Trusted Applications
Files with a 'Trusted' rating are automatically allowed to run outside the sandbox. Files are given 'trusted' status if:
- The application is from a vendor included in the Trusted Software Vendors list;
- The application is included in the extensive and constantly updated Comodo safelist.
- User Rating – You can provide 'Trusted' status to your executables by adding it to the Trusted Applications list.
By granting 'Trusted' status to executables you can reduce the amount of alerts that the sandbox generates while maintaining a high level of security. This is particularly useful for developers that are creating new applications that are unknown to the Comodo safe list.
Creating your own list of 'Trusted Files' allows you to define a personal safe list of files to complement the default Comodo safe list.
The 'Trusted Applications' interface allows you to add and manage files to 'Trusted Applications' list.
To open the 'Trusted Applications' interface
- Click the 'Settings' icon at the top left of the CCAV home screen to open the 'Settings' interface
- Choose
'Trusted Applications' under 'File Rating' on the left
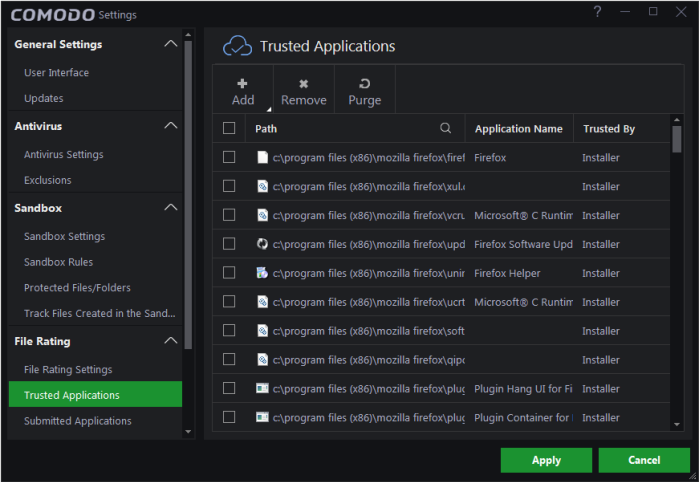
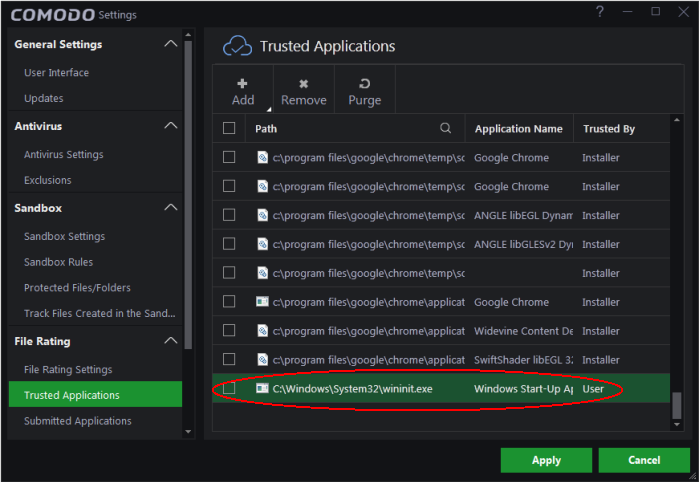
The interface displays a list of files added as 'Trusted Applications' with the following details:
- Path - The installation path of the application/executable file
- Application
Name – The name of the application/executable file
- Trusted by - Indicates who the changes were done by (User, Installer).
You can
search for specific application(s) from the list by clicking the
search icon  in the table header and entering the name of the
application in part or full.
in the table header and entering the name of the
application in part or full.
To add an item to the Trusted Applications list
- Click the 'Add' button at the top of the 'Trusted Applications' interface
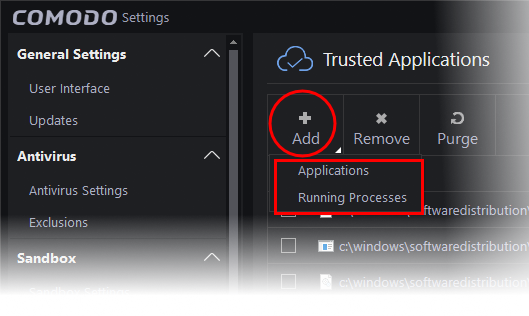
You can add an application by :
- Browsing your computer - Enables you to select files on your hard drive(s) that you want to add to your list of trusted applications.
- Selecting from running processes - Enables you to choose files from processes which are currently running on your system.
To add an application from your computer
- Choose 'Applications' from 'Add' drop-down
- Navigate to the file you want to add to 'Trusted Applications' in the 'Open' dialog and click 'Open'.
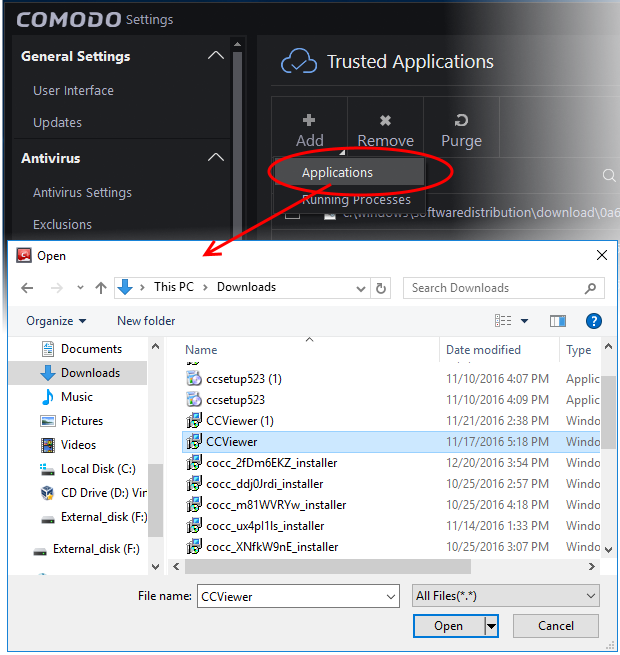
This file will now be added to the trusted applications list.
- Repeat the process to add more items
- Click 'Apply' to save your settings
To add applications from Running processes
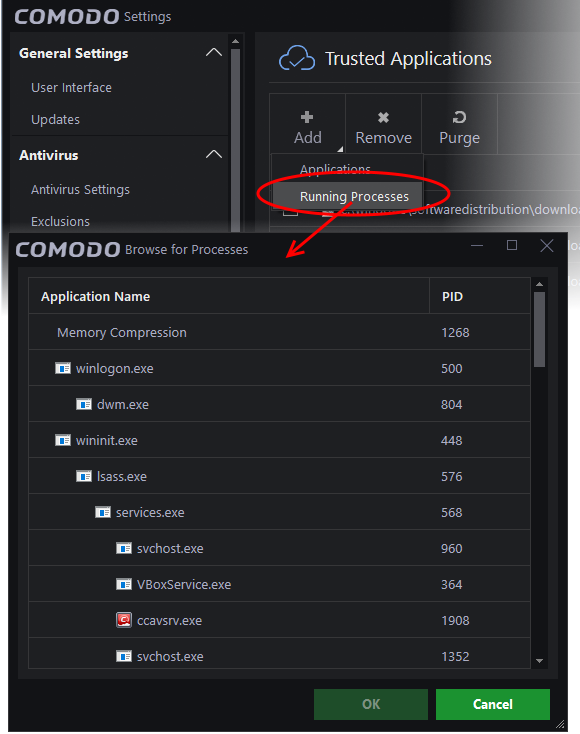
- Select the application from the running process you wish to add to trusted applications and click 'OK'.
The selected applications will be added to the 'Trusted Applications' list.
- Repeat the process to add more items
- Click 'Apply' to save your settings
To remove item(s) from the Trusted Applications list
- Select items to be removed from the Trusted Applications list and click the 'Remove' button at the top
- Click 'Apply' for your changes to take effect
To Purge item(s) from the Trusted Applications list
- Click 'Purge'
CCAV will verify that all files in the list are actually installed on your computer at the paths specified. If not, the file will be removed ('purged') from the list.



