Process Infected Files
The scan results screen lists all detected threats and allows you to take appropriate actions. You can quarantine the file, ignore the alert, trust the file or report it as a false positive.
- You can choose an action to be taken on all threats from the 'Action' drop-down at top right:
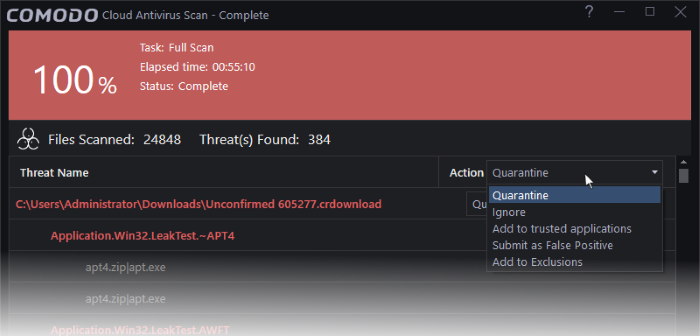
… or choose an action to be applied to individual items from the drop-down beside each item:
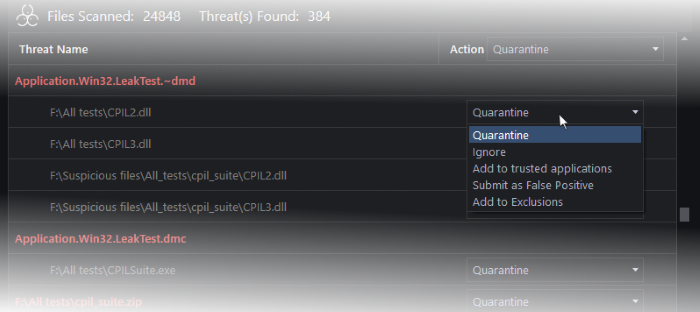
The available actions are:
- Quarantine – The files will be moved to quarantine. See 'View and Manage Quarantined Items' for more details on the quarantine feature.
- Ignore – If you want to ignore the threat the threat this time only, select 'Ignore'. The file will be ignored only at that time and if the same application invokes again, the AV scanner will report it as a threat.
- Add to trusted applications - If you trust the file, select 'Add to trusted applications'. The file will be assigned 'Trusted' status in the 'Trusted Applications'. The alert will not generated if the same application invokes again.
- Submit as False Positive - If you are sure that the file is safe, select 'Submit False Positive'. The file will be sent to Comodo for analysis. If the file is trustworthy it will be added to the Comodo safe list.
- Add to Exclusions - The file will be moved to an 'Exclusions' list maintained by CCAV and will not be scanned in future. The alert will not generated if the same application invokes again.
- After selecting the action(s) to be applied, click 'Apply'. The files will be treated as per the action selected and the progress will be displayed.
On completion the action taken against each threat will be displayed.
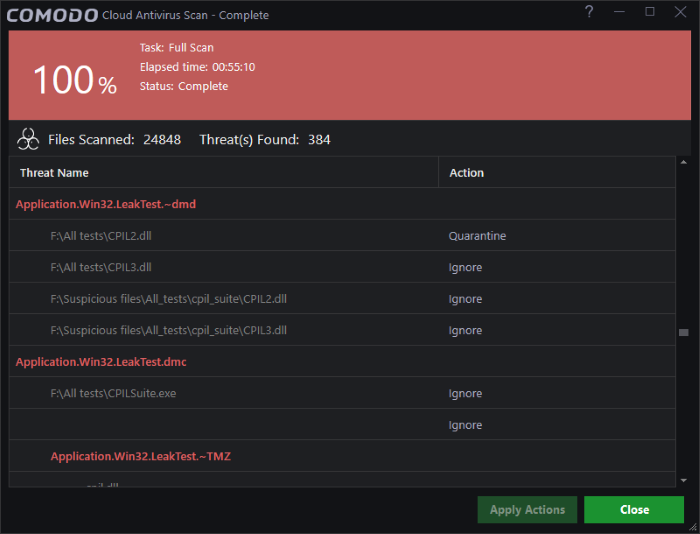
If you choose to close the results window without taking any action, the threats will be added to the 'Detected Threats' list.
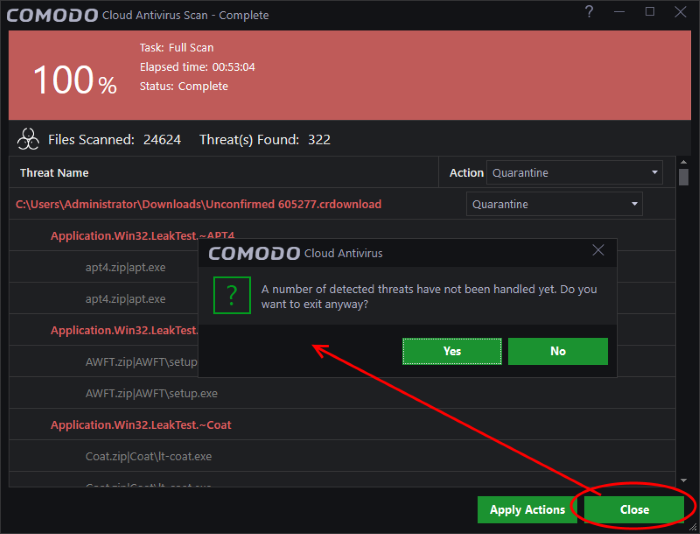
The 'Detected Threats' interface allows you to take action such as 'Quarantine', 'Trust' or 'Trust and Report False Positive' later on. See 'Manage Detected Threats' for more details.



