View and Manage Quarantined Items
- The 'Quarantine' interface displays a list of files which have been isolated by Comodo Cloud Antivirus to prevent them from infecting your system.
- Items are generally placed in quarantine as a result of an on-demand or real time antivirus scan. Any files transferred to quarantine are encrypted, meaning they cannot be run or executed.
- You
can also manually quarantine items that are suspicious. Conversely,
you can restore a file to its original location if you think it has
been quarantined in error, and/or submit files as false positives to
Comodo for analysis.
- Click 'View Quarantine' on the main interface
OR
- Click the 'Quarantine' icon
 on the CCAV
desktop widget
on the CCAV
desktop widget
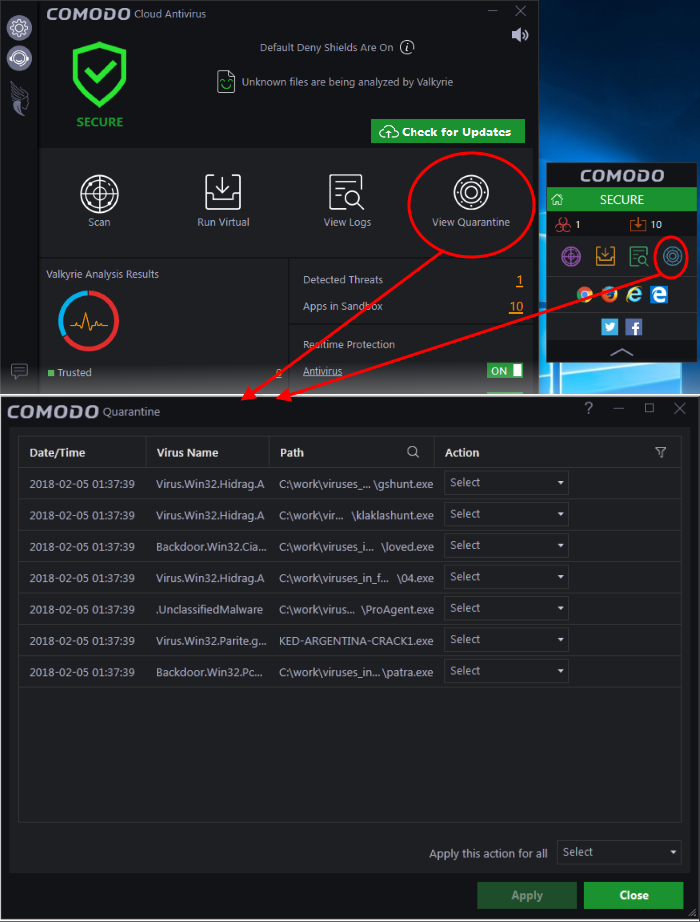
Column Descriptions
- Date/Time – The precise date and time at which the item was moved to quarantine
- Virus Name – The name of the malware that was quarantined
- Path – The location where the file was discovered
- Action - Displays a drop-down with options for handling
the item.
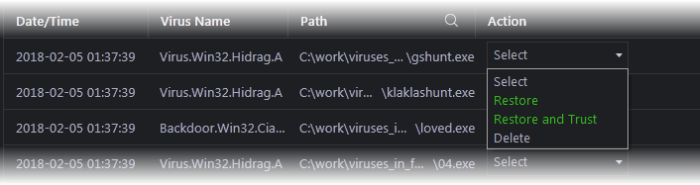
The available actions are:
- Restore – The item will be restored to its original location. However, subsequent scans will still identify it as malicious and will quarantine the file.
- Restore and Trust – The item will be restored to its original location and will be added to 'Trusted Applications' list in your local file list. The file will be excluded from future scans.
- Delete – The item will be removed from your computer.
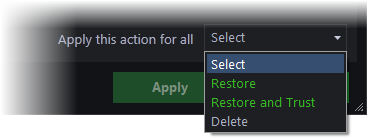
You can also apply an action to all quarantined items at once using the 'Apply this action for all' drop-down at bottom right:
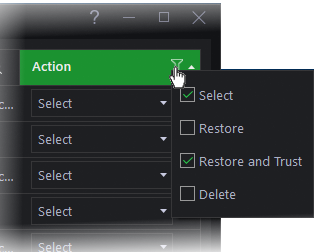
- To filter items based on the actions to be executed on them, click the funnel icon in the 'Action' column:
The 'Quarantine' interface also allows you to:
Manually adding files as Quarantined Items
Files or folders that you are suspicious of can be manually moved to quarantine:
To manually add a Quarantined Item
- Right-click anywhere inside the 'Quarantine' interface and choose 'Add'
- Navigate to the file you want to add to quarantine and click 'Open'.
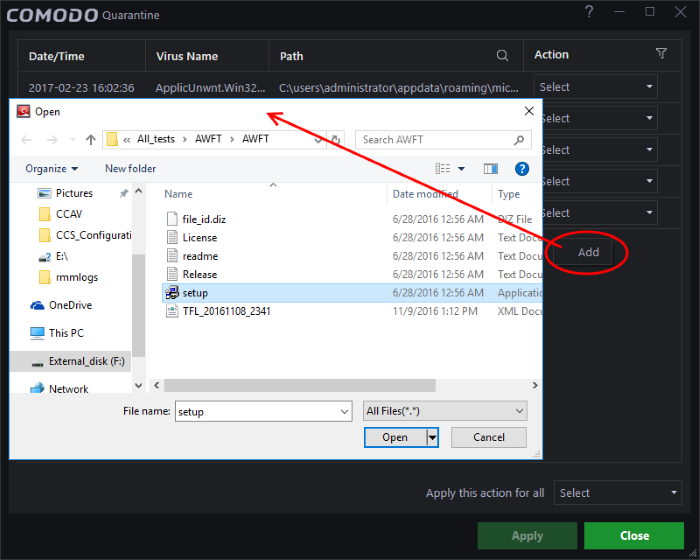
-
Click 'Apply' to quarantine the file
- To delete a single item, choose 'Delete' from the 'Action' drop-down in the item row.
- To delete all the quarantined items at once, choose 'Delete' from the drop-down beside 'Apply this action to all' at the bottom right of the interface.
- Click 'Apply' for your changes to take effect.
The file(s) will be deleted from the system permanently.
To restore quarantined item(s) to its/their original location(s)
- To restore a single item, choose 'Restore' from the 'Action' drop-down in the item row.
- To restore a single item and exclude it from future scans, choose 'Restore and Trust' from the 'Action' drop-down in the item row.
- To restore all items, choose 'Restore' from the 'Apply this action to all' drop-down at bottom right.
- To restore all items and exclude them from future scans, choose 'Restore and Trust' from the 'Apply this action to all' drop-down at bottom right.
- Click 'Apply' for your changes to take effect.
To
submit a selected quarantined item to Comodo for analysis
- Select the item from the 'Quarantine' interface, right click on it and choose 'Submit as False Positive' from the options.
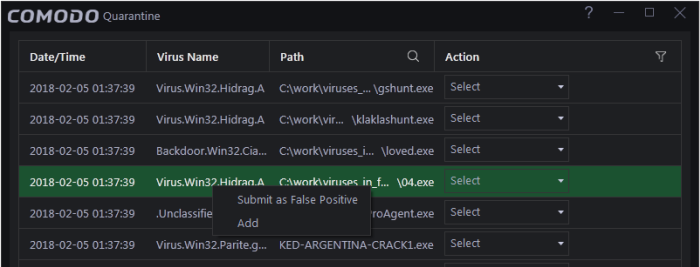
-
Click 'Apply' for your changes to take effect
You can submit suspicious files to
Comodo for deeper analysis. You can also submit files which you think
are safe but have been identified as malware by CCAV (false
positives). Comodo will analyze all submitted files.
- If they are
found to be trustworthy, they will be added to the Comodo safe list
(whitelisted).
- Conversely, if they are found to be malicious then
they will be added to the database of virus signatures (blacklisted).
|
Note: Quarantined files are strongly encrypted, cannot be executed and do not constitute any danger to your computer. |



