Manage Quarantined Items
Click 'Tasks' > 'General Tasks' > 'View Quarantine'
- The quarantine area shows malicious files which CCS has isolated to prevent them from infecting your system.
- All files in quarantine are encrypted so they cannot run or cause harm.
- Items are usually quarantined by the antivirus scanner, but it is also possible to manually quarantine items. See 'General Tasks' > 'Scan and Clean Your Computer' if you want to learn about the AV scanner.
Open the 'Quarantine' interface
- Click 'Tasks' on the CCS home screen
- Click 'General Tasks' > 'View Quarantine'
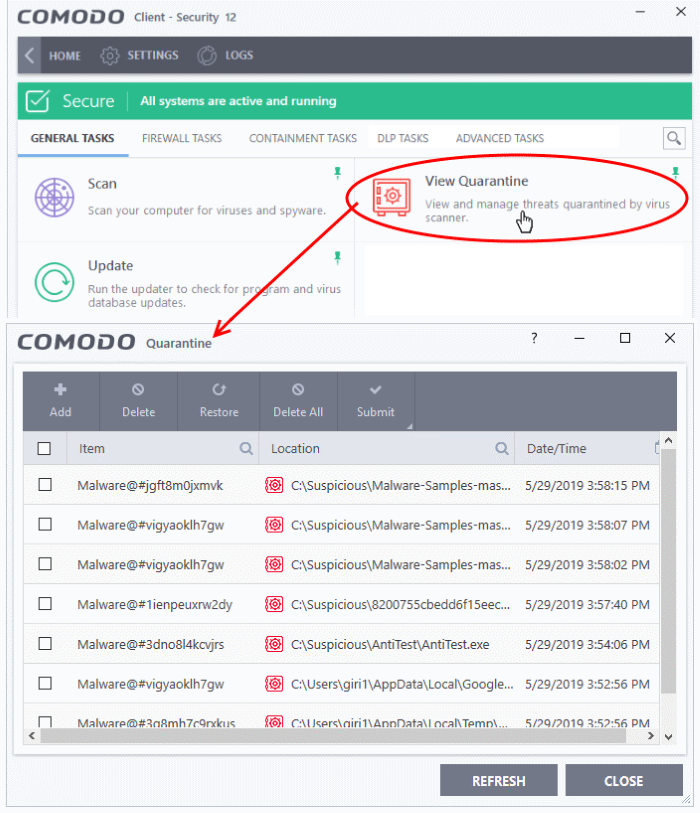
- Item - The name of the malicious component
- Location - The file path of the item
- Date/Time – When the item was moved to quarantine.
The interface lets you review quarantined files and take the following main actions:
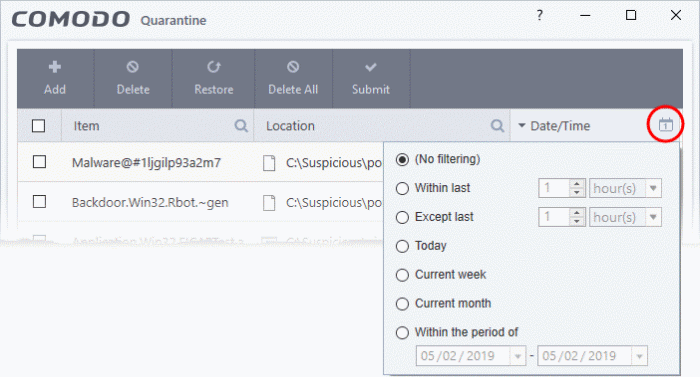
Search and filter options:
- Click
any column header to sort items in alphabetical order of that column
- Click the search icon in the 'Item' column to search for a file by name
- Click the search icon in the 'Location' column to search by file-path
- Click the icon in the 'Date/Time' column to filter results by time period
Manually add files to quarantine
Files or folders that you are suspicious of can be manually moved to quarantine:
- Click 'Tasks' on the CCS home screen
- Click 'General Tasks' > 'View Quarantine'
- Click the 'Add' button at the top
- Navigate to the file you want to add to the quarantine and click 'Open'.
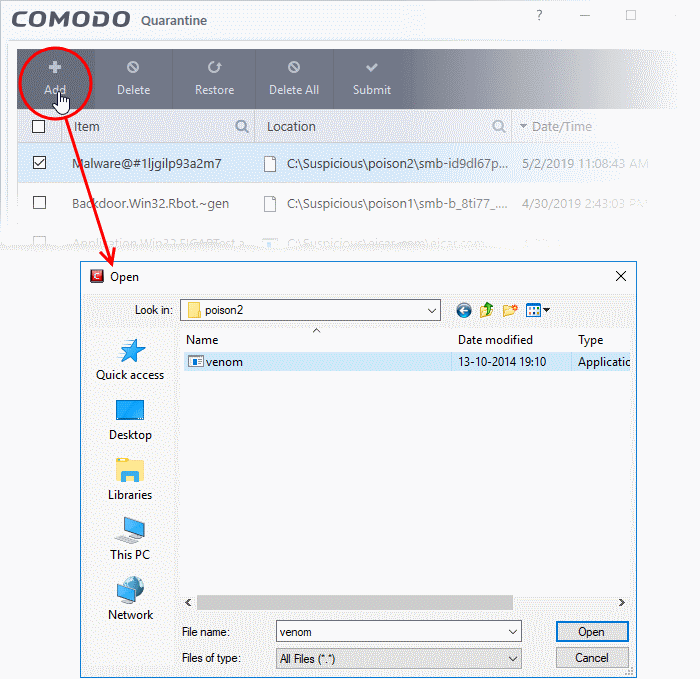
The file will be added to 'Quarantine'. You can even send the file for analysis to Comodo Valkyrie, for inclusion in the white list or black list, by clicking the 'Submit' button.
- Click 'Tasks' on the CCS home screen
- Click 'General Tasks' > 'View Quarantine'
- Select the items in the quarantine interface and click the 'Delete' button at the top
- Click the 'Delete All' button if you want to permanently remove all quarantined items
- The files will be deleted from your computer
- Click 'Tasks' on the CCS home screen
- Click 'General Tasks' > 'View Quarantine'
- Select the items to be moved back to their original locations and click the 'Restore' button at the top
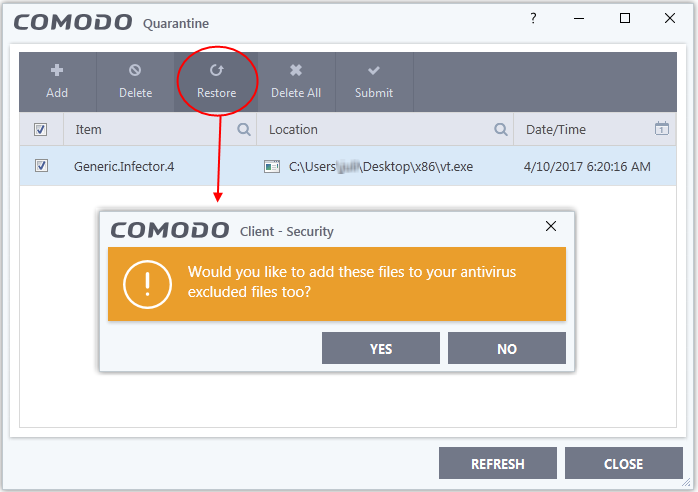
You will be asked if you want to add the item to the Scan Exclusions list:
- 'Yes' - The file will be restored to its original location. It will not be flagged as dangerous nor quarantined by future antivirus scans
- 'No' - The file will be
restored to its original location. If the file contains malware it
will be re-quarantined by the next antivirus scan
Submit selected quarantined items to Valkyrie for analysis
Valkyrie is Comodo’s file testing and verdicting system. After submitting your files, Valkyrie will analyze them with a range of static and dynamic tests to determine the file’s trust rating.
- Click 'Tasks' on the CCS home screen
- Click 'General Tasks' > 'View Quarantine'
- Select the items you want to submit. You can send several files at once
- Click 'Submit' > 'Submit to Valkyrie' in the top-menu. The files will be immediately sent to Valkyrie for analysis
|
Tip:
Alternatively, right click an item then choose 'Submit to
Valkyrie' from the menu. |
- All submitted files are analyzed at Valkyrie. If they are found to be trustworthy, they will be added to the Comodo safe list (white-listed). Conversely, if they are found to be malicious then they will be added to the database of virus signatures (blacklisted).



