Miscellaneous Protection Settings
The 'Miscellaneous' panel allows you to:
- Configure heuristic command line analysis for certain applications
-
Configure protection against shellcode injections (buffer overflow attacks)
To open the 'Miscellaneous' settings interface
- Click 'Settings' at the top-left of the CCAV home screen
- Click 'Advanced Protection' > 'Miscellaneous':
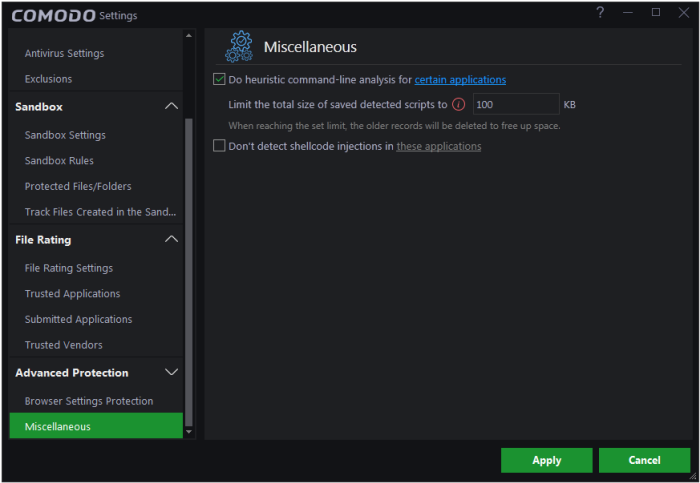
The interface allows you to:
Run heuristic analysis on certain applications
- This setting instructs CCAV to perform heuristic analysis on programs that execute code, like Visual Basic scripts and Java applications.
- Example file types that are checked are wscript.exe, cmd.exe, java.exe and javaw.exe.
- For example, the program wscript.exe can be made to execute Visual Basic scripts (.vbs file extension) via a command similar to 'wscript.exe c:/tests/test.vbs'. If this option is selected, CCAV detects c:/tests/test.vbs from the command-line and applies all security checks based on this file.
- If test.vbs attempts to connect to the internet, for example, the alert will state 'test.vbs' is attempting to connect to the internet.
Background note: 'Heuristics' is a security technique that checks whether software contains code typical of a virus. Heuristics is about detecting ‘virus-like behavior’ rather than looking for a precise virus signature that matches a signature on the virus blacklist. This helps to identify previously unknown (new) viruses.
Click the 'certain applications' link to view the list of programs that are included by default:
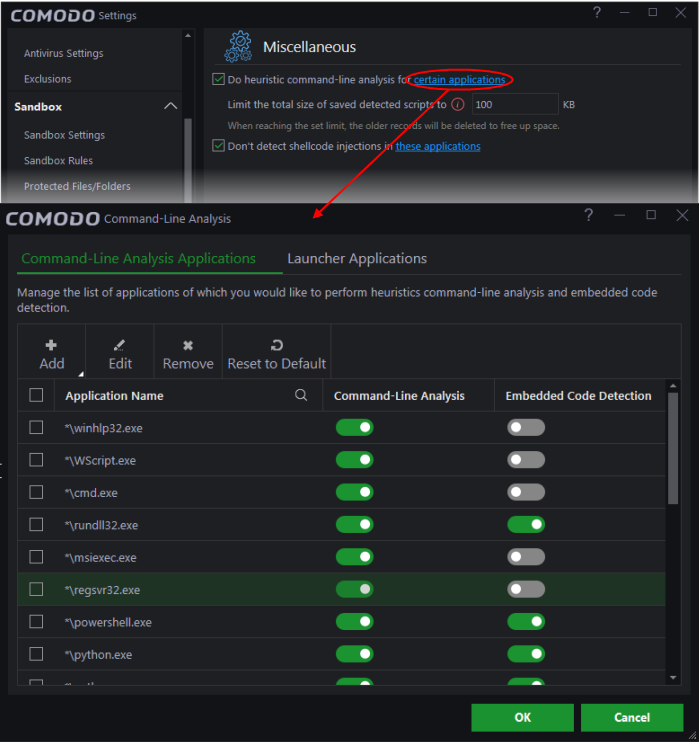
Command-line analysis - Allows CCS to analyze and apply security checks to scripts that are executed by a command line. For example, consider the line ' wscript.exe c:/tests/test.vbs'. If test.vbs attempts to connect to the internet, the subsequent alert will state 'test.vbs' is attempting to connect to the internet. If this option is disabled, the alert will only state 'wscript.exe' is trying to connect to the internet.
Embedded Code Detection - Embedded code detection protects you against fileless malware attacks. Fileless malware attacks allow malicious actors to directly execute Powershell commands on your system. These commands can be used to take control of your computer, install ransomware, steal confidential data and more. File-less scripts reside in memory so no trace of them remains after the computer is restarted.
Click the ‘Add’ button to add new
applications and processes to the list of analyzed items.
Disable shellcode injection detection
By default, shellcode injection protection is enabled for all applications on your computer. Use this setting to define applications which you do not want to be monitored for shellcode injections.
Background:
- Shellcode injection is a malicious technique which allows an attacker to cause a buffer overflow on your system.
- A buffer overflow occurs when a process attempts to store data beyond the boundaries of a fixed-length buffer. A buffer is an area of memory designed to hold a specific amount of data.
- The result is that the extra data overwrites adjacent memory locations. The overwritten data may include other buffers, variables and program flow data.
- Overflows can be caused by inputs specifically designed to execute malicious code or make the program operate incorrectly. As such, buffer overflows cause many software vulnerabilities and form the basis of many exploits.
To exclude certain applications from shellcode injection protection
- Make sure 'Don't detect shellcode injections' checkbox is enabled and click the 'these applications' link. The 'Manage Exclusions' dialog will appear.
- Click the 'Add' button at the top
You can add items by selecting the required option from the drop-down:
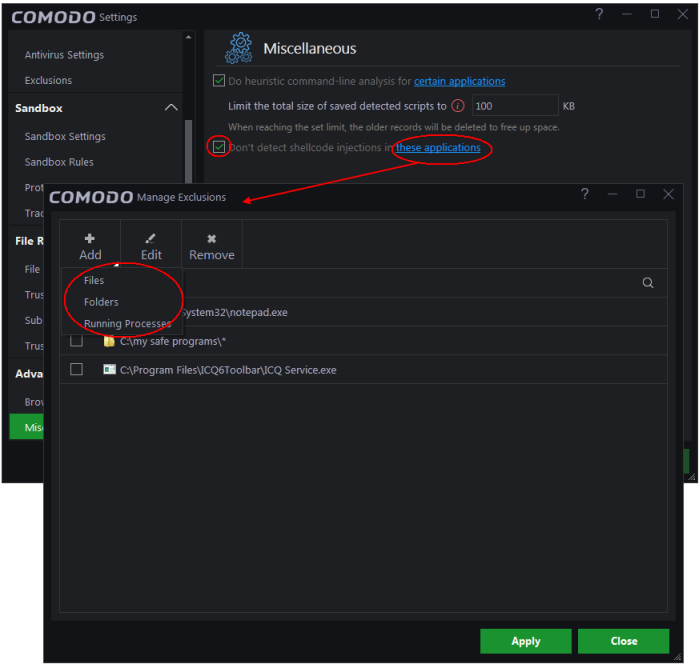
- File Groups - Select a category of pre-set files or folders.
For example, 'Executables' lets you create a ruleset for all files
with the extensions .exe .dll .sys .ocx .bat .pif .scr .cpl,
*cmd.exe *.bat, *.cmd. Other categories available include 'Windows
System Applications', 'Windows Updater Applications', 'Start Up
Folders' etc.
- Running Processes - As the name suggests, this option allows you to select an application or executable from the processes that are currently running on your PC.
- Folders - Opens the 'Browse for Folders' window and enables you to navigate to the folder you wish to add.
- Files - Opens the 'Open' window and enables you to navigate to the application or file you wish to add.



