Manage
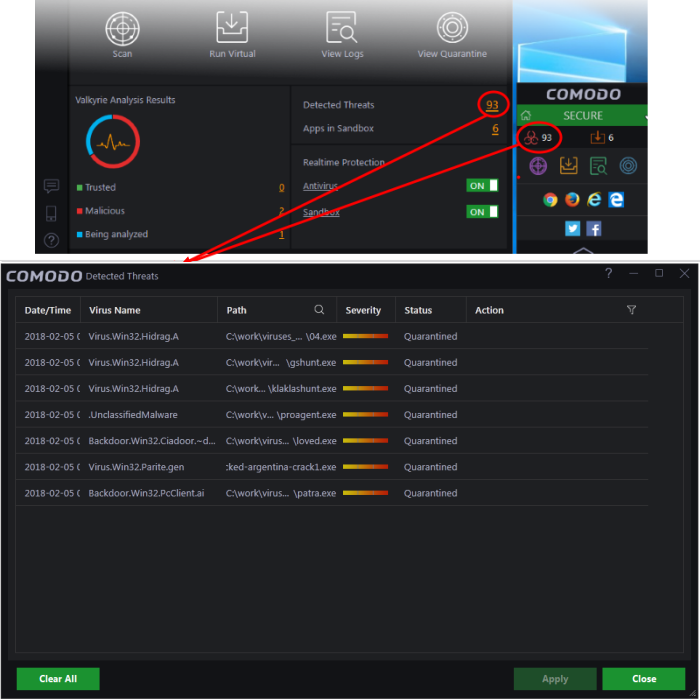
Detected Threats
- The 'Detected Threats' interface shows items identified as malicious, but which have yet to be processed.
- The interface also displays the current status of each item - whether it is quarantined, removed, trusted or submitted as a false positive to Comodo.
- You can also apply actions like move the detected threats to 'Quarantine' or 'Trusted files', or 'Submit as False Positive' to Comodo.
To open the 'Detected Threats' interface
- Click the number under 'Detected Threats' in the CCAV home screen.
- Alternatively, click the 'Detected Threats' icon on the widget.
Column Descriptions:
- Date/Time – The date and time at which the threat was detected
- Virus Name – The name of the malware contained in the application detected as threat
- Path – The location of the application in the system
- Severity – Indicates the risk level presented by the activity or request of the detected threat
- Status – Indicates the status of the action taken. It can be either 'Quarantined', 'Removed' and 'Trusted'
- Action - Displays a drop-down with options for handing the item:
The available actions are:
- Quarantine – Item will be moved to Quarantine and saved in an encrypted manner. You can analyze the item at a later time and:
- Restore it to the original location if it is trustworthy or
- Delete the item from your computer if it is a malware
from the Quarantine interface. See View and Manage Quarantined Items for more details.
- Trust – The item will be added to the Trusted Applications and will be excluded from the future scans. Choose this option only if the item is trustworthy.
- Submit as False Positive - The item will be added to the Trusted Applications and will be excluded from the future scans. Also it will be submitted to Comodo for analysis. If the file is found harmless by our experts, it will be added to the global safe-list.
- To
search for a specific application, click the search icon
beside the Path column header and enter the name of the application in part of full.
- To filter items by the action to be executed on them, click the funnel icon beside the 'Action' header and select an action:
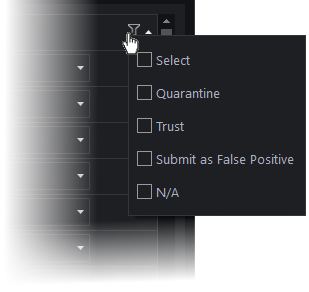
- To move an item to quarantine, choose 'Quarantine' from the 'Action' drop-down in the item row.
- To exclude an item from future scans, choose 'Trust' from the 'Action' drop-down in the item row
- To submit an harmless item identified as malware by Comodo Cloud Antivirus by mistake for analysis by Comodo, choose 'Submit as False Positive' from the 'Action' drop-down in the item row
- Click
'Apply' for your actions to take effect.



