Installation
Note - Before beginning installation, please ensure you have uninstalled any other antivirus products, including Comodo CIS/CES. Failure to remove other AV products could lead to conflicts which cause CCAV to function incorrectly. We advise users consult their vendor documentation for help to remove specific programs. However, the following steps should help most Windows users:
- Click the Windows 'Start' button
- Select 'Control Panel' > 'Programs and Features' (Win 10, Win 8, Win 7, Vista), or 'Control Panel' > 'Add or Remove Programs' (XP)
- Select your current antivirus program(s) from the list
- Click 'Remove/Uninstall'
- Repeat the process until all required programs have been removed
Installation
- Download and install Comodo Cloud Antivirus from https://antivirus.comodo.com/cloud-antivirus.php)
- The first step is language selection:

- Use the drop-down menu to select the language that you want to see in the CCAV interface
- Click 'I agree' to begin the installation wizard. This will start the installation of CCAV and, if you do not have it installed already, Comodo Internet Security Essentials (CISE). See Comodo Internet Security Essentials to find out more about CISE.
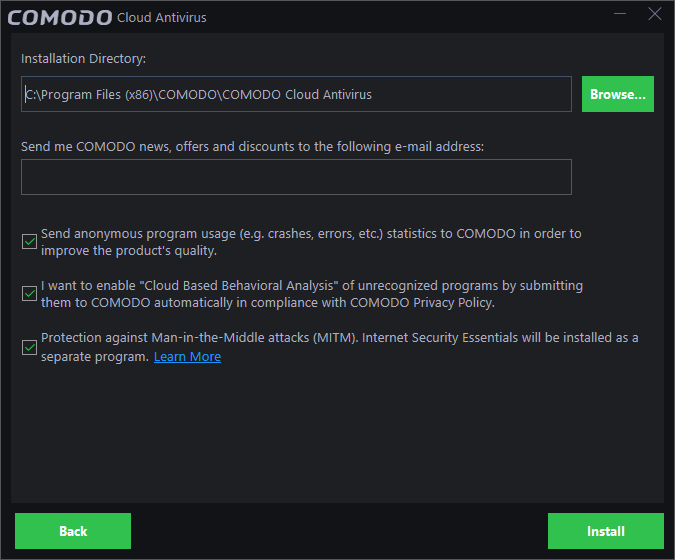
- The default install location is C:/Program Files(x86)/COMODO/COMODO Cloud Antivirus. Click the 'Browse...' button if you want to install to a different folder.
- Enter your email address in the second field if you would like to subscribe for Comodo news and get offers and discounts from Comodo.
Send
anonymous program usage data
If enabled, CCAV will send
anonymous crash and usage data to Comodo. This helps us troubleshoot
issues faster and better understand how our users interact with CIS,
so helping us to improve the product. Your privacy is protected
because all data is anonymized and sent over a secure and encrypted
channel. Disable this option if you do not want to send usage
details.
Cloud
Based Behavior Analysis
If enabled, any file that is
identified as unknown is submitted to Comodo Valkyrie for behavior
analysis. Unknown files are subjected to a range of static and
dynamic tests to determine whether they behave in a malicious
manner. The results will be sent back to your computer in around 15
minutes. Comodo recommends users leave this setting enabled.
Protection
against Man-in-the-Middle attacks (MITM)
Will also
install Comodo Internet Security Essentials (CISE). CISE protects
you online by verifying that the websites you visit are using SSL
certificates signed by a trusted CA. This option is not shown if you
already have CISE installed.
- Click
the 'Install' button to begin
installation:
- Click 'Finish'
CCAV will automatically launch a quick scan of important areas. Areas scanned include system memory, auto-run entries, start-up items, hidden services, boot sectors and other critical areas.
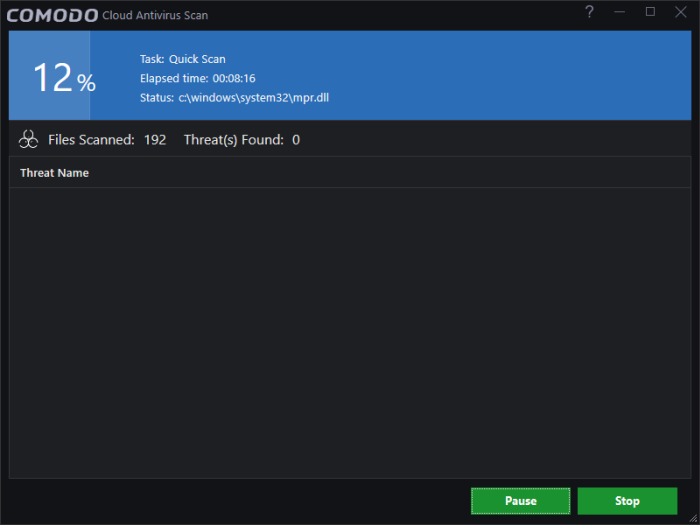
- Click 'Pause' to postpone the scan.
- Click
'Continue' to restart the scan.
The scan results show the number of files scanned and any threats found:
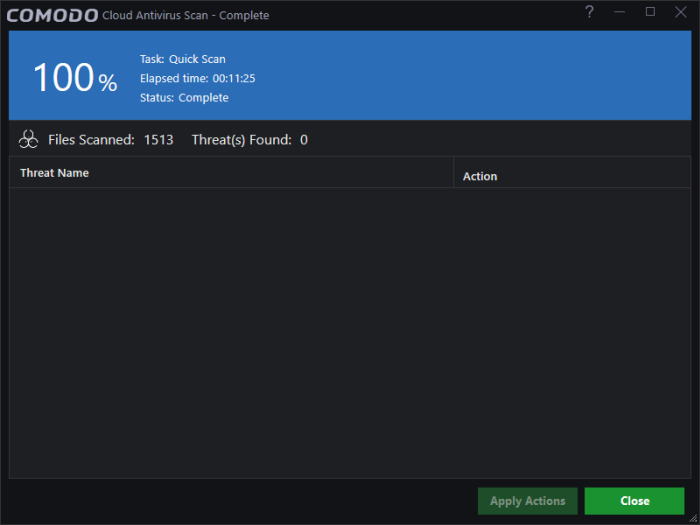
See 'Process
Infected Files' if you want to learn more about the actions you can take on detected malware.
- Click 'Close' after the scan is completed.
You will be prompted to restart the system after the scan. Please note that the application will work to its full potential only after the restart.
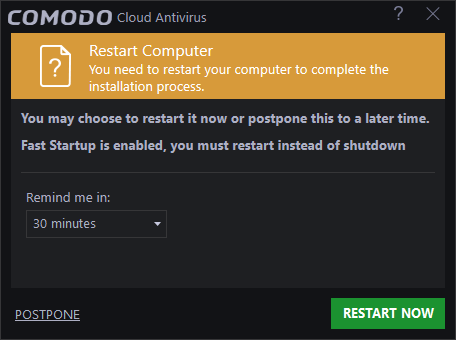
- Click 'Restart Now' if you want to restart the computer immediately. Save all your work first.
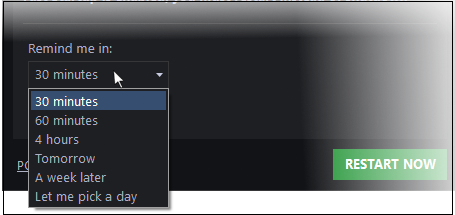
- 'Remind me in:' - Choose a more convenient time to restart your system
- Click 'Postpone' to confirm the later restart time.
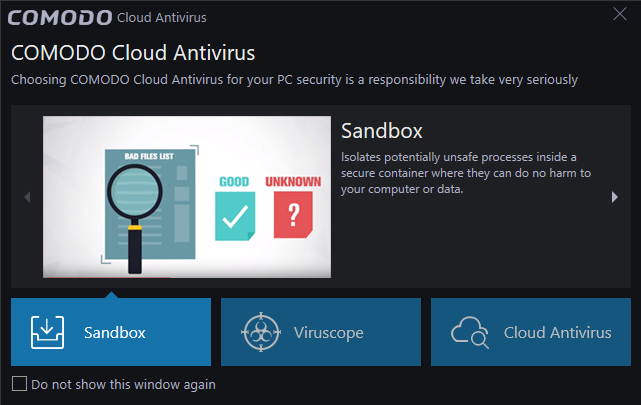
- The welcome screen will appear after you restart. The welcome screen contains useful product information and is updated frequently.
- Select 'Do not show this window again' if you would rather not see this screen.
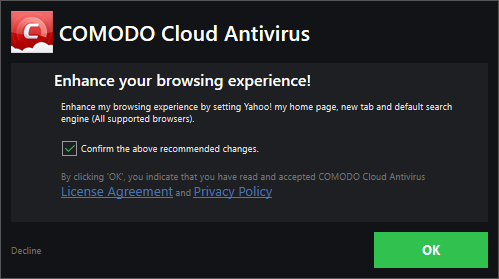
You will be offered the opportunity to set your search engine provider to Yahoo:
Currently supported browsers are Mozilla Firefox, Google Chrome, Internet Explorer, Comodo Dragon, Comodo IceDragon and Opera.
- Making Yahoo! your default search engine means:
- When you enter a search item into the address bar of a supported browser, the search will be carried out by Yahoo
- A ‘Search with Yahoo’ menu entry will be added to the right-click menu of supported browsers
- Yahoo will be set as the default search engine in the ‘Search’ box of supported browsers
- The instant ‘search suggestions’ that you see when you start typing a search item will be provided by Yahoo!
- Click 'Decline' to continue using your current search engine and home page.
The CCAV widget is displayed every time you start your computer. It contains five rows with shortcuts for different CCAV tasks:
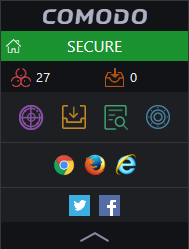
- The top row shows the current security status of your computer. Click the row to open CCAV.
- The second row shows how many threats were detected by the antivirus, and how many apps are running in the sandbox.
- The third row contains shortcuts for common CCAV tasks:
- Start a scan
- Select an application and run it in the Sandbox
- View logs
- View quarantine
- The fourth row has shortcuts which launch your browsers inside the secure container. Browsers inside the container are isolated from the rest of your computer and your private data, protecting you from online threats.
- The fifth row contains shortcuts to social networking sites like Twitter and Facebook.



