Firewall Logs
- Click 'Logs' in the CCS menu bar
- Select 'Firewall Events' from the drop-down at upper-left
Firewall
events are created for various reasons. Reasons include when a
process attempts a connection that breaks a firewall
rule, or when there is a change in
firewall settings.
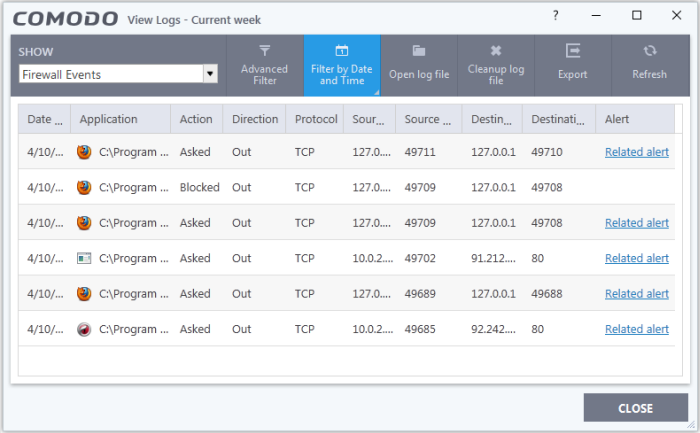
- Date & Time - When the event occurred.
- Application – The name of the program or process that caused the event.
- Action - How the firewall reacted to the connection attempt. For example, whether the attempt was allowed, blocked o r an alert displayed.
- Direction - Whether the connection attempt was inbound or outbound.
- Protocol – The connection method that the application attempted to use. This is usually TCP/IP, UDP or ICMP, which are the most heavily used networking protocols.
- Source IP – The address of the host from which the connection attempt was made. For outbound connections, this is usually the IP address of your computer. For inbound connections, it is usually the IP address of the external server.
- Source Port - The port number that the source host used to make the connection attempt.
- Destination IP - The address of the host to which the connection attempt was made. For inbound connections, this is usually the IP address of your computer.
-
Destination Port - The port number on the destination host which the source tried to connect to.
- Alert - Click 'Related Alert' to view the notification generated by the event.
|
Note: Firewall alerts are only shown if 'Do not show pop up alerts' is disabled in 'Settings' > 'Firewall' > 'Firewall Settings'. See General Firewall Settings for more details. |
- Export - Save the logs as a HTML file. You can also right-click inside the log viewer and choose 'Export'.
- Open log file - Browse to and view a saved log file.
- Cleanup log file - Delete the selected event log.
- Refresh - Reload the current list and show the latest logs.
Click any column header to sort the entries in ascending / descending order.



