File Rating Settings
- A file rating determines how CCS interacts with a file:
- 'Trusted' files are safe to run.
- 'Untrusted' files are malware so they get quarantined or deleted.
- 'Unknown' files are run in the container until they get rated as trusted or untrusted.
- The rating of a file can change over time, especially in the case of 'unknown' files. For example, an unknown file might be re-classified as 'trusted' or 'untrusted' after it has been tested.
- You can also configure whether CCS should auto-upload unknown files to Comodo for analysis.
Open the 'File Rating Settings' interface
- Click 'Settings' on the CCS home screen
- Click
'File Rating' > 'File Rating Settings'
- Enable Cloud Lookup - CCS checks a file's trust rating on our cloud severs as part of the real-time scan process. (Default and recommended = Enabled)
- Analyze unknown files in the cloud by uploading them for instant analysis - CCS uploads files with an 'unknown' trust rating to Comodo for further analysis. Our experts will analyze the file, award it a trust rating, and add it to the global whitelist or blacklist as appropriate. (Default = Disabled)
- Upload metadata of unknown files to the cloud - Metadata is basic file information such as file source, author, date of creation and so on. If enabled, CCS will also send the file metadata when uploading unknown files to Comodo. (Default = Enabled)
- Do not show popup alerts - Whether or not CCS should show an alert when malware is detected by the cloud scanner (FLS). (Default = Enabled)
- Enabled - No alerts are shown. This minimizes disturbances but at some loss of user awareness.
CCS will automatically block and quarantine the threat.
- Disabled - A rating scanner alert is shown for malicious files.
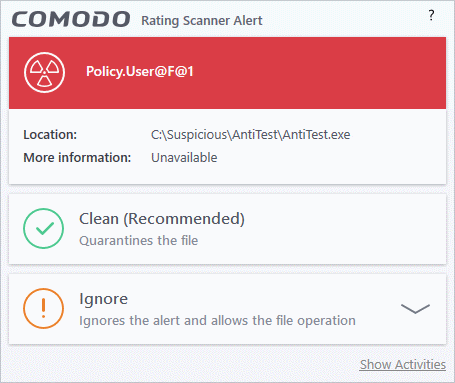
You can choose from these actions:
- Clean - The program is blocked and quarantined
- Ignore - Allows the file to run. Does not attempt to clean the file or move it to quarantine. Only click 'Ignore' if you are absolutely sure the file is safe. Clicking 'Ignore' will open three further options:
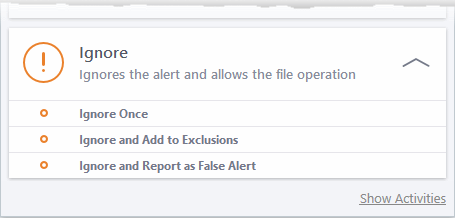
- Ignore Once - The file is allowed to run this time, but it will still be flagged as a threat by future scans.
- Ignore and Add to Exclusions - The file is allowed to run this time, and will not be flagged as a threat in future scans. The file is placed on the Exclusions list, meaning it is ignored permanently by the scanner.
- Ignore and Report as a False Alert - The file is allowed to run this time, and submitted to Comodo for analysis. Select this option if you think the file is safe, and that CCS was wrong to flag it as a threat. Comodo will re-examine the file.
- Terminate the entire process chain of malware detected by rating scan - When a malicious process is detected, the entire process tree can be terminated instead of the only termination of the Malicious process.
- Rate applications according to their vendor rating - CCS will give files the same rating as the trust rating of the publisher (software creator). For example - if the vendor is trusted, then all files created by the vendor will be trusted. (Default =Enabled)
- The vendor is the software company who created and digitally signed the file.
- You can view vendor trust ratings in 'Advanced Settings' > 'File Rating' > 'Vendor List'.
- CCS ships with a list of vendors with 'Trusted' status. You can add new vendors to the list and set your own vendor ratings as required.
- The vendor rating priority is shown below:
- Admin
- User
- Comodo
- Click the 'Vendor Rating' link to open the 'Vendor List' screen. See Vendor List for more details.
- Trust files installed by trusted installers - CCS awards trusted status to files whose parent applications are listed in the 'Installer or Updater' rule in HIPS Rules. (Default = Enabled)
- Detect potentially unwanted applications (PUA) - CCS scans will flag applications that:
(i) a user may or may not be aware is installed on their computer(ii) may contain functionality and objectives that are not clear to the user.
Example PUA's include adware and browser toolbars.
PUA's are often installed as an additional extra when the user is installing an unrelated piece of software. Unlike malware, many PUA's are legitimate pieces of software with their own EULA agreements. However, the true functionality of the software might not have been made clear to the end-user at the time of installation. For example, a browser toolbar that tells you the weather may also contain code that tracks your online activity(Default = Enabled).
- Automatically purge unrecognized files every NN hour(s) - CCS periodically checks that all unrecognized files in the list are still installed at the path specified. If not, the file is removed from the list. Select the interval in hours from the drop-down box. (Default = Enabled, 4 Hours)
- Use proxy when performing Cloud Lookup - CCS submits files to FLS for analysis through a proxy. The proxy server is same one that is defined for program and database updates.
- See 'Configure Program and Virus Database Updates' for more details. (Default = Disabled)
- Automatically scan unrecognized files at equal intervals - CCS can periodically re-scan unknown files to check whether a new trust rating is available for them. (Default = Enabled and set for every 4 hours).
- Click 'Edit Scan Options' to configure the scan settings and schedule.
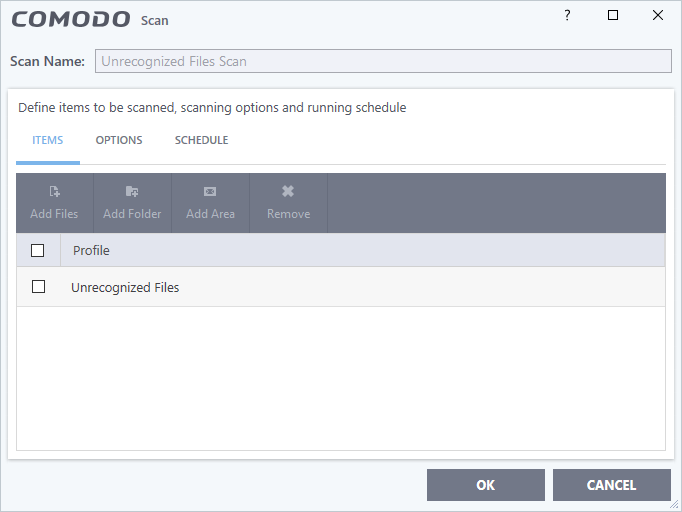
- Scan Name - The label of the scan. This is pre-configured and cannot be edited.
- Items - The files that are scanned by the profile. 'Unrecognized Files’ is the default. You cannot edit or add files to this profile.
- Scan Options - Configure scan technologies, how to handle threats, and more. See Configure scan options for the profile in Scan Profiles for help with this.
- Schedule - Specify the frequency of the automated scans. See Configure a scan schedule in Scan Profiles for help with this. (Default = Every 4 hours)
- Automatically re-evaluate quarantined files at equal intervals - CCS checks our master online database for the latest trust rating on currently quarantined files. (Default = Enabled and set for once every day)
- Click 'Edit Scan Options' to configure the scan schedule.
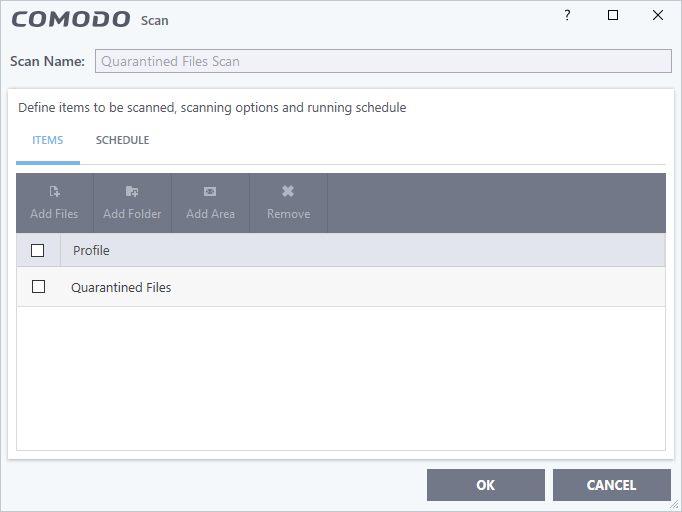
- Scan Name - The label of the scan. This cannot be edited
- Items - The files that are scanned by the profile. 'Quarantined Files’ is the default. You cannot edit or add files to this profile
- Schedule - Specify the frequency of the automated scans. See Configure a scan schedule in Scan Profiles for help with this. (Default = Once every day)
- Click 'OK' to save your changes
- Click
'OK' in the 'Advanced Settings' screen for your settings to take
effect.
- Automatically delete obsolete files at equal intervals - CCS will automatically delete some files which appears in quarantine. So file should be quarantined first, then new scan will check quarantined items and deleted files matching new list (files to delete).
- Click 'Edit Scan Options' to configure the scan schedule.
- Scan Name - The label of the scan. This cannot be edited
- Items - The files that are scanned by the profile. 'Quarantined Files’ is the default. You cannot edit or add files to this profile
- Obsolete Files - Files that identified and deleted that appear in quaratine.
- Select from Files
- Click 'Add' > Select 'Files'
- Selct the file you want to add
- Click 'Ok'
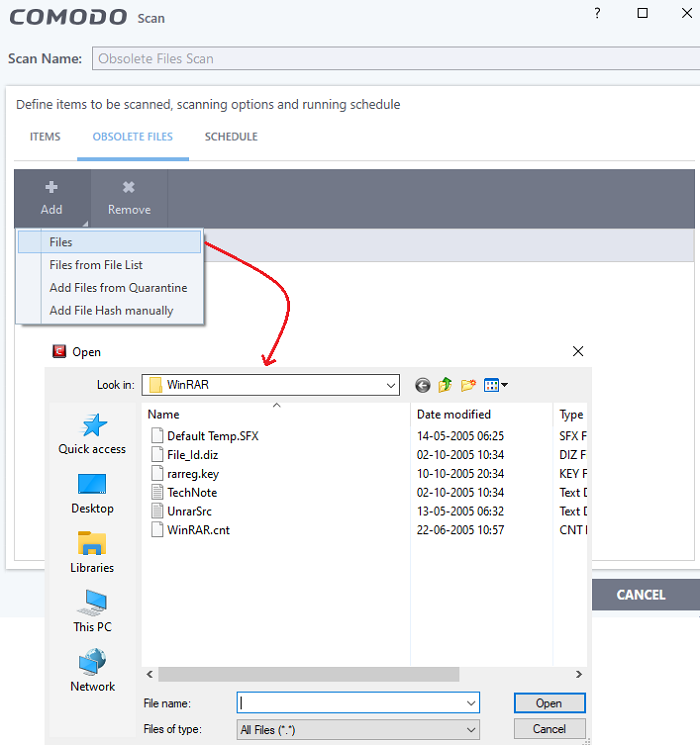
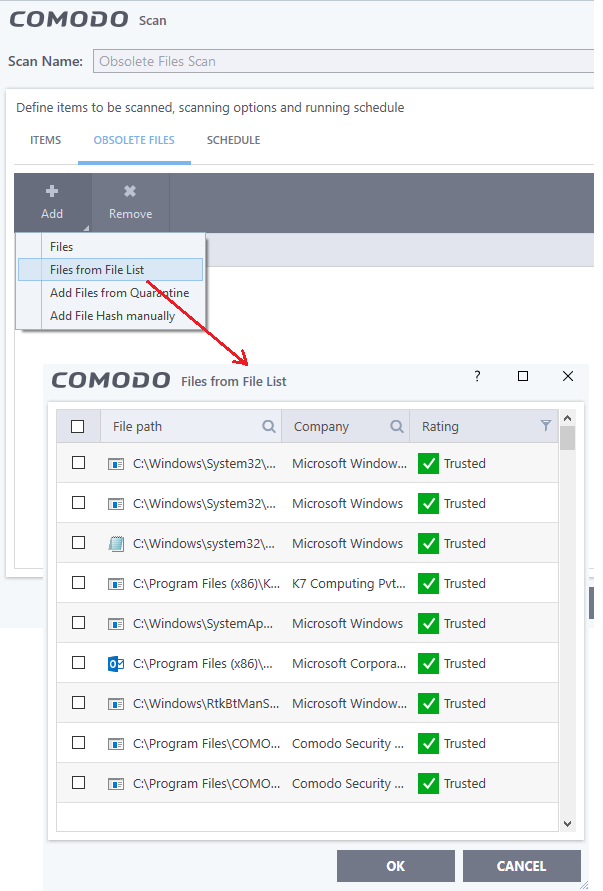
- Files from file list
- Click 'Add' > Select 'Files from File List.
- Select the files and click 'Ok'
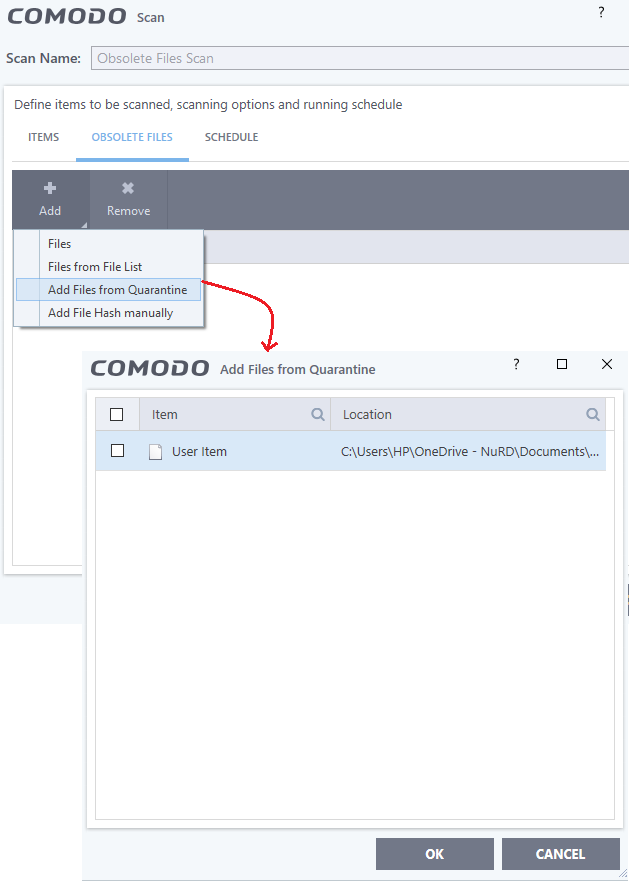
- Add files from Quarantine List
- Click 'Add' > Select 'Add Files from Quaratine'
- Select the quaratined files from the list and click 'Ok'
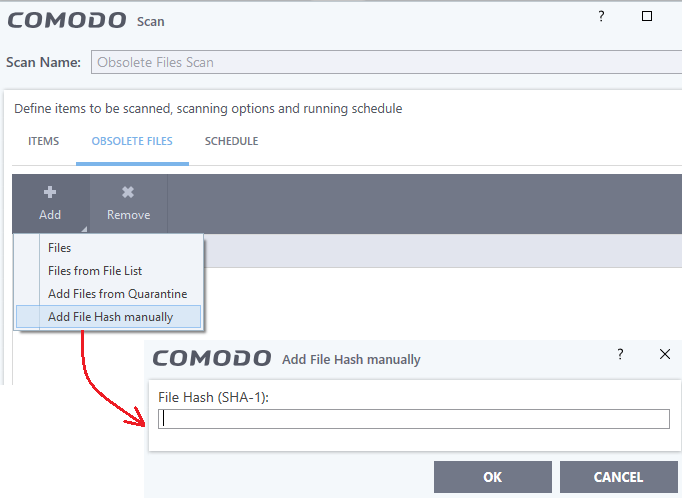
- Add file hash manually
- Click 'Add' > Select 'Add File hash manually'
- Enter the file hash value and click 'Ok'
- Schedule - Specify the frequency of the automated scans. See Configure a scan schedule in Scan Profiles for help with this. (Default = Once every day)
- Click 'OK' to save your changes
- Click 'OK' in the 'Advanced Settings' screen for your settings to take effect.



