Respond to Alerts
Comodo Cloud Antivirus alerts provide warnings about security threats. You should understand how to respond to these alerts to ensure the safety of your computer.
There are
three categories of alerts:
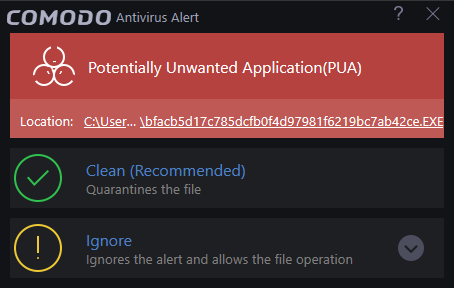
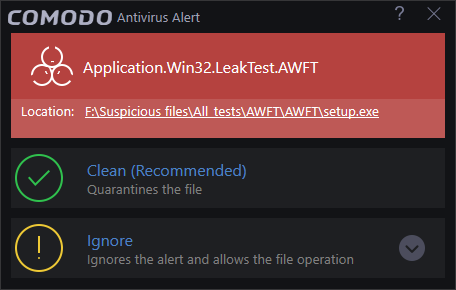
The AV alert will be shown when your computer encounters malware. The alert message contains the name of the virus detected and the location of the file or application infected.
Note: Realtime scanning must be enabled to activate this type of alert (highly recommended).
When you
receive an AV alert, the following options are available:
- Clean - Disinfects the file if a disinfection routine exists. If no routine exists for the file then it will be moved to Quarantine.
- Ignore - Allows the process to run and does not attempt to clean the file or move it to quarantine. Click 'Ignore', only if you are sure the file is safe. Clicking 'Ignore' will open three further options:
- Ignore Once - The file is allowed to run temporarily. Another alert will shown by the real-time scanner the next time the file runs. It will also be flagged the next time you run an antivirus scan.
- Ignore and Add to Whitelist - The file is allowed to run and is added to Trusted Applications. The file will no longer be flagged as malicious by the antivirus.
- Ignore and Report as False Alert - Allows the process to run and the file will be submitted as false positive and added to the trusted applications list.
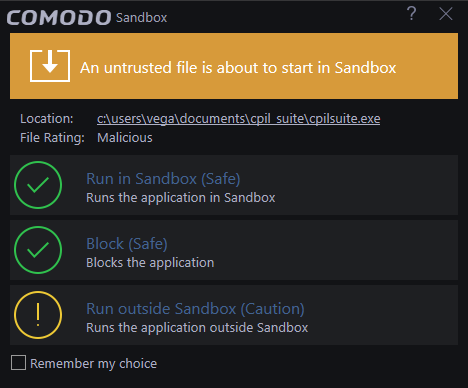
Sandbox alerts are shown when an untrusted application is opened. The alert presents you with the following options:
- Run in Sandbox – Recommended. Runs the application in a secure, isolated environment. The application will not be able to modify other processes and will be completely blocked from making changes to your computer while in the sandbox.
- Block – Stops the application from running
- Run outside Sandbox – Allows the application to run as normal on your computer. Unless you are sure the application is safe, Comodo recommends you run unknown applications in the sandbox. The application will function as normal in the sandbox, but is prevented from causing damage to your computer.
Note: 'Enable Auto-Sandbox' must be switched on for you to receive this type of alert.
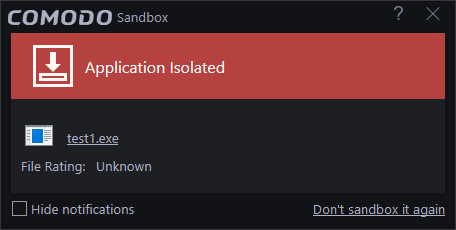
Note: If your sandbox setting is 'Sandbox all untrusted applications' then you will receive the “Application Isolated” alert for all untrusted files. You can choose to make it a trusted file by clicking “Don't sandbox it again”.
Note: You will get a sandbox notification whenever a tracked extension is created by an application in the sandbox.
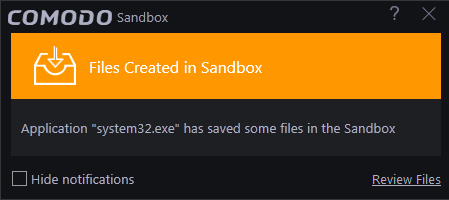
- Click 'Review Files' link to view the files. You can then move the files to your local drive if required.
This
alert is shown when applications in sandbox run unauthorized events
and when non- sandboxed programs like installers / updaters take
suspicious actions. You need to be watchful of alerts when you have
not made changes to your computer.
Note: You need to enable Viruscope in the sandbox settings to enable this alert.
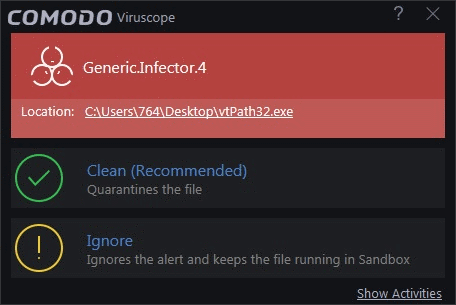
- Clean – Click 'Clean', If you are not sure of the authenticity of the parent application indicated in the 'Location' field to quarantine it
- Ignore – Click 'Ignore', if it is an application you trust, to allow the process to run
- Show Activities – Click this link at the bottom right, to view the list of activities exhibited by the process though the 'process activities List'
- This alert is shown whenever CCAV receives a verdict on an unknown file that was submitted to Valkyrie.
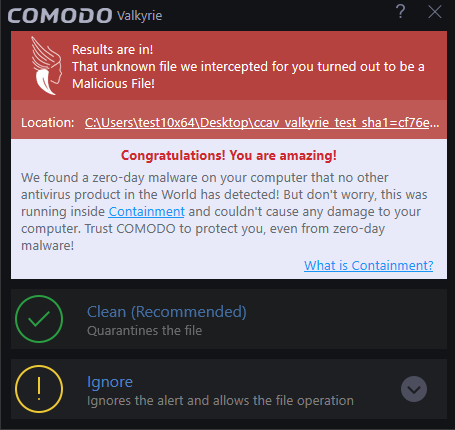
The following responses are available:
- Clean - Moves the file to 'Quarantine'.
- Ignore - Allows the file and does not attempt to clean the file or move it to quarantine. Only click 'Ignore' if you are absolutely sure the file is safe. Clicking 'Ignore' will open three further options:
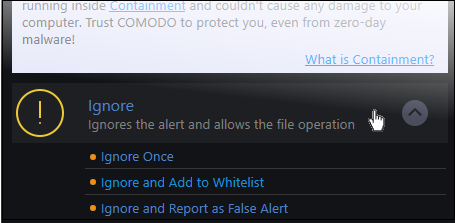
- Ignore Once - The file is allowed to run this time only. If the file attempts to execute on future occasions, another antivirus alert is displayed.
- Ignore and Add to Whitelist - The file is allowed to run and is moved to the safe file list - effectively making this the 'Ignore Permanently' choice. No alert is generated if the same application runs again.
- Ignore and Report as a False Alert - If you are sure that the file is safe, select 'Ignore and Report as a False Alert'. CCAV will then submit this file to Comodo for analysis. If the false-positive is verified (and the file is trustworthy), it will be added to the Comodo safe list.
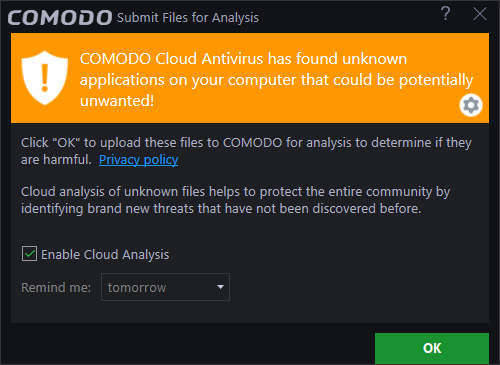
If you click 'OK' with this selected then these notifications will no longer be shown and unknown files will be automatically uploaded to Valkyrie in future. Clicking 'OK' also enables the 'I want to enable “Cloud Based Behavioral Analysis” of unrecognized programs...'option.
To select an option, deselect 'Enable Cloud Analysis' check box, select the option and click 'OK'.
- If you select the last option, 'Don't ask again', the notification will not be displayed anymore.
- If this option is selected then in order to submit unknown files automatically to Valkyrie, you have to enable the option in the 'Sandbox Settings' interface.
This alert is shown when an application attempts to change your browser settings for the first time (e.g. default search engine, home page, privacy setting etc).
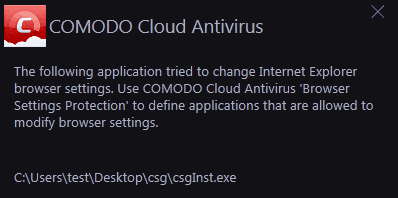
Blocked applications will automatically be added to the 'Browser Settings Protection' area of CCAV. You can subsequently change access permissions for each application from this interface. You can also use this interface to manually add applications that you want to restrict.
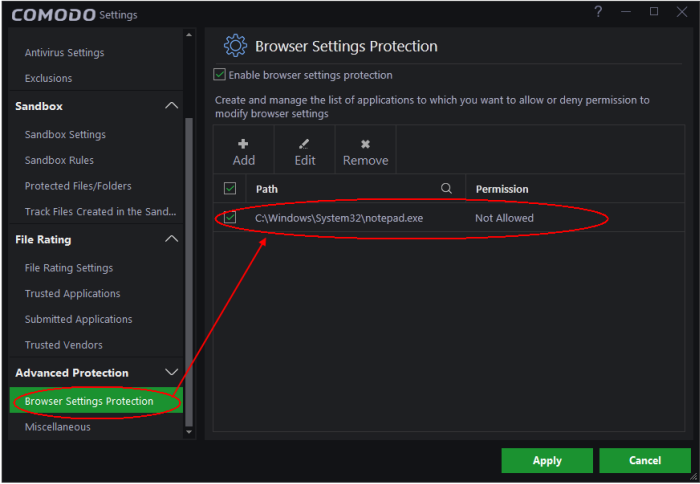
This alert is shown whenever the antivirus module encounters a crash. You can help Comodo rectify the issue by sending the error report to Comodo for analysis.
These alerts are shown if you attempt to download a piece of software from a domain that is known to serve potentially unwanted software (PUA). Example PUAs include adware and browser toolbars.