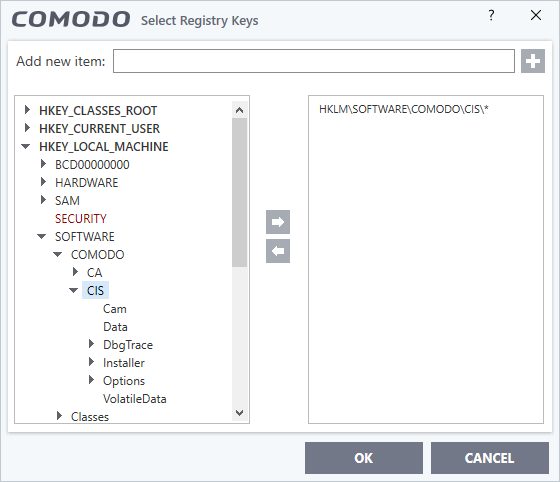
- Alternatively, you can type the key name in the field at the top then click '+'.
Edit an item in the Registry Protection list
- Select the key from the list and click the 'Edit' button. The 'Edit Property' dialog will appear.
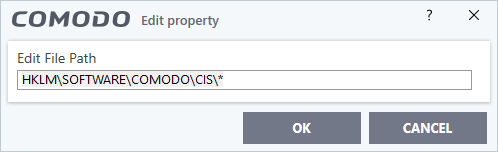
- Edit the key path, if you have relocated the key and click 'OK'.
|
Note: The 'Registry Groups' cannot be edited from this interface. You can edit only from Registry Groups in HIPS Groups section. |
To delete an item from Registry Protection list
-
Select the item from the list and click the 'Remove' button.
The
selected item will be deleted from the 'Registry Keys' protection
list. CCS will not generate alerts, if the key or the group is
modified by other programs.



