Firewall Configuration
Click
'Settings' > 'Firewall'
- The firewall protects your computer against inbound and outbound threats
- It checks that all network traffic in and out of your computer is legitimate, hides your computer ports against hackers, and blocks software from transmitting your personal data over the internet
- The simple rules interface lets you specify exactly which applications can access the internet
- You can choose to receive alerts if the firewall detects suspicious activity, or have the firewall auto-implement a specific action
Configure the 'Firewall' module
- Click 'Settings' on the CIS home screen
- Click 'Firewall' on the left:
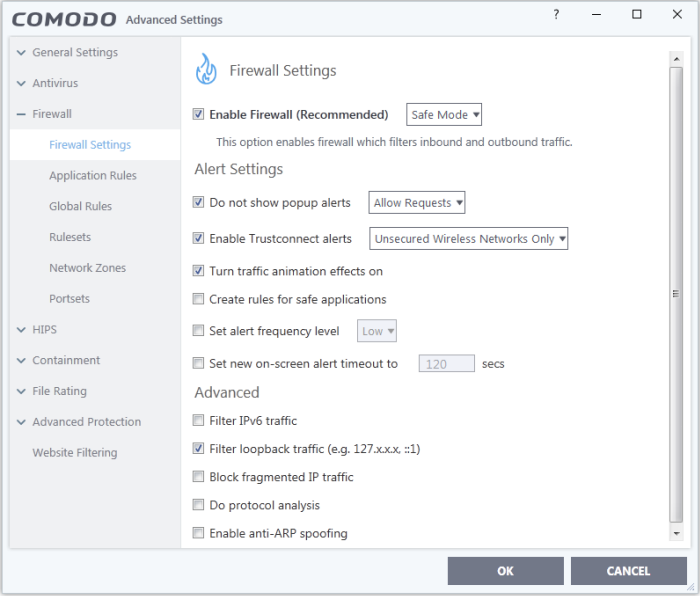
Firewall settings has the following sections:
- General Firewall Settings - Settings that govern the overall behavior of the firewall.
- Application Rules - Rules which control the network access rights of specific applications, or types of application.
- Global Rules - Rules which apply to all traffic flowing in and out of your computer.
- Rule Sets - Predefined collections of firewall rules that can be applied, out-of-the-box, to Internet capable applications such as browsers, email clients and FTP clients.
- Network Zones - Collections of rules that can be applied to internet capable applications like browsers and email/FTP clients.
- Portsets - Predefined groups of regularly used ports that can be used and reused when creating traffic filtering rules.
| Background note on rules: Both application rules and global rules are consulted when the firewall decides whether to allow or block a connection: Outgoing connections - Application rules are consulted first then global rules. Incoming connections - Global rules are consulted first then application rules. |



