Sandbox Settings
The sandbox settings area allows you to configure your overall sandbox policy.
To open sandbox settings
- Click the 'Settings' icon on the left then 'Sandbox' > 'Sandbox Settings'
OR
- Click the 'Sandbox' link under 'Realtime Protection' on the home screen
OR
- Right-click on the CCAV system tray icon (or the widget) and choose 'Sandbox Settings' from the options.
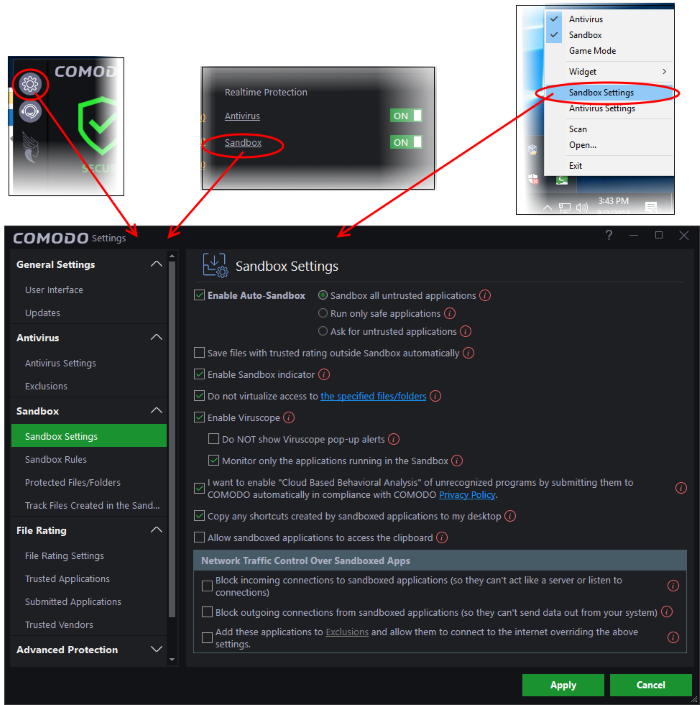
- Enable Auto-Sandbox - Switch automatic sandboxing on or off. Default = On.
- If you disable the sandbox, then any sandbox rules that you have created will be disregarded.
- If you enable the sandbox, you have the following options:
- Sandbox all untrusted applications - Comodo Cloud Antivirus will automatically run 'unknown' files and applications in the sandbox. A file can have one of three trust statuses – Trusted, Untrusted or Unknown. 'Trusted' files are those that are either on the Comodo white-list of known-good applications or have been manually trusted by the user. Trusted files are allowed to run outside the sandbox. 'Untrusted' files are malware and will be quarantined by the antivirus scanner. 'Unknown' files are those which are neither 'Trusted' nor 'Untrusted'. As their precise intentions are not yet known, we run these applications in in a secure virtual environment known as the 'sandbox'. If they later transpire to be malicious, they will not have been able to cause damage to your computer or data because they were isolated.
- Run only safe applications - Only applications from Trusted Vendors or those in your list of Trusted Applications will be allowed to run. All other applications will be blocked.
- Ask for untrusted files - Instead of automatically sandboxing unknown files, CCAV will show you an alert and offer you the choice of sandboxing the application or running it normally.
- Save file with trusted rating outside sandbox automatically' – If enabled, files saved in the sandbox which are subsequently found to be safe will be moved to your local hard drive. Default= Disabled. Click Trusted Applications to see what Comodo rates as 'Trusted'.
- Enable Sandbox indicator - CCAV will display a green border around an application if it is running in the sandbox. Disable this setting if you do not want to see this border.
- Do not virtualize access to the specified folders – By default, sandboxed applications can access folders and files on your computer but cannot save any changes to them. You can define exceptions to this rule by using the 'Do not virtualize access to...' links.
- Enable Viruscope - Viruscope monitors the activities of processes running on your computer and alerts you if they take actions that could potentially threaten your privacy and/or security. Viruscope alerts give you the opportunity to quarantine the process & reverse its changes or to let the process continue. Viruscope forms another layer of security on top of the core antivirus protection and helps CCAV to control and evaluate the behavior of sandboxed applications.
- Do NOT show Viruscope pop-up alerts - Configure whether or not CCAV should show an alert if Viruscope detects suspicious activity. Choosing 'Do not show' will minimize disturbances but at some loss of user awareness. If you choose not to show alerts then detected threats are automatically quarantined and their activities are reversed.
- Monitory only the applications running in the Sandbox - Choose whether Viruscope should monitor the activities of all running processes, or only processes which are sandboxed.
- I want to enable 'Cloud based Behavioral Analysis of unrecognized programs by submitting them to Comodo automatically in compliance with Comodo Privacy Policy' - Any file that is identified as unknown is sent to the Cloud server for behavior analysis. Each file is executed in a virtual environment on Comodo servers and tested to determine whether it contains any malicious code. The results will be sent back to your computer in around 15 minutes. If
you disable this setting, an alert to submit unknown files will be
displayed. See 'Understand
CCAV Alerts' for more
details.
- Copy any shortcuts created by sandboxed applications to my desktop - Will place a duplicate of any shortcuts created by sandboxed applications onto the desktop of your local machine. This allows you to open the application faster and also alerts you to the fact that the application created a shortcut. Clicking the local shortcut will run the application in the sandbox.
-
Allow sandboxed applications to access the clipboard – If enabled, you will be able to copy and paste content between sandboxed applications and non-sandboxed applications. This option is disabled by default.
- Net Traffic Control Over Sandbox Apps
- Block incoming connections to sandboxed applications (so they can't act like a server or listen for connections) - Will prevent sandboxed applications from accepting TCP internet connections from external sources. This stops potentially malicious applications from receiving instructions from their control server.
- Block outgoing connections from sandboxed applications (so they can't send data out of your system) - Will prevent sandboxed applications from making TCP internet connections to external sources. This stops potentially malicious applications from broadcasting your confidential data without your knowledge.
- Add these applications to Exclusions and allow them to connect to the internet by overriding the above settings - Specify applications which are allowed internet connectivity, even if sandboxed.
- To specify exceptions, select the option then click the 'Exclusions' link. Click 'Add' at top-left. Choose applications or running processes:
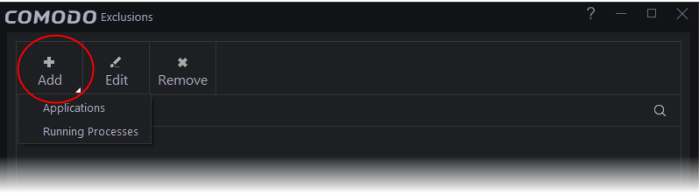
- Applications - Choose an installed programs that should be allowed to connect to the internet.
- Running Processes - Select an application from the list of currently running processes. The parent application of the chosen process will also be excluded.
- Click 'Apply' for your settings to take effect.



