Understand Security Alerts
Alerts Overview
- CCS alerts warn you about security related activities at the moment they occur.
- Each alert contains information about a particular issue so you can make an informed decision about whether to allow or block it.
- Alerts also let you specify how CCS should behave in future when it encounters activities of the same type.
- The following screenshot shows the basic layout of a CCS alert:
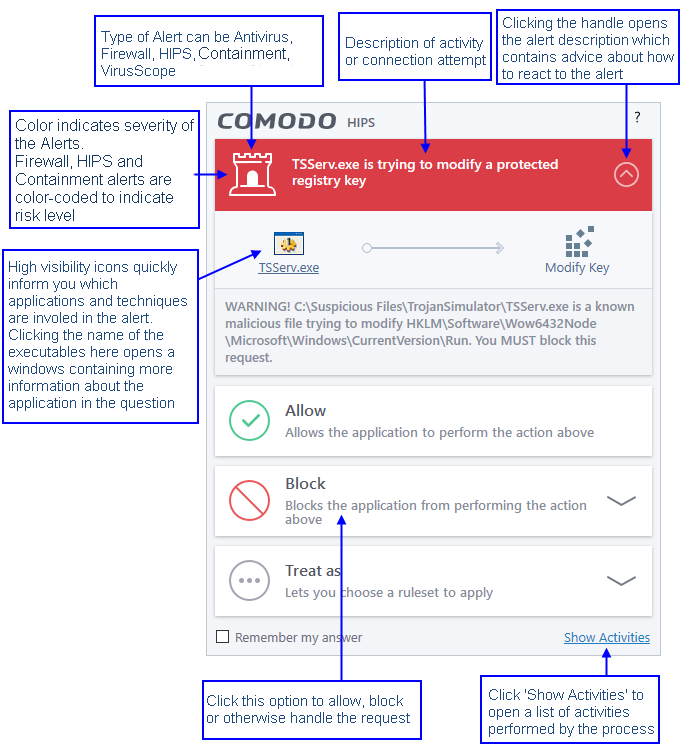
The type of alert you see depends on the security module which generated the alert. Click the links below to find out more about each alert type.
- Antivirus Alerts - Shown whenever virus or virus-like activity is detected. AV alerts are shown if the antivirus is enabled and 'Do not show antivirus alerts' is disabled in Real-time Scanner Settings.
-
Auto-Scan Alerts - Shown when you connect an external storage device to your computer. Auto-scan alerts are shown if antivirus is enabled and the option 'Do not show auto-scan alerts' is disabled in Real-time Scanner Settings.
-
Firewall Alerts - Shown whenever a process attempts unauthorized network activity. Firewall alerts will be displayed only if firewall is enabled and the option 'Do not show popup alerts' is disabled in Firewall Settings.
- HIPS Alerts - Shown when a process attempts an unauthorized action or tries to access protected areas. HIPS alerts are shown if HIPS is enabled and Do not show popup alerts is disabled.
- Containment Alerts (including Elevated
Privilege Alerts) - Shown when CCS automatically contains an file. This usually happens if the file has an 'unknown' trust-rating. If privilege elevation alerts are enabled in Containment
Settings you will also see this type of alert if a program requires admin privileges to run.
- VirusScope Alerts - Shown when a running process tries to perform a suspicious action. VirusScope alerts let you quarantine the process & reverse its changes, or let the process go ahead. Be especially wary if a VirusScope alert appears 'out-of-the-blue' when you have not made any recent changes to your computer. VirusScope alerts are generated if VirusScope is enabled in advanced settings.
- Device
Control Notifications - Shown when an external device that is blocked by the admin is connected to your system. These alerts are shown if 'Device Control' and 'Show notifications when devices...' are both enabled in Device
Control Settings.
Alerts may contain very important security warnings, or may simply occur because you are running a certain application for the first time. Your reaction should depend on the information in he alert.
|
Note: This section is concerned only with alerts and notifications generated by the antivirus, firewall, HIPS, VirusScope, auto-Containment and device control components of CCS. See Comodo Message Center notifications, Notification Messages and Information Messages for other types of alert. |
The color of the alert shows the risk level of the reported activity.
- Yellow - Low Severity - In most cases, you can safely approve these requests. The 'Remember my answer' option is automatically pre-selected for safe requests
- Orange - Medium Severity - Read the information in the alert description area before making a decision. These alerts could be the result of harmless activity by program you trust, but could also indicate malicious activity. If you know the application to be safe, then it is usually okay to allow the request. If you do not recognize the application or connection request then you should block it.
- Red - High Severity - Known malware discovered, or highly suspicious behavior by an application/process. Carefully read the information provided when deciding whether to allow it to proceed.
|
Note: Antivirus alerts are not ranked in this way. They always appear with a red bar. |
The description is a summary of the
nature of the alert and can be revealed by clicking the handle as
shown:
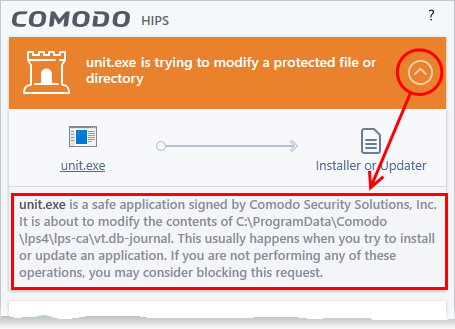
The description tells you the name of the software/executable that caused the alert; the action that it is attempting to perform and how that action could potentially affect your system. You can also find helpful advice about how you should respond.
Now that we have outlined the basic construction of an alert, let's look at how you should react to them.
Comodo Client Security generates
an Antivirus alert whenever a virus or virus-like activity is
detected on your computer. The alert contains the name of the virus
detected and the location of the file or application infected by it.
Within the alert, you are also presented with response-options such
as 'Clean' or 'Ignore'.
|
Note: Antivirus alerts will be displayed only if the option 'Do not show antivirus alerts' is disabled. If this setting is enabled, only antivirus notifications are shown. This option is found under 'Settings > Antivirus > Realtime Scan'. See Real-time Scan Settings for more details. |
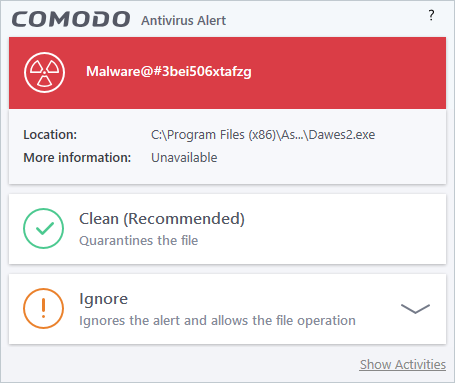
The following response-options are available:
- Clean - Disinfects the file if a disinfection routine exists. If no routine exists for the file then it will be moved to quarantine, an isolated storage in which the item is encrypted and stored. Files in the quarantine cannot be executed. If desired, you can submit the file/application to Comodo for analysis from the Quarantine interface. See Manage Quarantined Items for more details on quarantined files.
- Ignore - Allows the process to run and does not attempt to clean the file or move it to quarantine. Only click 'Ignore' if you are absolutely sure the file is safe. Clicking 'Ignore' will open three further options:
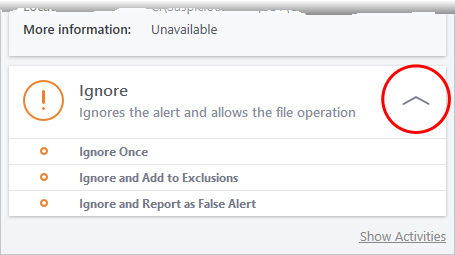
- Ignore Once -The file is allowed to run this time only. If the file attempts to execute on future occasions, another antivirus alert is displayed.
- Ignore and Add to Exclusions - The file is allowed to run and is moved to the Exclusions list - effectively making this the 'Ignore Permanently' choice. No alert is generated if the same application runs again.
- Ignore
and Report as a False Alert - If you are sure that the file is
safe, select 'Ignore and Report as a False Alert'. CCS will then
submit this file to Comodo for analysis. If the false-positive is
verified (and the file is trustworthy), it will be added to the
Comodo safe list.
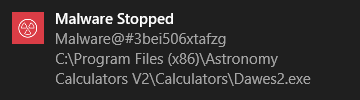
If you have chosen to not to show Antivirus Alerts through Settings > Realtime Scanner Settings by leaving the option 'Do not show antivirus alerts' enabled (default=enabled) and if CCS identifies a virus or other malware in real time, it will immediately block malware and provide you with instant on-screen notification:
Auto-scan alerts appear when you plug a removable device into your computer (USB stick, portable HDD, etc). The alert asks you whether you want to scan the device for viruses.
These alerts are only shown if 'Do not show auto-scan alerts' is disabled in 'Settings > Antivirus > Realtime Scan'. See Real-time Scan Settings if you want to read more.
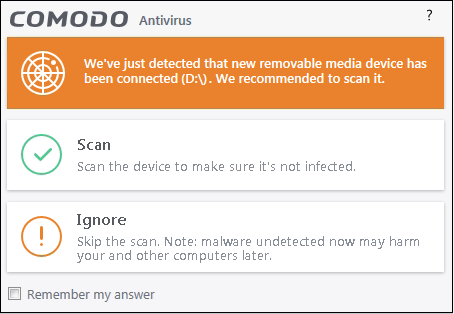
- Scan - CCS checks the device for viruses using the settings in the 'Manual Scan' profile. If this is not available then the scan uses the settings in the 'Full Scan' profile.
- Ignore - The device is not scanned.
- Remember my answer – CCS will automatically carry out your choice of scan or ignore when the device is connected in future. This only applies to the specific device. You will still see an alert if you connect a different device.
CCS generates a firewall alert when it detects unauthorized network connection attempts or when traffic runs contrary to one of your application or global rules. Each firewall alert allows you to set a default response that CCS should automatically implement if the same activity is detected in future. The followings steps will help you answer a Firewall alert:
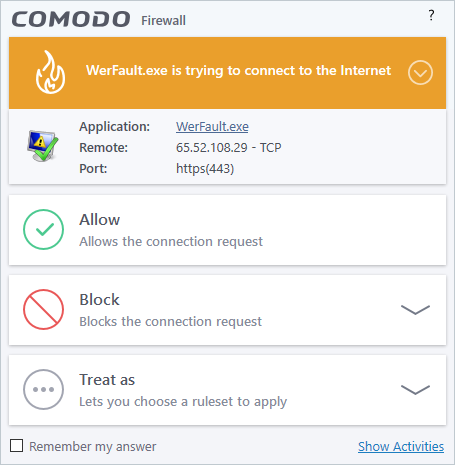
|
Tip: Click
'Show Activities' to view actions performed by the process in
question. This link is only shown if
VirusScope is enabled in Settings >
VirusScope. The 'Show Activities' link is grayed-out if the process had not started before the alert was generated. |
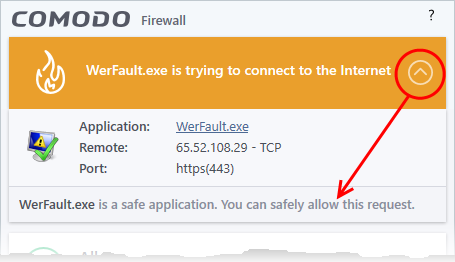
-
Carefully read the information displayed in clicking the down arrow in the alert description area. The Firewall can recognize thousands of safe applications. (For example, Internet Explorer and Outlook are safe applications). If the application is known to be safe - it is written directly in the security considerations section along with advice that it is safe to proceed. Similarly, if the application is unknown and cannot be recognized you are informed of this.
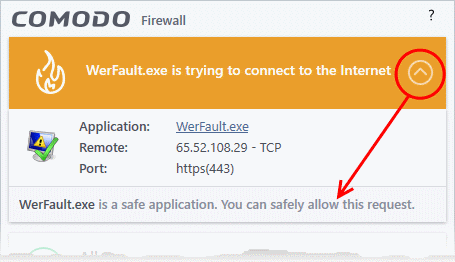
If it is one of your everyday applications and you want to allow it Internet access to then you should select Allow.
In all cases, clicking on the name of the application opens a properties window that can help you determine whether or not to proceed:
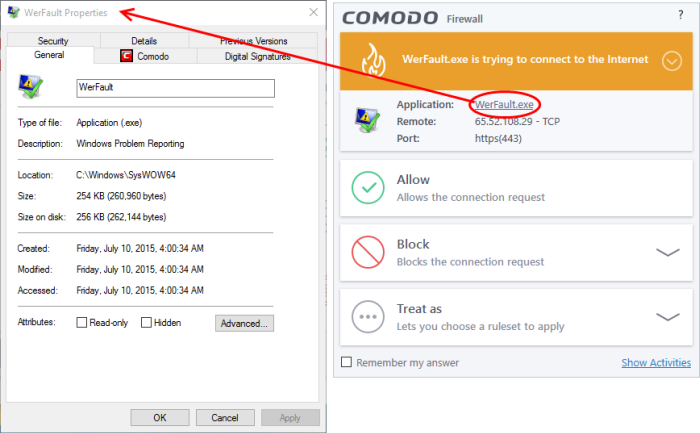
If you don't recognize the application then we recommend you Block the application. By clicking the handle to expand the alert, you can choose to 'Block' the connection (connection is not allowed to proceed), 'Block and Terminate' (connection is not allowed to proceed and the process/application that made the request is shut down) or 'Block, Terminate and Reverse' (connection is not allowed to proceed, the process/application that made the request is shut down and the changes made by the process/application to other files/processes in the system will be rolled back).
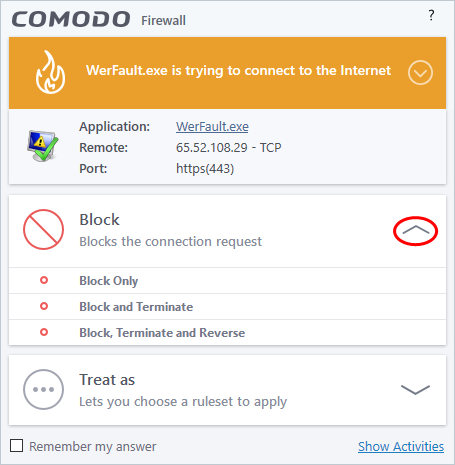
|
Note: Block, Terminate and Reverse':
|
-
If you are sure that it is one of your everyday application, try to use the 'Treat As' option as much as possible. This allows you to deploy a predefined firewall ruleset on the target application. For example, you may choose to apply the policy Web Browser to the known and trusted applications like 'Comodo Dragon', 'Firefox' and 'Google Chrome'. Each predefined ruleset has been specifically designed by Comodo to optimize the security level of a certain type of application.
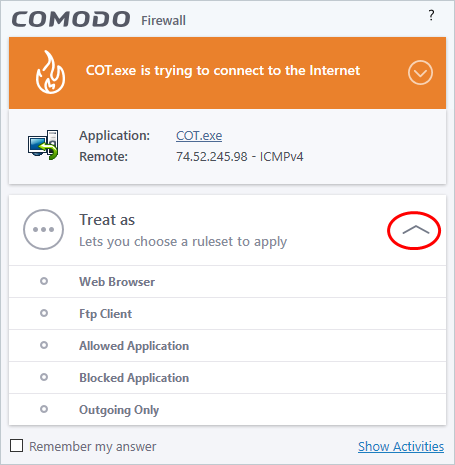
Remember to check the box 'Remember My Answer' for the ruleset to be applied in future.
-
If the Firewall alert reports a behavior, consistent with that of a malware in the security considerations section, then you should block the request AND select Remember My Answer to make the setting permanent.
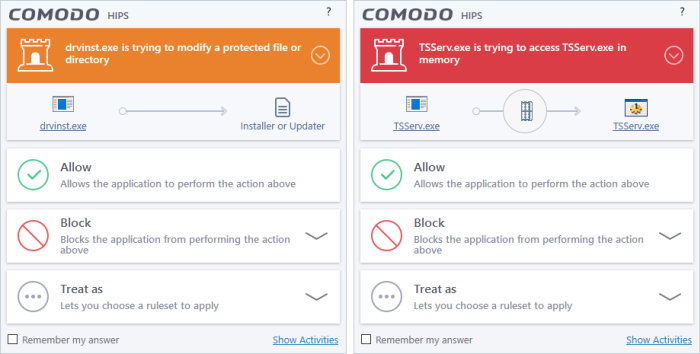
Comodo Client Security generates a HIPS alert based on the behavior of applications and processes running on your system. Please read the following advice before answering a HIPS alert:
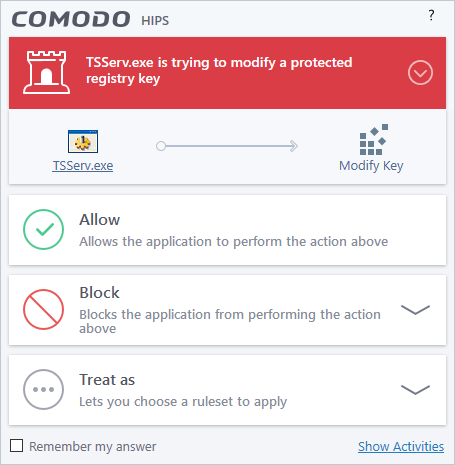
|
Tip: Click 'Show Activities' to view actions performed by the process in question. This link is only shown if
VirusScope is enabled in Settings >
VirusScope. The 'Show Activities' link is grayed-out if the process had not started before the alert was generated. |
-
Carefully read the information displayed after clicking the handle under the alert description. Comodo Client Security can recognize thousands of safe applications. If the application is known to be safe - it is written directly in the security considerations section along with advice that it is safe to proceed. Similarly, if the application is unknown and cannot be recognized, you are informed of this.
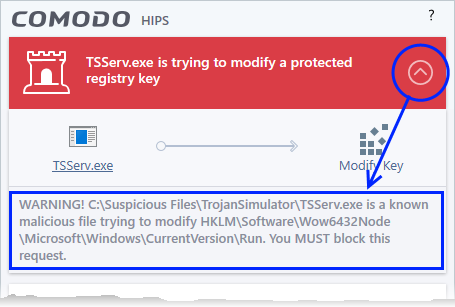
If it is one of your everyday applications and you simply want it to be allowed to continue then you should select Allow.
If you don't recognize the application then we recommend you select Block the application. By clicking the handle to expand the alert, you can choose to
- 'Block' - The application is not allowed to run
- 'Block and Terminate' - The application is not allowed to run and the processes generated by it are terminated thereby shutting down the application
- 'Block, Terminate and Reverse' - The application is not allowed to run, the processes generated by it are terminated and the changes made by the processes/application to other files/processes in the system will be rolled back.
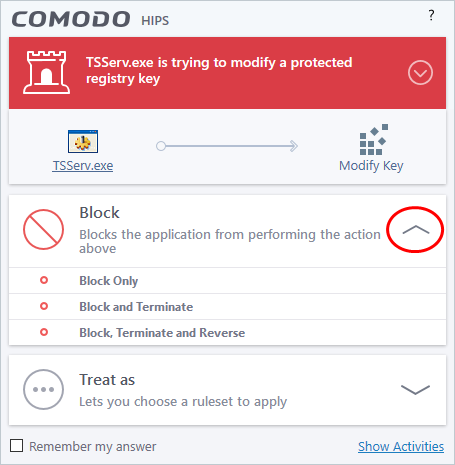
|
Note: 'Block, Terminate and Reverse' is only shown if VirusScope is enabled in Settings > VirusScope. |
-
If you are sure that it is one of your everyday applications and want to enforce a security policy (ruleset) to it, please use the 'Treat As' option. This applies a predefined HIPS ruleset to the target application and allows the application to run with access rights and protection settings as dictated by the chosen ruleset.
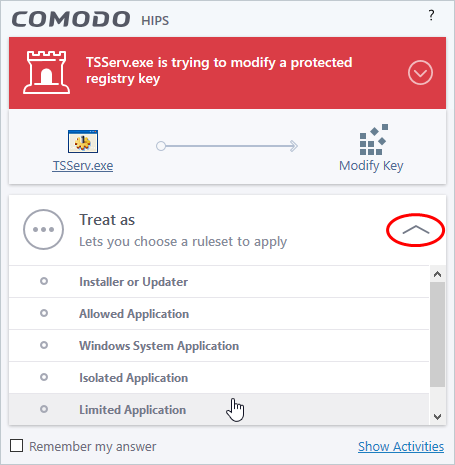
Avoid using the Installer or Updater ruleset if you are not installing an application. This is because treating an application as an 'Installer or Updater' grants maximum possible privileges onto to an application - something that is not required by most 'already installed' applications. If you select 'Installer or Updater', you may consider using it temporarily with Remember My Answer left unchecked.
-
Pay special attention to Device Driver Installation and Physical Memory Access alerts. Again, not many legitimate applications would cause such an alert and this is usually a good indicator of malware / rootkit like behavior. Unless you know for a fact that the application performing the activity is legitimate, then Comodo recommends blocking these requests.
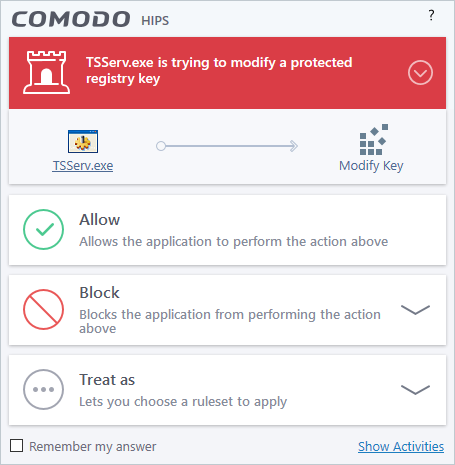
4. Protected Registry Key Alerts usually occur when you install a new application. If you haven't been installing a new program and do not recognize the application requesting the access , then a 'Protected Registry Key Alert' should be a cause for concern.
5. Protected File Alerts usually occur when you try to download or copy files or when you update an already installed application.
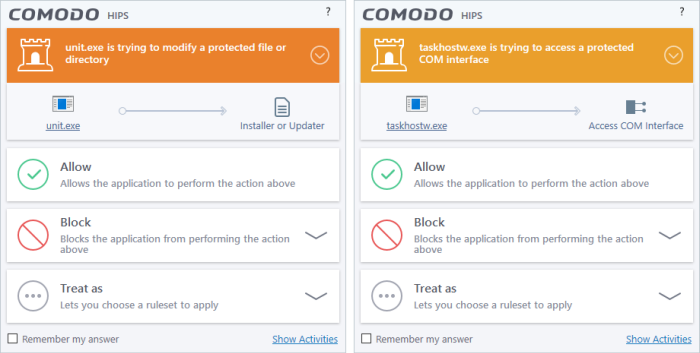
Were you installing new software or trying to download an application from the Internet? If you are downloading a file from the 'net, select Allow, without selecting Remember my answer option to cut down on the creation of unnecessary rules within the firewall.
If an application is trying to create an executable file in the Windows directory (or any of its subdirectories) then pay special attention. The Windows directory is a favorite target of malware applications. If you are not installing any new applications or updating Windows then make sure you recognize the application in question. If you don't, then click Block and choose Block Only from the options, without selecting Remember My answer option.
If an application is trying to create a new file with a random file name e.g. "hughbasd.dll" then it is probably a virus and you should block it permanently by clicking Treat As and choosing 'Isolated Application' from the options.
-
If a HIPS alert reports a malware behavior in the security considerations area then you should Block the request permanently by selecting Remember My Answer option. As this is probably a virus, you should also submit the application in question, to Comodo for analysis.
-
Unrecognized applications are not always bad. Your best loved applications may very well be safe but not yet included in the Comodo certified application database. If the security considerations section says "If xxx is one of your everyday applications, you can allow this request", you may allow the request permanently if you are sure it is not a virus. You may report it to Comodo for further analysis and inclusion in the certified application database.
-
If HIPS is in 'Paranoid' mode, you probably are seeing the alerts for any new applications introduced to the system - but not for the ones you have already installed. If required, you may review files with 'Unrecognized' rating in the 'File List' interface and remove them from the list.
-
Avoid using Trusted Application or Windows System Application policies for you email clients, web browsers, IM or P2P applications. These applications do not need such powerful access rights.
Comodo Client Security generates
a Containment alert if an application or a process tries to perform
certain modifications to the operating system, its related files or
critical areas like Windows Registry and when it automatically
contained an unknown application.
Please read the following advice before answering a Containment alert:
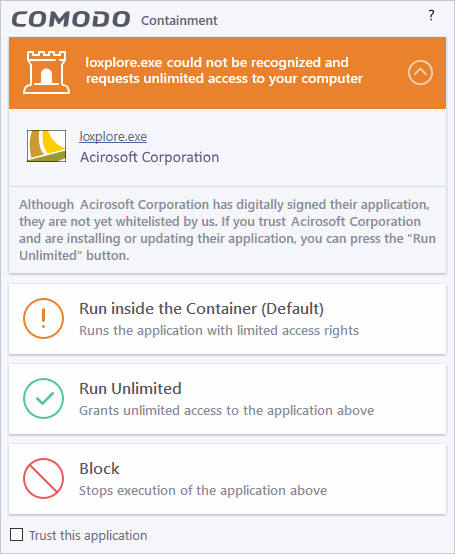
-
Carefully read the information displayed after clicking the handle under the alert description. Comodo Client Security can recognize thousands of safe applications. If the application is known to be safe - it is written directly in the security considerations section along with advice that it is safe to proceed. Similarly, if the application is unknown and cannot be recognized, you are informed of this.
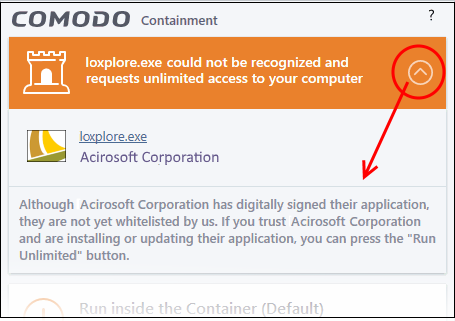
-
If you are sure that the application is authentic and safe and you simply want it to be allowed to continue then you should select Run Unlimited. If you want the application not to be monitored in future, select 'Trust this application' checkbox. The application will be added to Trusted Files list.
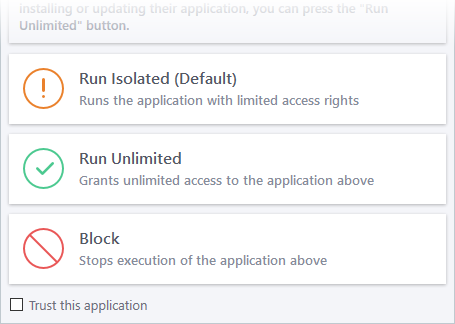
- If you are unsure of the safety of the software, then Comodo recommends that you run it with limited privileges and access to your system resources by clicking the 'Run Isolated' button. See Unknown Files: The Scanning process for more explanations on applications run with limited privileges.
- If you don't recognize the application then we recommend you select to 'Block' the application.
Run with Elevated Privileges Alert
The container will display this kind of alert when the installer of an unknown application requires administrator, or elevated, privileges to run. An installer that is allowed to run with elevated privileges is permitted to make changes to important areas of your computer such as the registry.
- If you have good reason to trust the publisher of the software then you can click the 'Run Unlimited' button. This will grant the elevated privilege request and allow the installer to run.
- If you are unsure of the safety of the software, then Comodo recommends that you run it with restricted access to your system resources by clicking the 'Run Isolated' button.
- If this alert is unexpected then you should abort the installation by clicking the 'Block' button (for example, you have not proactively started to install an application and the executable does not belong to an updater program that you recognize).
- If you select 'Trust this application' then CCS will include this to Trusted Files list and no future alerts will be generated when you run the same application.
|
Note: You will see this type of alert only if you have enabled the 'Detect programs which require elevated privileges e.g. installers or updaters' option and disabled the 'Do not show privilege elevation alerts' option in containment settings. See 'Containment
Settings' for more details. |
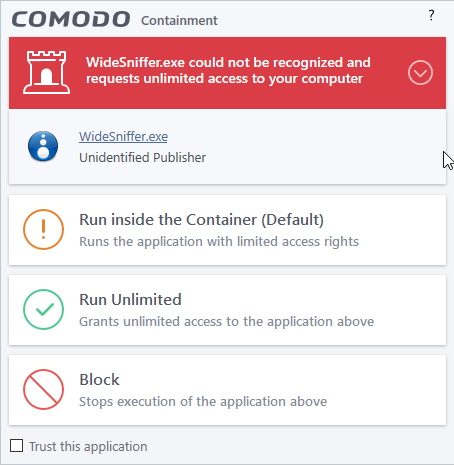
There are two versions of this alert - one for unknown installers that are not digitally signed and the second for unknown installers that are digitally signed but the publisher of the software has not yet been white-listed (they are not yet a 'Trusted Software Vendor').
Unknown and not digitally signed
Unknown and digitally signed but the publisher not yet whitelisted (Not yet a 'Trusted Vendor')
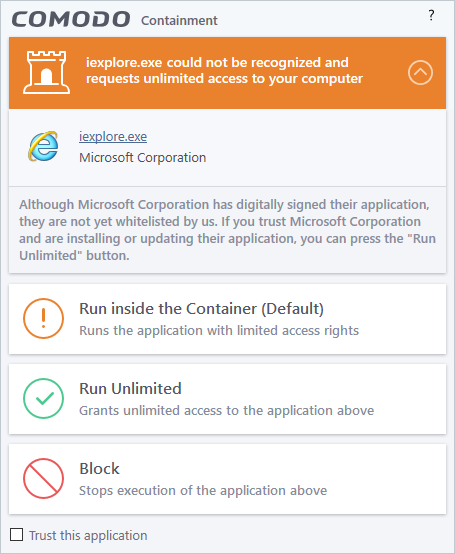
- Unknown and unsigned installers should be either isolated or blocked.
- Unknown but signed installers can be allowed to run if you trust the publisher, or may be isolated if you would like to evaluate the behavior of the application.
Also see:
- 'Unknown Files: The Scanning Processes' - to understand process behind how CCS scans files.
- 'Vendor List' - for an explanation of digitally signed files and trusted software vendors.
CCS shows a notification when it run an application inside the container. This usually happens if the application has an 'unknown' trust-rating.
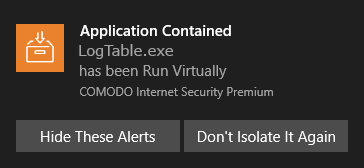
- Hide These Alerts - CCS will not show an alert if the same app is auto-contained in future.
- Don't
Isolate It Again - The application will not be auto-contained in
future. An 'Ignore' rule is created for the application in
auto-containment rules. SeeAuto-Containment
Rules for more details.
CCS checks a file's trust rating on our cloud severs as part of a real-time scan. The software can generate alerts when it finds a file with 'Malicious' rating.
You will see these alerts if you have disabled 'Do not show popup alerts' in 'Settings' > 'File Rating' > 'File Rating Settings'.
An example alert is shown below:
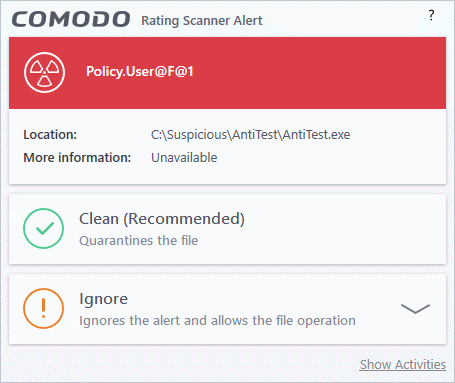
You can choose from these actions:
- Clean - The program is blocked and quarantined
- Ignore - Allows the file to run. Does not attempt to clean the file or move it to quarantine. Only click 'Ignore' if you are absolutely sure the file is safe. Clicking 'Ignore' will open three further options:
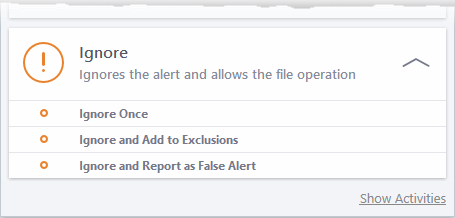
- Ignore Once - The file is allowed to run this time, but it will still be flagged as a threat by future scans.
- Ignore and Add to Exclusions -The file is allowed to run this time, and will not be flagged as a threat in future scans. The file is placed on the Exclusions list, meaning it is ignored permanently by the scanner.
- Ignore and Report as a False Alert - The file is allowed to run this time, and submitted to Comodo for analysis. Select this option if you think the file is safe, and that CCS was wrong to flag it as a threat. Comodo will re-examine the file.
Comodo Client Security generates a VirusScope alert if a running process performs an action that might represent a threat to your privacy and/or security. Please note that VirusScope alerts are not always definitive proof that malicious activity has taken place. Rather, they are an indication that a process has taken actions that you ought to review and confirm because they have the potential to be malicious. You can review all actions taken by clicking the 'Show Activities' link.
Please read the following advice before answering a VirusScope alert:
-
Carefully read the information displayed in the alert. The 'More Information' section provides you the nature of the suspicious action.
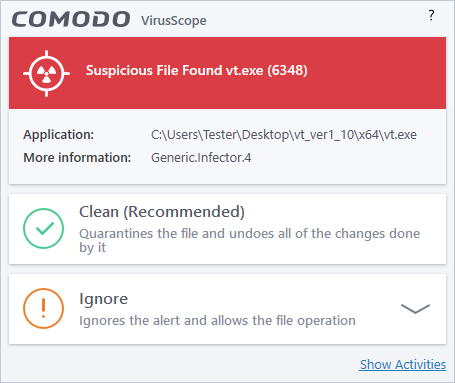
- If you are not sure on the authenticity of the parent application indicated in the 'Application' field, you can safely reverse the changes effected by the process and move the parent application to quarantine by clicking 'Clean'.
- If it is a trusted application, you can allow the process to run, by clicking 'Ignore' and selecting the option from the drop-down.
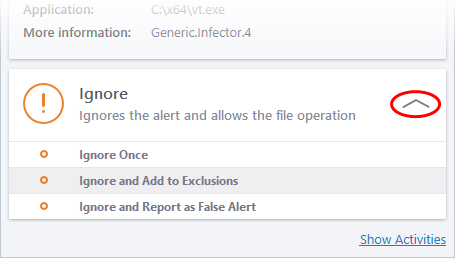
- Ignore Once - The process is allowed to run this time only. Another alert is shown if the process attempts to execute on future occasions.
- Ignore and Add to Exclusions - The file is allowed to run and will not be contained in the future. See Auto-Containment Rules for help to configure which types of files should be auto-contained.
- Ignore and Report as False Alert - Select this if you think the file is trustworthy and CCS is wrong to block it. CCS will submit the file to Comodo for analysis. If the false-positive is verified (and the file is trustworthy), it will be added to the Comodo safe list.
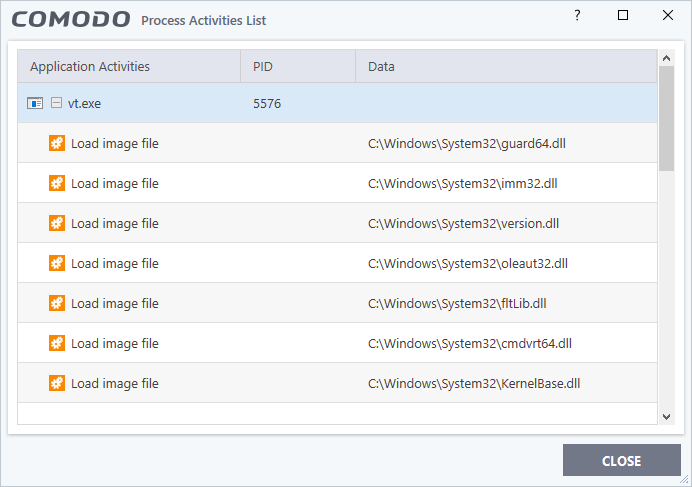
- Application Activities - The action executed by each of the processes run by the parent application.
- File actions: The process performed a file-system operation (create/modify/rename/delete file) which you might not be aware of.
- Registry: The process performed a registry operation (created/modified a registry key) which might not be authorized.
- Process: The process created a child process which you may not have authorized or have been aware of.
- Network: The process attempted to establish a network connection that you may not have been aware of.
- If the process has been terminated, the activities will be indicated with gray text and will appear in the list until you view the 'Process Activities List' interface. If you close the interface and reopen the list within five minutes, the activities will appear in the list. Else, the terminated activities will not be shown in the list.
- PID - The process identification number.
- Data
- The file affected by the action.
These notifications are shown when you connect an external device to your computer (USB stick, external HDD etc). The alert indicates whether the device is allowed or blocked.
- You can add blocked devices in 'Settings' > 'Advanced Protection' > 'Device Control'
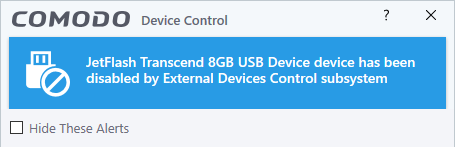
- See Device Control Settings to find out more.



