Run a Certificate Scan on Your Computer
- The 'Certificate Scan' feature examines all root SSL certificates installed on your computer and identifies all untrusted roots.
- Root certificates are used by browsers to validate the websites that you connect to. They are also used by operating systems to check the legitimacy of software that you download.
- For example, when you connect to a secure website, Mozilla Firefox and Google Chrome use these root certificates to check the SSL certificate on the website. If the website certificate is not signed by a trusted root then those browsers will warn you and recommend you do not continue. Similarly, Microsoft Windows uses these root certificates to check that any software you download is legitimate. If the software is not signed by a trusted root then Windows will warn you that you are taking a risk by installing it.
- All root certificates are embedded in what is known as the 'certificate store' in your Windows OS. If a malicious actor managed to get a root in your local certificate store then it could mean your browser and/or operating system would trust a fraudulent website or a piece of malware.
- A certificate scan will find all root certificates that are not part of the major root programs run by browsers and operating systems.
To run a Certificate scan
- Click 'Scan' on the CCAV home screen OR click the scan button on the widget
- Click
'Certificate Scan' in the scan options
page
The scan will check roots installed on your PC against the list of trusted store of roots:
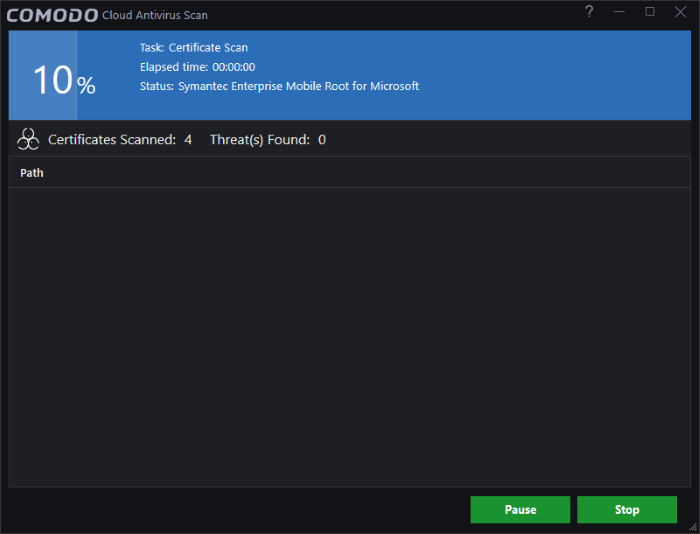
- You can pause, continue or stop the scan by clicking the appropriate button
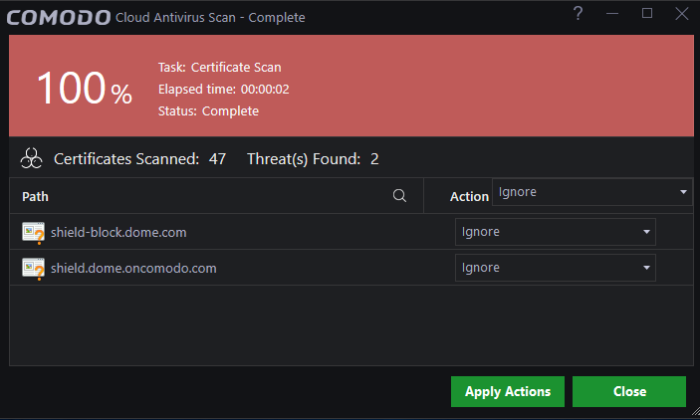
- The results show the total number of root certificates found on your system, and lists all untrusted certificates.
- You can take the following actions against untrusted certificates:
- Ignore – Will take no action on the certificate. The certificate will be flagged as untrusted by subsequent scans.
- Clean - Delete the certificate.
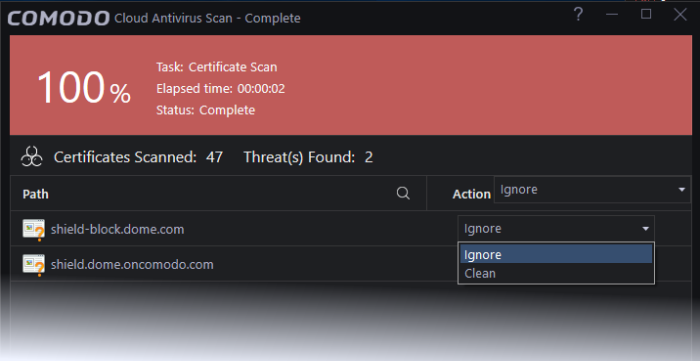
- Click
'Apply Actions' to implement your choices.



