Configuration Change Logs
- Click 'Tasks' > 'Advanced Tasks' > 'View Logs'
OR
- Click ‘Logs’ in advanced view of the CIS home screen
- Select 'Configuration Changes' in the drop-down at upper-left
Configuration change logs are a record of changes to CIS settings.
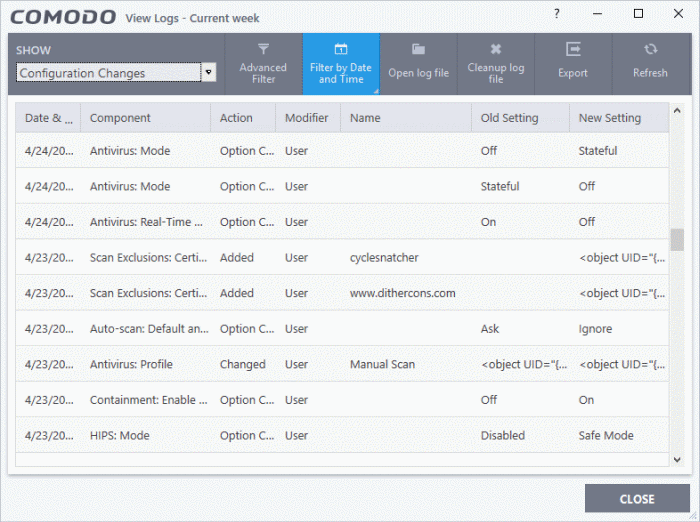
- Date & Time - When the configuration change was done.
- Component – The CIS interface that was modified.
- Action – Short description of the change made to the CIS component. For example, if a setting was changed, or an exclusion was created.
- Modifier - The service or user that made the change. Possible modifiers include 'User', 'Antivirus Alert', 'Auto-Learn', 'Firewall Alert', 'HIPS Alert', 'Containment Alert', 'Scheduler' and 'Comodo'.
- Name - The item featured in the modification. This will vary depending on the component.
- Old Setting - The value before the configuration change.
- New Setting - The value after the configuration change.
- Pace your mouse over an entry in the 'Old Value' or 'New Value' column to view the full setting string
Export - Save the logs as a HTML file. You can also right-click inside the
log viewer and choose 'Export'.
Open
log file - Browse to and view a saved log file.
Cleanup
log file - Delete the
selected event log.
Click any column header to sort the entries in ascending / descending order.



