Browser Settings Protection
Browsers that are protected include IE, Comodo Dragon, Ice Dragon, Firefox and Chrome. If protection is switched on, the blocked apps will be automatically added to the list. You can also manually add individual apps and configure their browser access settings.
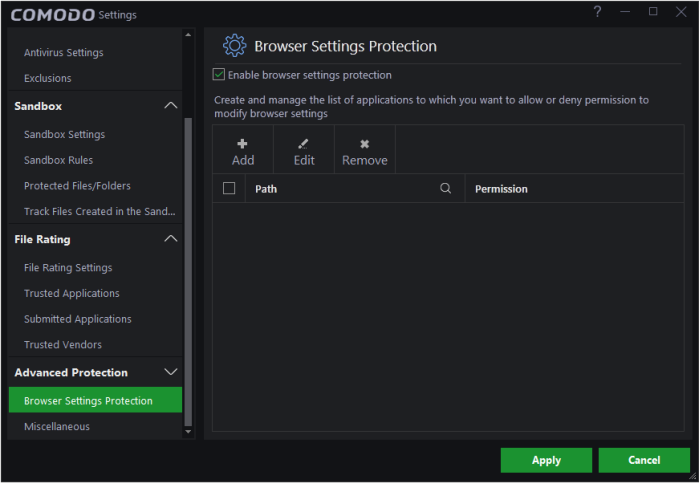
To open the 'Browser Settings Protection' interface
- Click 'Settings' at the top left of the CCAV home screen to open the 'Settings' interface
- Choose
'Browser Settings Protection' under 'Advanced Protection' on the
left
- Enable
browser settings protection - Switch
browser protection on or off.
- If disabled, any protection that you have created will be disregarded
- If the protection is switched on, the blocked apps will be automatically added to the list
The interface displays a list of applications added with the following details:
- Path - The installation path of the application.
- Permission – Indicates whether 3rd party applications are allowed to alter the browser settings or not.
You can search for specific
applications(s) from the list by clicking the search icon  in the
table header and entering the name of the browser in part or full.
in the
table header and entering the name of the browser in part or full.
You can add new a application and the protection status that should be applied to it.
To add applications to the protection list
- Click 'Add' at the top of the 'Settings' interface to open the 'Browser Settings' dialog.
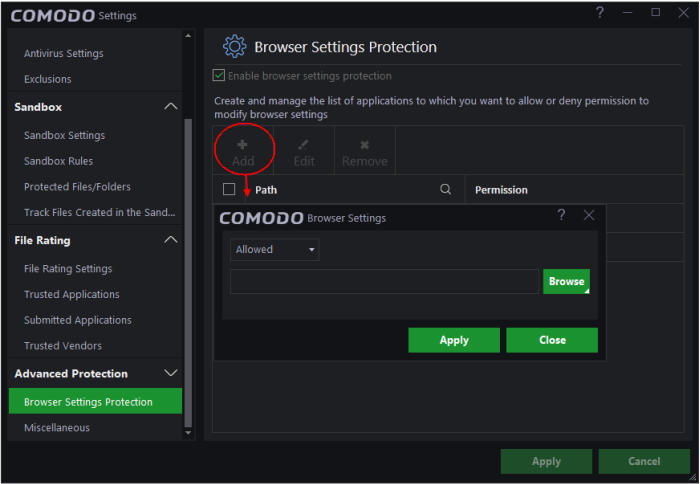
- Choose the action to be applied from the drop-down at the top.
The available choices are:
- Allowed – Browsers in the system will allow 3rd party applications to modify the settings, for example, to gather information by accessing cookies to analyze your browsing habits and so on.
- Not Allowed – CCAV will block 3rd party applications from altering browsers' settings and provide an alert.
- Next, specify the application for which the settings should apply. You have the following options:
- Enter the path of the application – Type or paste the full path of the application in the field provided.
- Browse your computer for the browser - Click the 'Browse' button and select 'Application', navigate to the application and click 'Open'
- Select an application from running processes - Click the 'Browse' button and choose 'Running Processes' to select an application's processes which are currently running on your PC.
- After choosing your application, click 'Apply' for your settings to take effect.
- Repeat the process to add more applications.
- Click 'Apply' from the 'Settings' dialog for your protection settings to take effect.
If you feel that a safe application is blocked from modifying the browsers' settings, you can edit the settings to allow it.
Editing browser settings
- Select and click the 'Edit' button at the top or simply double-click on it.
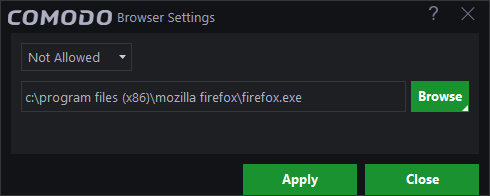
The edit dialog is same as 'Browser Settings' dialog. Refer to the explanation above for more details.
- To remove an application from the list, select the check-box next to the application's name and click 'Remove'.
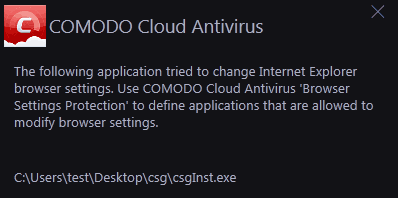
An example of the alert for a protected browser is shown below: