Viruscope - Feature Spotlight
Comodo Cloud Antivirus (CCAV) provides unrivaled protection against new malware by automatically running unknown files inside a sandbox. Unknown files are those that are neither definitely bad (blacklisted malware) nor definitely good (whitelisted).
- If the file is harmless it will run as normal within the sandbox, meaning you will not notice any difference when using it.
- If the file turns out to be malicious, it will not have been able to cause damage because it was denied access to your data and the underlying operating system.
But what do we do to evaluate the behavior of unknown files in the sandbox? Enter Viruscope.
Viruscope is a behavior analysis
technology built into Comodo Cloud Antivirus that monitors the activities of sandboxed
processes and installers and alerts you if they take actions that
could threaten your security.
You will see an alert if Viruscope discovers a sandboxed process or an installer/updater is behaving in a suspicious manner:
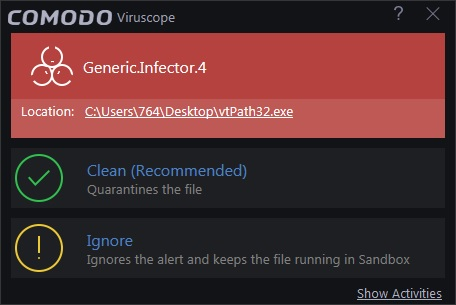
- If you are not sure of the authenticity of the parent application indicated in the 'Location' field, you can move it to quarantine by clicking 'Clean'.
- If it is an application you trust, you can allow the process to run by clicking 'Ignore'.
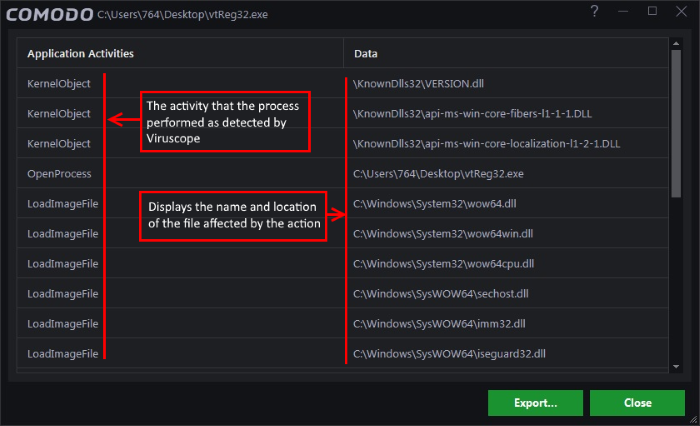
- To view the activities of process, click the 'Show Activities' link at the bottom right of the alert:
Viruscope identifies zero-day malware by using a sophisticated set of behavior 'Recognizers', each of which can detect actions typical of a malicious application.
What are behavior recognizers?
Viruscope behavior recognizers detect suspicious activities in multiple functional areas. Recognizers monitor the following activity events:
File activities:
- Create/Modify/Rename/Delete file.
- Set file attributes.
- Set file time to past.
Registry activities:
- Create/Rename/Delete registry key.
- Set/Delete registry key value.
Process activities:
- Create/Terminate process.
- Load file image.
- Other process activities.
Technically, the core Viruscope technology contains the following items:
- Tree of all active processes. This tree includes all processes-tracked or not.
-
Queue of activities. IO threads receive activities from a target application and pushes them to a queue. These activities are then processed sequentially by a worker thread.
- Per-process
activity list. Each process has a list of activities which belong to
it. A Viruscope worker thread audits all activities executed by a
running process and adds them to the activity list for this
particular process.
It will use these items to execute the following tasks:
- After queuing the activities of each process, the worker thread will sequentially send each one to the behavior recognizers for analysis.
- A recognizer may traverse the entire process tree and activity list created by Viruscope.
- A recognizer may build its own process tree (the default recognizer uses this technique) and/or queue of activities (the default recognizer doesn't use a cache of activities)
This flowchart describes the activity inspection process of a sample Viruscope recognizer:
Viruscope is another key layer of security in the CCAV arsenal, taking our protection beyond that found in any other antivirus product. Our real-time virus monitor protects you against known threats, while auto-sandboxing protects you against unknown threats. With Viruscope on top, you also get proactive warnings about brand new malware.



