Configure Security Modules that Store Certificates and Passwords
Comodo IceDragon contains built-in security modules to store your passwords and certificates securely. In addition for enhanced security, you can use external security devices like smart cards to store your certificates and passwords, and configure IceDragon to fetch your certificates and passwords from them.
Security modules
A Security Module or a PKCS#11 module is a program to manage encryption and decryption using the PKCS #11 standard. A PKCS #11 module can control a software security devices as well as hardware security devices like a smart card or token, in a reader inserted into a slot dedicated for the module
By default, Comodo IceDragon has two internal PKCS#11 security modules:
- NSS Internal PKCS #11 Module that controls two types of security devices:
- Generic Crypto Services - A special software security device for all cryptographic operations required by the Netscape Internal PKCS #11 Module.
- Software Security Device - A software security device for storing your certificates and passwords that cannot be stored on external security devices, including any CA certificates that you have installed in addition to default CA certificates that came with the browser.
- Builtin Roots Module controls a special security device called the Built-in Object Token.
- Builtin Object Token - A token that stores the default CA certificates that came with the browser.
Manage Security Modules
- Click the hamburger/ menu button at the top-right
- Select 'Options' > 'Privacy & Security' > scroll to the 'Certificates' then click 'Security Devices' button
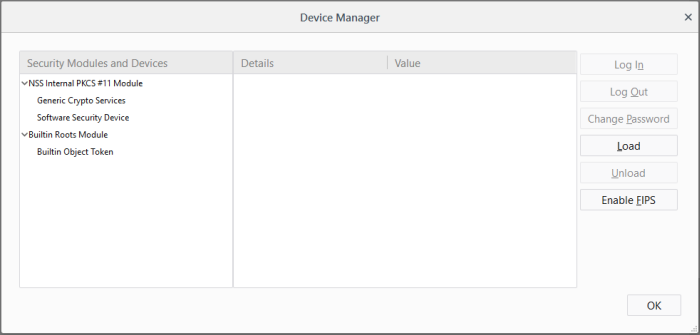
This dialog enables you to:
View the details of a security module or device
-
Click on the module or the device
-
The details of the module or the device is displayed in the middle pane
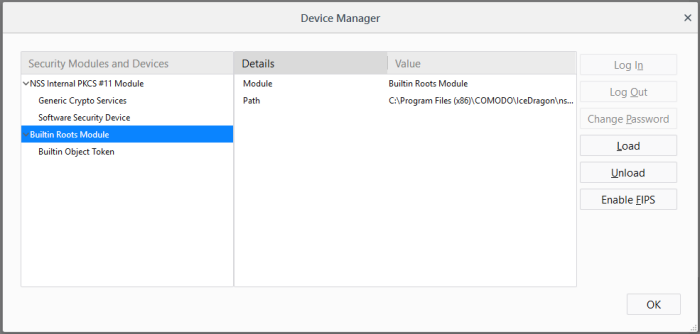
-
Select the security device and click 'Log In'
-
Enter the Master Password for the security device and click 'OK'
|
Note: You need to enter the Master Password for the browser to fetch the certificates and passwords. If you haven't set a Master Password please see the instructions on 'To set or change Password'. |
You will be logged-in to the security device so that the browser can access the certificates and the passwords stored by the security device.
-
To logout of the security device, click 'Log Out'
-
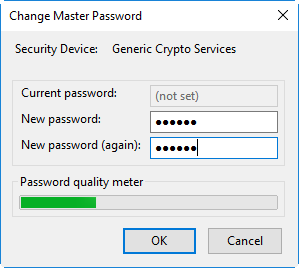
Select the security device and click 'Change Password'
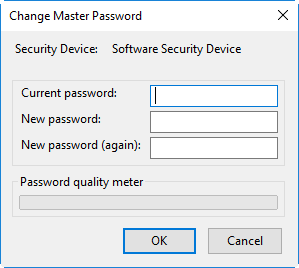
-
Enter your current password in the 'Current password' field. If you are setting the Master Password for the fist time, leave this field blank
-
Enter your new password, re-enter it for confirmation in the respective fields and click 'OK'.
If you want to use an external security device like a smart card, you need to first install the module software following the instructions that came with the security device. You may have to physically connect the device to the port specified in the instructions during installation. After installation:
- Click the hamburger/menu button at the top-right
- Select 'Options' > 'Privacy & Security' > scroll to the 'Certificates' then click 'Security Devices' button
- Click the 'Load' in the 'Device Manager' interface
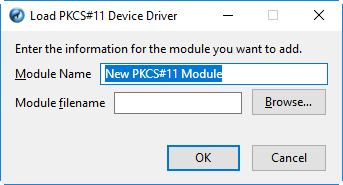
-
Enter a name for the new device in order fo the browser to identify it in the 'Module Name' field.
-
Enter the path of the module file you installed with the device in the 'Module filename' field.
- Alternatively, click 'Browse' and navigate to the location in your hard drive where you have installed the module and click 'Open'.
-
Click 'OK'.
Your new module will be loaded. You can set a password and login to the device for the browser to access the certificates and passwords stored by the new device.
-
To remove a module, select the module and click 'Unload'.
Federal Information Processing Standards Publications (FIPS PUBS) 140-1 is a US government standard for implementations of cryptographic modules - hardware or software that encrypts and decrypts data or performs other cryptographic operations (such as creating or verifying digital signatures).
All the encryption and decryption processes of Comodo IceDragon can be configured to adhere to FIPS PUBS 140-1 through the Device Manager interface.
- Click the hamburger/menu button at the top-right
- Select 'Options' > 'Privacy & Security' > in the 'Certificates', select 'Security Devices'
- Click 'Enable FIPS'.



